Vulnerability Management Essentials
Overview of Vulnerability Management
The use of digital technologies across industries has increased security threats vastly. It’s rising the number of vulnerabilities corresponding with them. The inability of organizations to deal with these vulnerabilities raises security attacks. In this situation, a vulnerability management tool comes into the picture.
Without any delay, let us dwell on understanding ‘what is vulnerability?’.
What is vulnerability?
Vulnerability is the weakness within an organization’s devices that are prone to cyber-attacks. In addition, it poses an opportunity for hackers to invade the network. Open vulnerability will create a path for cyber-attacks. Hence, it affects the financial status and fame of the organization. One can expose these vulnerabilities with an efficient vulnerabilities management software
Why do we need to find vulnerabilities?
Vulnerabilities are critical security flaws in the network. Also, resolving these vulnerabilities is vital to prevent potential cyber-attacks. Moreover, a certain security assessment with a vulnerability assessment tool offers a clear idea about the risks in an organization.
Identifying and evaluating vulnerabilities is not a one-time process because new threats emerge daily. In addition, vulnerabilities with different severity levels pose different challenges to organizations. Therefore, identifying vulnerable assets is an ongoing process in an enterprise.
Now we know why we need to find vulnerabilities. Let us understand ‘what is vulnerability management?’
What is Vulnerability Management?
Vulnerability management definition:
Vulnerability management is a systematic and recurring process to identify and resolve vulnerabilities. The method comprises scanning, detecting, assessing, prioritizing, and remediating vulnerabilities. Likewise, these steps help to prevent security attacks in an enterprise.
We got an idea about ‘what is vulnerability management?’. Let us know more about its importance.
Importance of vulnerability management:
Vulnerabilities are the security gaps through which hackers can easily exploit any software application. Also, hackers always hunt for new and unpatched vulnerabilities. As a result, it is essential to have a robust vulnerability management tool. It aids to check the latest vulnerabilities and address them through several steps. It is not a one-time process but an ongoing process in the network.
Roadblocks to Vulnerability management:
Periodic Scans
Many enterprises rely on regular scans to identify threats that affect their operation. Note that the gap between the scans allows hackers to enter the network. Also, for rising vulnerabilities each day, regular vulnerability scanning is not enough to prevent them.Everyday scans are an effective way to find vulnerabilities. For early detection and remediation of vulnerabilities, ongoing scans are essential.
Manual scanning vs. Automated scanning:
Manual vulnerability scans are boring and tame. Thus, it makes security teams slow, leading to the periodic vulnerability scanning routine. Automated scans will help to overcome this challenge as it is more effective. With automation, you can schedule and run the scans every day. Also, automated scans run in the background without intervening with the user.
Inaccurate vulnerability detection
At times, vulnerability scanners are well-known for misreading scans. It results in reporting the vulnerabilities that do not exist. For assessing and remediating these vulnerabilities, there will be needless efforts. These are false positives and let down the whole process.
Lack of vulnerability prioritization
Vulnerability prioritization is vital before stepping into the process of remediation. An average enterprise finds a huge pile of cyber threats. Security teams are often confused about what vulnerability to address first. They tend to remediate them randomly. Thus, security teams focus their efforts on less critical ones. It will lead to missing the high-risk ones.
Prioritization based on CVSS
Vulnerability Prioritization helps in listing down the risks in the order of severity. This allows enterprises to deal with them in real-time to be secure and safe.CVSS determines the level of severity of the vulnerabilities. It helps to address the most critical vulnerable assets first. They are simple and accessible for prioritization. Additionally, CVSS scores map to a qualitative scale of low / medium / high/critical. From the vulnerability scale of 1 to 10, CVSS greater than seven to remediate at the earliest.
Dependence on CVE data to detect vulnerabilities
CVE is known as Common Vulnerabilities and Exposures. The data gives the lists of records publicly disclosing security flaws in systems. CVEs serve to standardize each vulnerability or exposure. Despite this, this is not the same for all vulnerabilities. But, a lot of vulnerabilities persist without CVE data.Vulnerabilities without CVEs are those which are old enough to be unexposed by vulnerability scanning. At times, non-CVE vulnerabilities do not turn up even after their exposure. Hence, it is essential to know that a large number of vulnerabilities do not have CVE.
