Vulnerability Management Essentials
What is Vulnerability Management Lifecycle?
A cyber security plan includes vulnerability identification, detection, prioritization, and remediation with a vulnerability management software. The mitigation of these flaws will keep the enterprise safe and secure. The vulnerability management lifecycle ensures and verifies the enterprise is not at risk.
Let us know about vulnerability. It goes around three ways. Firstly, the system flaws, secondly, the hacker’s access to system flaws, and thirdly, the hacker’s ability to exploit the flaws.
This article will focus on SanerNow’s vulnerability management life cycle.
Stages of the vulnerability management lifecycle
The following diagram will depict the SanerNow vulnerability management lifecycle.
Find the description of the vulnerability manager lifecycle below:
Rapid scanning
Scanning is the first stage of the vulnerability management lifecycle. SecPod SanerNow provides a continuous and automatic vulnerability scanning tool. It has an intelligence-augmented and efficient scanning algorithm. You can scan and detect vulnerabilities in less than five minutes. With this, you can schedule the scans and rest back where SanerNow will work in the background without interrupting the user. It also facilitates ongoing vulnerability management platform discovery and on-demand accurate scans across your endpoints and network.
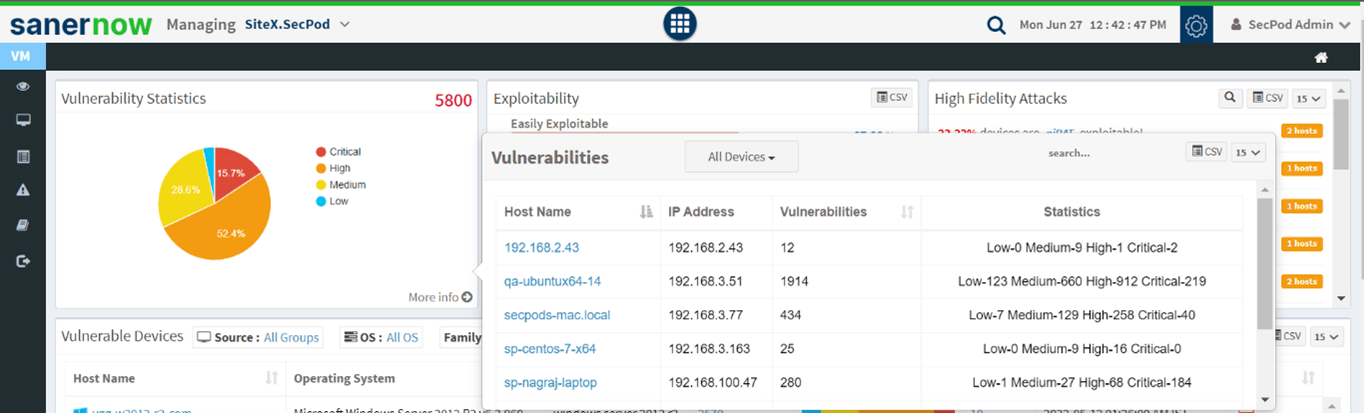
Accurate detection
SecPod SanerNow provides precise detection of flaws in the network. The lightweight agents in the endpoints will monitor the devices, and with limited resources and low bandwidth, it detects multiple risks. SanerNow supports the world’s largest vulnerability database with 175,000+ security checks, and the latest vulnerability information will aid in precise detection.
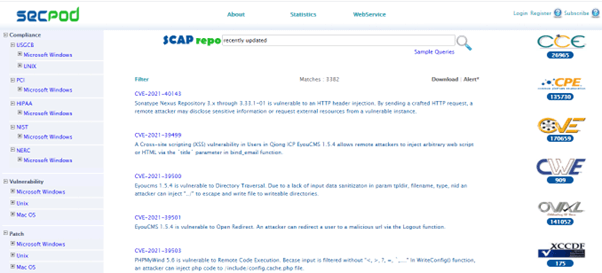
Rigorous assessment
SecPod SanerNow facilitates rigorous assessments in various methods. A precise analysis of each flaw will be based on CVSS scores, risk-based assessments, and predictive analysis. CVSS scores range from 1 to 10, with 10 indicating high severity. In risk-based assessments, SanerNow vulnerability remediation is based on the level of severity it poses to an enterprise. Also, predictive analysis of risk provides the potential exploit details. So, you can take action on vulnerabilities with recorded recurrence knowledge. Rigorous assessment is a crucial stage in vulnerability lifecycle management.
