SanerNow for IT and ITES
Continuous Security and Compliance
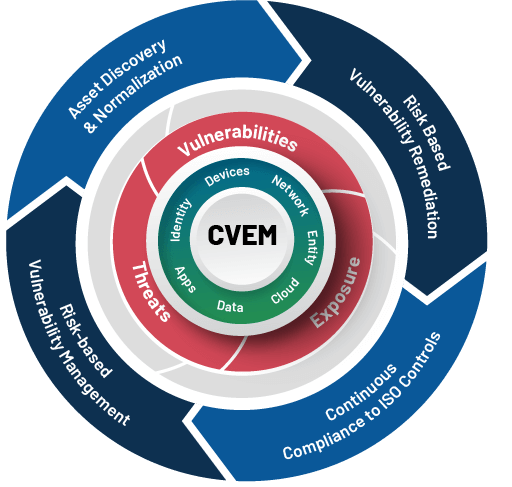
Achieve continuous ISO compliance, automate risk detection and remediation with unified vulnerability management.

Best value in vulnerability and patch management
High-quality vulnerability & patch management solutions seemed expensive solutions from Qualys and Tenable. Thankfully we found high quality & affordable alternative with SecPod’s SanerNow.
– Norm Messenger, Chief Security Officer, Inspirage





Leverage the Benefits Designed for You
Provide uninterrupted service without any disruption
Protect sensitive data with proactive cyberattack prevention
Achieve Continuous Compliance with ISO and Standard Regulations
Enable Business Continuity and Align IT Security Goals
Reduce risk, improve efficiency, and increase cost-effectiveness
SanerNow for IT & ITES Organizations
Understand how SanerNow Continuous Vulnerability & Exposure Management can protect IT & ITES organizations from devastating cyberattacks
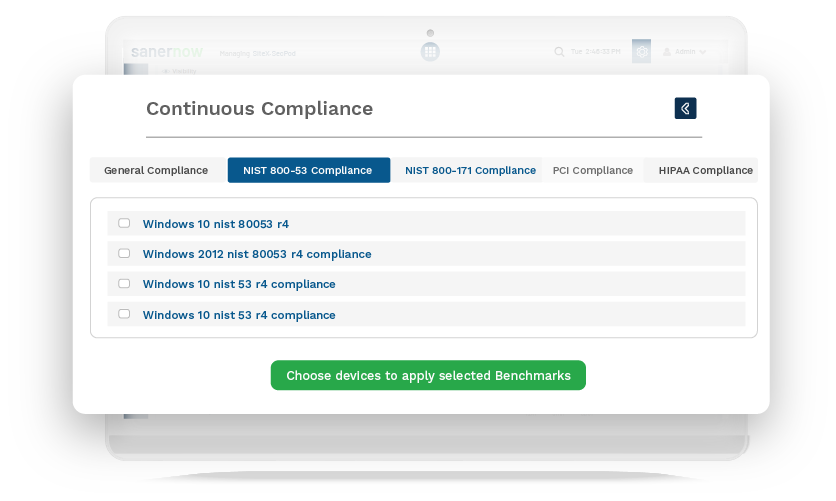
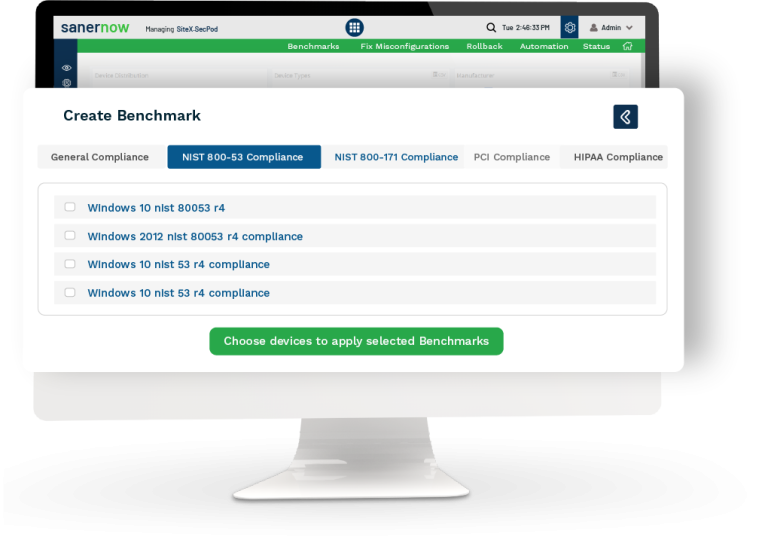
Continuously Adhere to ISO and Other Security Compliances
ISO compliance is critical for IT and ITES organizations looking to secure their IT. SanerNow supports PCI, HIPAA, NIST, ISO, and custom policies to safeguard your network and endpoints.