Thus, CVE data is not enough to detect vulnerabilities. IT admins need to make use of an extensive vulnerability database while resolving any issues. It has to detect all the vulnerabilities, irrespective of CVE data. Further, the vulnerability database should support vulnerabilities beyond CVE data.
Delay in vulnerability detection and remediation
Many enterprises achieve vulnerability scans and detection, but lag in remediating them. As we saw above in the vulnerability management definition, the step is incomplete without remediation. This plot leads to security gaps and creates an open window for hackers. Hence, we need to remediate the issues instantly. Accordingly, your vulnerability management tool must come with an integrated patch management solution. It enables faster remediation from the same console.
Bulky reports for analysis
Vulnerability management is an ongoing process. It includes four major steps, and they are:a. Scanning
b. Detection
c. Prioritization
d. RemediationThe accurate gauging of these steps is vital to know if the process is going correctly. Hard-to-read and bulk reports do not help and make it challenging during analysis. Hence, reports must be clear and insightful to record all activities. Auto-generated and customizable reports help to gain needed insights.
Let us learn ‘what is vulnerability manager?’ and what it does?
What is a vulnerability manager?
In the previous section, we already saw about “what is vulnerability”. A vulnerability manager takes care of each step of managing vulnerabilities. Enterprises use vulnerability management software to perform the following steps:
1. Scan
2. Detect
3. Assess
4. Prioritize
5. Remediate
How does SanerNow Vulnerability Manager help you implement effective vulnerability management?
SecPod’s SanerNow vulnerability manager enables enterprises to manage vulnerabilities. SanerNow offers the industry’s fastest vulnerability scanning techniques to detect security vulnerabilities. It provides a continuous approach to detect, assess, prioritize, and remediate vulnerabilities.
SanerNow offers a centralized cloud-based console to manage vulnerabilities remotely. Furthermore, it leverages the home-grown world’s largest SCAP feed with 175,000+ security checks. The latest vulnerabilities are updated in the SCAP feed regularly.
SanerNow’s integrated patch management tool allows us to remediate vulnerable assets at a faster rate. SanerNow also automates end-to-end vulnerability management.
We will begin to understand the architecture of SanerNow Vulnerability Management.
SanerNow Vulnerability Management Architecture:
SecPod SanerNow works on a cloud-based, single agent, and single server model.
SanerNow Centralized Server:
SanerNow server can be hosted on both cloud and on-premises. Also, it is in sync with the in-built SCAP feed to get the latest vulnerability information. This information aids in the accurate detection of any security issues. Additionally, a web-based graphical user interface supports the SanerNow server. You can manage your tasks from SanerNow’s user-friendly interface.
SanerNow Multifunctional Agent:
A multifunctional agent in the organization’s endpoints executes the vulnerability management tasks. You can set the agent in a live connection with the server. Consequently, this will help to perform on-demand tasks. The agents installed in the endpoints execute all tasks from scanning to remediation. This agent also takes up the role of a network scanner to scan other devices in the network. It saves investments in extra hardware.
SecPod SCAP Feed:
The architecture consists of the world’s most extensive SCAP feed. It has 175,000+ security checks with all the vulnerability information. Within 24 hours of vulnerability disclosure, the information is updated in the database. Also, SecPod offers a natural language-based search interface to take out security information easily. It has gained the trust of other vendors to give accurate details of Software vulnerabilities.
Key Features of SanerNow Vulnerability Management:
Rapid and continuous vulnerability scanning
SanerNow has an intelligence-augmented and efficient scanning algorithm. With this, you can scan and detect vulnerabilities in your devices in less than five minutes. You can also schedule and automate these scans and perform an ongoing vulnerability discovery.It facilitates running on-demand and real-time vulnerability scanning across your network devices. It supports the world’s largest vulnerability database with accurate detection.