Predictive prioritization
SecPod SanerNow detects ongoing exploits in the devices. Security teams cannot just randomly mitigate every threat. So there is a need for prioritization of the flaws. SanerNow prioritizes these vulnerabilities based on their severity. As discussed previously, CVSS scores will help security teams prioritize them and remediate the most critical vulnerabilities first. It’s a calculated risk assessment that will quickly help any enterprise deal with flaws.

Instant remediation
SecPod SanerNow comes up with an integrated patch management software module to serve as a right fit in the vulnerability management lifecycle. It will help in the quick vulnerability remediation of flaws soon after detection. It also reduces the security gap where an enterprise takes a lot of time to mitigate flaws, leading to greater exploitation. These patches are compatible with the relevant flaws. This comprehensive patch remediation supports multiple OSs like Windows, Linux, MAC, and other third-party applications.
Custom reports
SecPod SanerNow provides comprehensive reports with customization. You will get actionable insights on vulnerability details. These reports will help enterprises to plan and deal with emerging vulnerabilities. They also help monitor each step in your vulnerability lifecycle management.
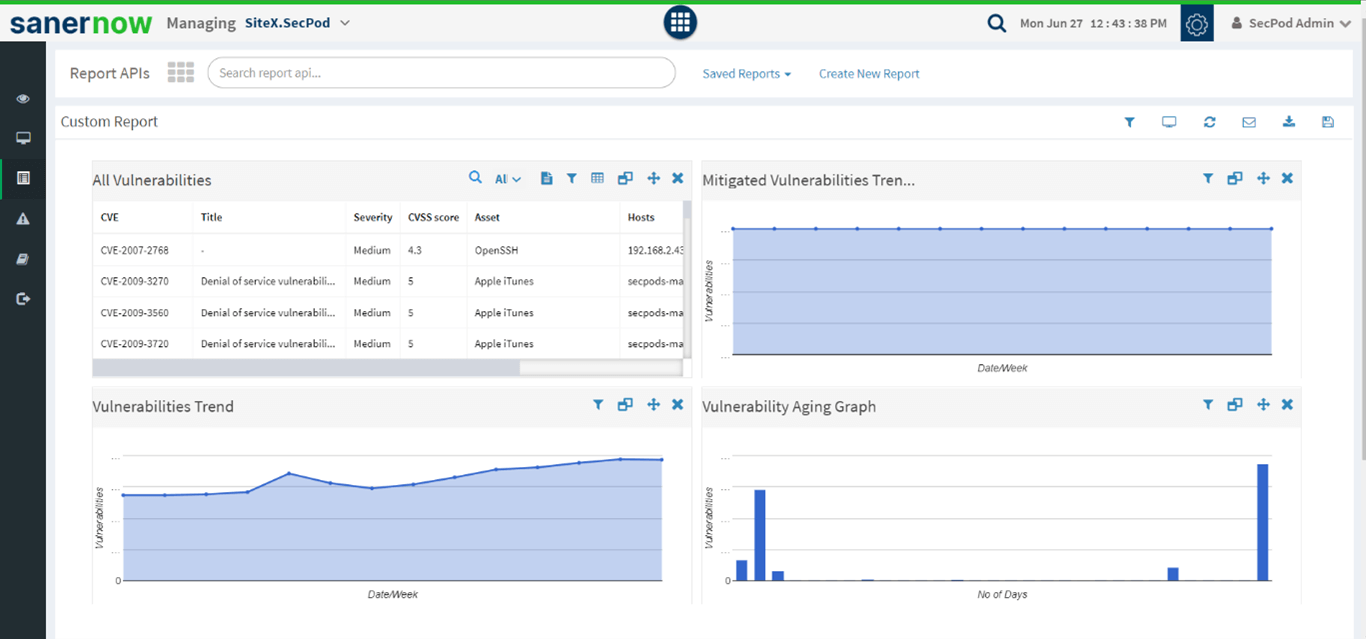
Therefore, a robust vulnerability management software is vital to deal with upcoming threats. Also, mitigation of risks must be prompt and timely to avoid cyber-crime