Identify non-compliant devices to enforce compliance
Harden devices with integrated patching and secure it
Implement real-time scanning for continuous compliance
Generate audit-ready reports anytime, anywhere!
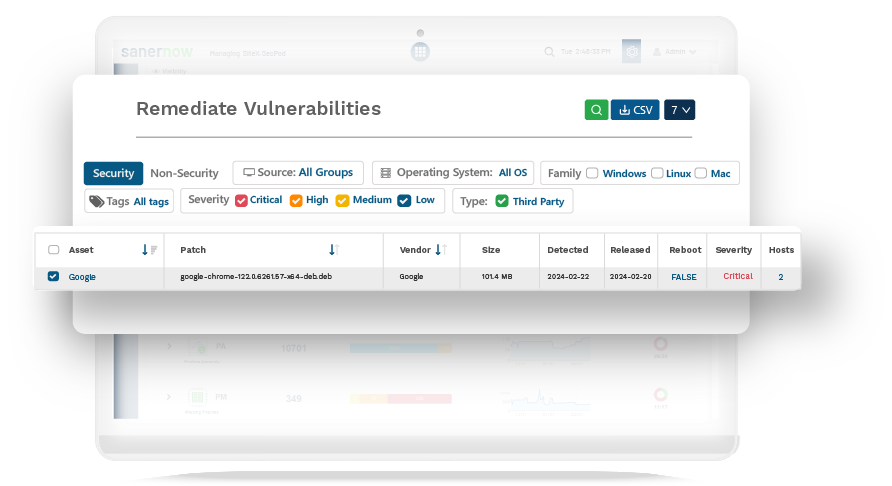
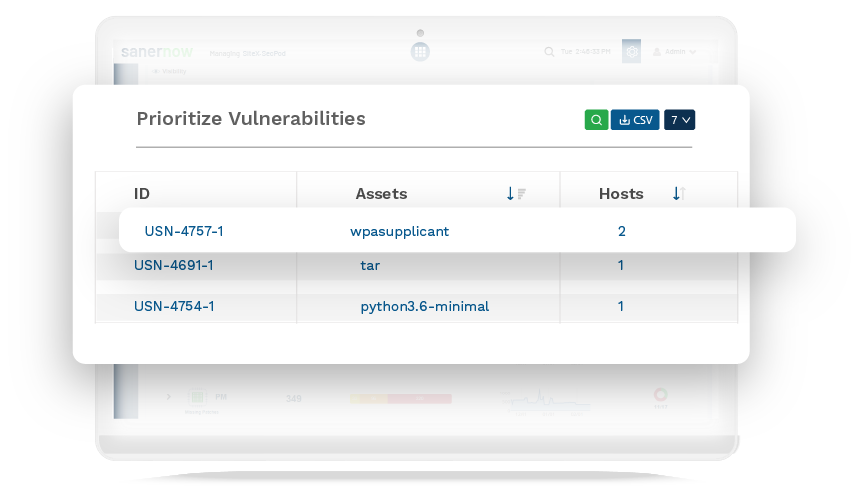
Swiftly Detect and Patch Security Risks Beyond CVEs
A tiny window of an open vulnerability is enough to lead to a cyberattack and interrupt your services. SanerNow helps you detect vulnerabilities immediately and patch them without any delay to reduce attack surfaces. Implement and automate all basic cyber hygiene measures easily with SanerNow.
Automations for all vulnerability management stages
Rapid patch support for all major OSs in Windows, MAC, Linux, and 450+ third-party applications
Combat vulnerabilities, misconfigurations, posture anomalies and other security risks
Normalize and Secure Remote Devices in a Unified Console
Unnecessary IT anomalies in your network can be devastating, remote, or otherwise. Declutter and normalize your network by eliminating the obvious risks. Monitor endpoint metrics, manage endpoint health, perform bulk software deployment, and strengthen your security posture from the cloud.
Reduce attack surface by eliminating unnecessary risk in your network, remote or otherwise
Real-time monitoring of 100+ security controls to keep system health in check
Strong security controls to protect all devices
HIGHLIGHTED CASE STUDY
Leading Video Surveillance Software Manufacturer Unifies Vulnerability Management to Achieve SOC 2, Type 2 Compliance
A Leading Cloud Video Surveillance Software
Manufacturer was in desperate need of a unified vulnerability management solution to handle their decentralized network and achieve SOC 2, Type 2 compliance.
Solutions Covering End-to-End Cyberattack Prevention Use Cases
Continuously Comply with ISO and Prevent Cyberattacks
Get a personalised demo of the platform and solutions.