SanerNow leverages the home-grown and world’s largest vulnerability database with 175,000+ security checks. Besides, the database will be up-to-date with the latest vulnerability information.
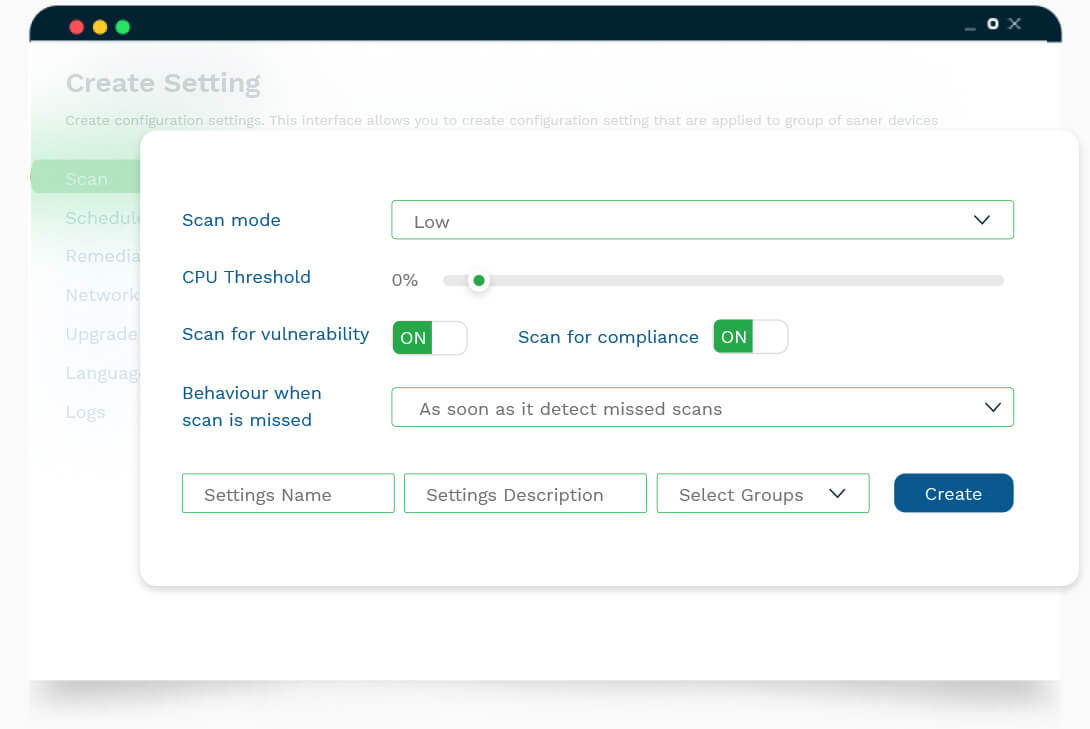
Predictive analysis of risk and probability assessment of vulnerability exploits
SanerNow assesses the vulnerability risks and provides the potential exploit details. With this, you can save your network from adverse impact. Also, you can take needed actions on the vulnerabilities with recorded recurrence knowledge.
A cloud-based solution for a perimeter-less world
SanerNow provides a centralized and cloud-based console to help you manage vulnerabilities remotely. Given that, you can easily manage the vulnerabilities across your distributed workforce with SanerNow vulnerability management platform.
Integrated vulnerability detection and patch remediation
SanerNow offers an integrated patch management solution to remediate the detected vulnerabilities. Integrated patching helps in faster remediation and eliminating the security gaps. Further, you can perform all tasks from detection to remediation from one console.
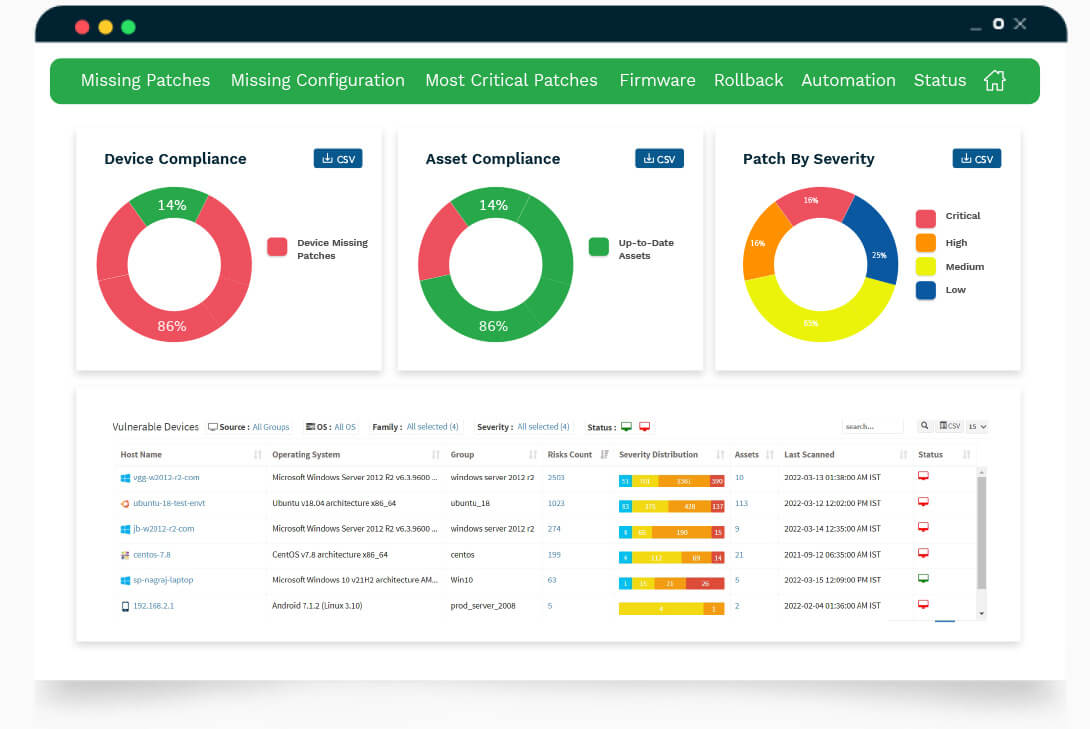
SanerNow supports patches for all operating systems. You can deploy patches on Windows, MAC, and Linux. SanerNow also supports patching for 300+ third-party applications.
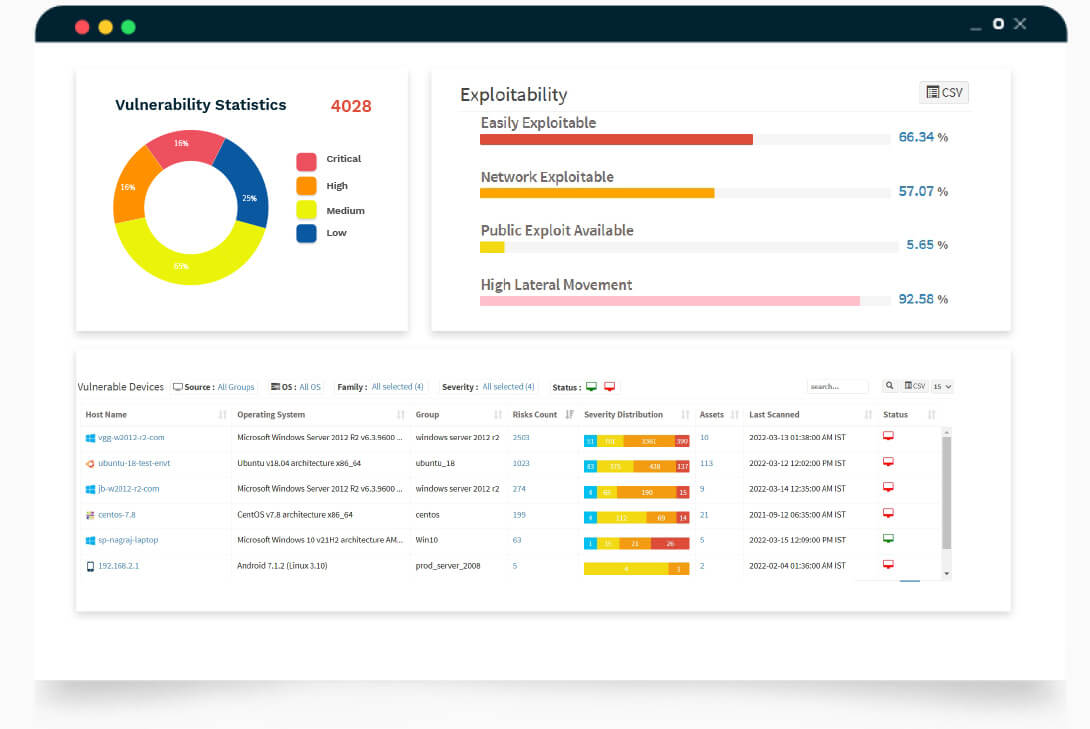
Accurate prioritization with high-risk vulnerability identification
SanerNow accurately prioritizes the identified vulnerabilities based on the CVSS scores. Also, with intact prioritization, admins can first focus on remediating the high-risk vulnerabilities. Later, they can plan an intelligent vulnerability remediation strategy.
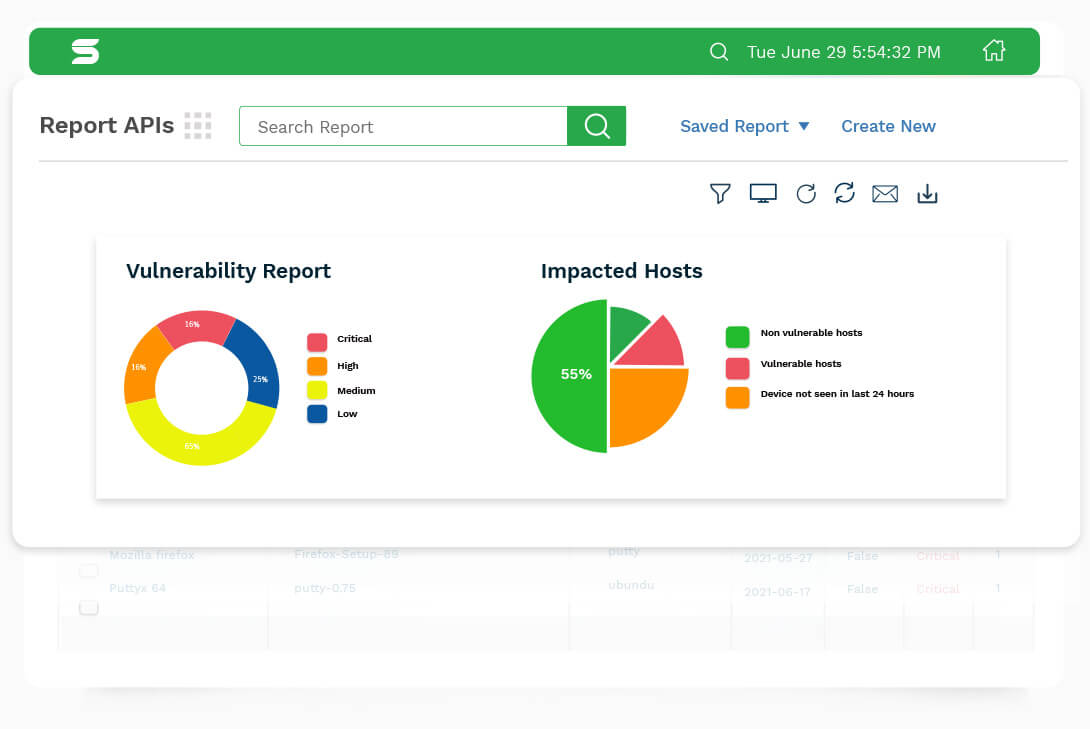
Comprehensive reports with customizations
SanerNow provides insightful and customizable reports. You can quickly evaluate your vulnerability details and management tasks with these reports. You can also automate these reports and schedule them in your mailbox.
360-degree visibility with insightful dashboards
SanerNow provides a user-friendly and insightful dashboard to manage vulnerabilities. You can quickly check different vulnerabilities grouping and set tasks. Moreover, the actionable dashboard makes the whole process simple and effective.
Why Choose SanerNow Vulnerability Management?
Fastest scan within five minutes
Scan and discover vulnerabilities across your devices in less than five minutes. SanerNow supports the industry’s fastest, most comprehensive, and ongoing vulnerability scanner.
Accurate detection powered by the largest SCAP repository.
SanerNow leverages the in-built world’s largest SCAP repository with 175,000+ vulnerability checks. Furthermore, extensive security checks aid in the accurate detection of vulnerabilities.

Integrated Patch Management
SanerNow provides an integrated patch management solution to remediate vulnerabilities instantly. Thus, you can execute all tasks from detection to remediation in one place.
Cloud-Based server
SanerNow provides a centralized, cloud-based console to manage vulnerabilities remotely. Also, you can easily manage vulnerabilities across your hybrid workforce using SanerNow.
End-to-end Automation
You can automate the end-to-end tasks from vulnerability detection, assessment to vulnerability remediation with SanerNow. In addition, you can schedule these tasks according to your organization’s requirements.
In this article, we saw in detail “What is vulnerability management platform”. With SanerNow manage vulnerability at ease. Schedule a demo to see SanerNow in action.
Contents
Overview of Vulnerability Management
The use of digital technologies across industries has increased security threats vastly. It’s rising the number of vulnerabilities corresponding with them. The inability of organizations to deal with these vulnerabilities raises security attacks. In this situation, a vulnerability management solution comes into the picture.
Without any delay, let us dwell on understanding ‘what is vulnerability?’.
What is vulnerability?
Vulnerability is the weakness within an organization’s devices that are prone to cyber-attacks. In addition, it poses an opportunity for hackers to invade the network. Open vulnerability will create a path for cyber-attacks. Hence, it affects the financial status and fame of the organization.
Why do we need to find vulnerabilities?
Vulnerabilities are critical security flaws in the network. Also, resolving these vulnerabilities is vital to prevent potential cyber-attacks. Moreover, a certain security assessment with a vulnerability assessment tool offers a clear idea about the risks in an organization.
Identifying and evaluating vulnerabilities is not a one-time process because new threats emerge daily. In addition, vulnerabilities with different severity levels pose different challenges to organizations. Therefore, identifying vulnerable assets is an ongoing process in an enterprise.
Now we know why we need to find vulnerabilities. Let us understand ‘what is vulnerability management?’
What is Vulnerability Management?
Vulnerability management definition:
Vulnerability management system definition says that it is a systematic and recurring process to identify and resolve vulnerabilities. The method comprises scanning, detecting, assessing, prioritizing, and remediating vulnerabilities. Likewise, these steps help to prevent security attacks in an enterprise.
We got an idea about ‘what is vulnerability management?’. Let us know more about its importance.
Importance of vulnerability management:
Vulnerabilities are the security gaps through which hackers can easily exploit any software application. Also, hackers always hunt for new and unpatched vulnerabilities. As a result, it is essential to have a robust vulnerability management platform. It aids to check the latest vulnerabilities and address them through several steps. It is not a one-time process but an ongoing process in the network.
Roadblocks to Vulnerability management:
Periodic Scans
Many enterprises rely on regular scans to identify threats that affect their operation. Note that the gap between the scans allows hackers to enter the network. Also, for rising vulnerabilities each day, regular vulnerability scanning is not enough to prevent them.Everyday scans are an effective way to find vulnerabilities. For early detection and remediation of vulnerabilities, ongoing scans are essential.
Manual scanning vs. Automated scanning:
Manual vulnerability scans are boring and tame. Thus, it makes security teams slow, leading to the periodic vulnerability scanning routine. Automated scans will help to overcome this challenge as it is more effective. With automation, you can schedule and run the scans every day. Also, automated scans run in the background without intervening with the user.
Inaccurate vulnerability detection
At times, vulnerability scanners are well-known for misreading scans. It results in reporting the vulnerabilities that do not exist. For assessing and remediating these vulnerabilities, there will be needless efforts. These are false positives and let down the whole process.
Lack of vulnerability prioritization
Vulnerability prioritization is vital before stepping into the process of remediation. An average enterprise finds a huge pile of cyber threats. Security teams are often confused about what vulnerability to address first. They tend to remediate them randomly. Thus, security teams focus their efforts on less critical ones. It will lead to missing the high-risk ones.
Prioritization based on CVSS
Vulnerability Prioritization helps in listing down the risks in the order of severity. This allows enterprises to deal with them in real-time to be secure and safe.CVSS determines the level of severity of the vulnerabilities. It helps to address the most critical vulnerable assets first. They are simple and accessible for prioritization. Additionally, CVSS scores map to a qualitative scale of low / medium / high/critical. From the vulnerability scale of 1 to 10, CVSS greater than seven to remediate at the earliest.
Dependence on CVE data to detect vulnerabilities
CVE is known as Common Vulnerabilities and Exposures. The data gives the lists of records publicly disclosing security flaws in systems. CVEs serve to standardize each vulnerability or exposure. Despite this, this is not the same for all vulnerabilities. But, a lot of vulnerabilities persist without CVE data.Vulnerabilities without CVEs are those which are old enough to be unexposed by vulnerability scanning. At times, non-CVE vulnerabilities do not turn up even after their exposure. Hence, it is essential to know that a large number of vulnerabilities do not have CVE.
Thus, CVE data is not enough to detect vulnerabilities. IT admins need to make use of an extensive vulnerability database while resolving any issues. It has to detect all the vulnerabilities, irrespective of CVE data. Further, the vulnerability database should support vulnerabilities beyond CVE data.
Delay in vulnerability detection and remediation
Many enterprises achieve vulnerability scans and detection, but lag in remediating them. As we saw above in the vulnerability management definition, the step is incomplete without remediation. This plot leads to security gaps and creates an open window for hackers. Hence, we need to remediate the issues instantly. Accordingly, your vulnerability management tool must come with an integrated patch management solution. It enables faster remediation from the same console.
Bulky reports for analysis
Vulnerability management is an ongoing process. It includes four major steps, and they are:a. Scanning
b. Detection
c. Prioritization
d. RemediationThe accurate gauging of these steps is vital to know if the process is going correctly. Hard-to-read and bulk reports do not help and make it challenging during analysis. Hence, reports must be clear and insightful to record all activities. Auto-generated and customizable reports help to gain needed insights.
Let us learn ‘what is vulnerability manager?’ and what it does?
What is a vulnerability manager?
In the previous section, we already saw about “what is vulnerability”. A vulnerability manager takes care of each step of managing vulnerabilities. Enterprises use these vulnerability management tools to perform the following steps:
1. Scan
2. Detect
3. Assess
4. Prioritize
5. Remediate
How does SanerNow Vulnerability Manager help you implement effective vulnerability management?
SecPod’s SanerNow vulnerability manager enables enterprises to manage vulnerabilities. SanerNow offers the industry’s fastest vulnerability scanning techniques to detect security vulnerabilities. It provides a continuous approach to detect, assess, prioritize, and remediate vulnerabilities.
SanerNow offers a centralized cloud-based console to manage vulnerabilities remotely. Furthermore, it leverages the home-grown world’s largest SCAP feed with 160,000+ security checks. The latest vulnerabilities are updated in the SCAP feed regularly.
SanerNow’s integrated patch management tool allows us to remediate vulnerable assets at a faster rate. SanerNow also automates end-to-end vulnerability management.
We will begin to understand the architecture of SanerNow Vulnerability Management.
SanerNow Vulnerability Management Architecture:
SecPod SanerNow works on a cloud-based, single agent, and single server model.
SanerNow Centralized Server:
SanerNow server can be hosted on both cloud and on-premises. Also, it is in sync with the in-built SCAP feed to get the latest vulnerability information. This information aids in the accurate detection of any security issues. Additionally, a web-based graphical user interface supports the SanerNow server. You can manage your tasks from SanerNow’s user-friendly interface.
SanerNow Multifunctional Agent:
A multifunctional agent in the organization’s endpoints executes the vulnerability management tasks. You can set the agent in a live connection with the server. Consequently, this will help to perform on-demand tasks. The agents installed in the endpoints execute all tasks from scanning to remediation. This agent also takes up the role of a network scanner to scan other devices in the network. It saves investments in extra hardware.
SecPod SCAP Feed:
The architecture consists of the world’s most extensive SCAP feed. It has 160,000+ security checks with all the vulnerability information. Within 24 hours of vulnerability disclosure, the information is updated in the database. Also, SecPod offers a natural language-based search interface to take out security information easily. It has gained the trust of other vendors to give accurate details of Software vulnerabilities.
Key Features of SanerNow Vulnerability Management:
Rapid and continuous vulnerability scanning
SanerNow has an intelligence-augmented and efficient scanning algorithm. With this, you can scan and detect vulnerabilities in your devices in less than five minutes. You can also schedule and automate these scans and perform an ongoing vulnerability discovery.It facilitates running on-demand and real-time vulnerability scanning across your network devices. It supports the world’s largest vulnerability database with accurate detection.
SanerNow leverages the home-grown and world’s largest vulnerability database with 160,000+ security checks. Besides, the database will be up-to-date with the latest vulnerability information.

Predictive analysis of risk and probability assessment of vulnerability exploits
SanerNow assesses the vulnerability risks and provides the potential exploit details. With this, you can save your network from adverse impact. Also, you can take needed actions on the vulnerabilities with recorded recurrence knowledge.
A cloud-based solution for a perimeter-less world
SanerNow provides a centralized and cloud-based console to help you manage vulnerabilities remotely. Given that, you can easily manage the vulnerabilities across your distributed workforce with SanerNow vulnerability management platform.
Integrated vulnerability detection and patch remediation
SanerNow offers an integrated patch management solution to remediate the detected vulnerabilities. Integrated patching helps in faster remediation and eliminating the security gaps. Further, you can perform all tasks from detection to remediation from one console.

SanerNow supports patches for all operating systems. You can deploy patches on Windows, MAC, and Linux. SanerNow also supports patching for 300+ third-party applications.
Accurate prioritization with high-risk vulnerability identification
SanerNow accurately prioritizes the identified vulnerabilities based on the CVSS scores. Also, with intact prioritization, admins can first focus on remediating the high-risk vulnerabilities. Later, they can plan an intelligent vulnerability remediation strategy.

Comprehensive reports with customizations
SanerNow provides insightful and customizable reports. You can quickly evaluate your vulnerability details and management tasks with these reports. You can also automate these reports and schedule them in your mailbox.

360-degree visibility with insightful dashboards
SanerNow provides a user-friendly and insightful dashboard to manage vulnerabilities. You can quickly check different vulnerabilities grouping and set tasks. Moreover, the actionable dashboard makes the whole process simple and effective.
Why Choose SanerNow Vulnerability Management?
Fastest scan within five minutes
Scan and discover vulnerabilities across your devices in less than five minutes. SanerNow supports the industry’s fastest, most comprehensive, and ongoing vulnerability scanner.
Accurate detection powered by the largest SCAP repository.
SanerNow leverages the in-built world’s largest SCAP repository with 160,000+ vulnerability checks. Furthermore, extensive security checks aid in the accurate detection of vulnerabilities.

Integrated Patch Management
SanerNow provides an integrated patch management solution to remediate vulnerabilities instantly. Thus, you can execute all tasks from detection to remediation in one place.
Cloud-Based server
SanerNow provides a centralized, cloud-based console to manage vulnerabilities remotely. Also, you can easily manage vulnerabilities across your hybrid workforce using SanerNow.
End-to-end Automation
You can automate the end-to-end tasks from vulnerability detection, assessment to vulnerability remediation with SanerNow. In addition, you can schedule these tasks according to your organization’s requirements.
In this article, we saw in detail “What is vulnerability management platform”. With SanerNow manage vulnerability at ease. Schedule a demo to see SanerNow in action.


