Saner Continuous Vulnerability & Exposure Management
Detect, Defend, and Defeat Vulns from Start to Finish!
Achieve complete attack surface reduction with a smart, swift, and efficient risk management
Trusted by
Trusted by
Saner CVEM
Your Go-To Superpower for Effortless, Automated,
and Continuous Vulnerability and Exposure Management!
Saner CVEM Vulnerability Management software is built for your modern enterprise to fight the growing risk landscape with advanced capabilities to scan, assess, prioritize, and remediate vulnerabilities on devices.
Differentiators
Manage Vulnerabilities, Exposures and Other Security Risks in a Single Unified Platform
Mitigate risks with extensive scans based on our homegrown, industry-renowned SCAP feed with over 190,000 risk checks. Moreover, the checks are updated daily with the latest vulnerability info to achieve accurate detection.
Mitigate Vulnerabilities On-Time with Integrated Remediation
Assess and fix vulnerabilities from a single console. Use patching and other security controls to reduce risks effectively.
Experience the Leading Edge of Security Innovation
Gain holistic IT visibility and detect outliers effectively. Utilize innovative security methods like machine learning and statistical analysis.
Automate End-to-End Tasks and Establish a Continuous Routine
Automate all tasks from scanning to remediation. Maintain a continuous routine for managing vulns and security risks.
Transform Enterprise Security with Saner CVEM
Before Saner CVEM
After Saner CVEM
Visualize & Normalize
Detect & Prioritize
Remediate & Mitigate
The Software that is Sleek, Simple, yet the Most Powerful
Manual patching cycles are tedious and time-consuming. With the Saner automated patch management tool, configure end-to-end workflows for automatic patching and fix risks faster than ever. Schedule automated patching tasks and make patching a hands-free task. It also supports the upload of pre and post-remediation scripts.
Applying new patches directly to the production environment is risky. Saner patch management software enables you to create a test environment to test the new patches to verify compatibility. Later, deploy the approved patches across the devices in your production environment and prevent any disruptions and productivity errors.
Saner auto patching software is an ideal solution for hybrid workforces. You can easily deploy patches across globally distributed devices from a centralized cloud patch management solution. Furthermore, all the patching tasks, from scanning to deployment, are executed by a single lightweight multifunctional agent installed in the endpoints. You can also go for the agent-less option, which is a unique approach to scanning while retaining the scan speed and accuracy.
Saner auto patching tool thoroughly assesses the patches and prioritizes them based on their business context, technical impact, severity level, and more intelligence to help focus on critical patches immediately. Additionally, you can deploy these patches quickly to reduce risk exposure and plan your remediation efforts wisely.
As important as the software application patches, firmware patches are critical to tightening IT security. Moreover, it is recommended to include firmware patching as you establish your automated patch management cadence to reduce security risk exposure. Saner patch manager supports patching for firmware updates to fix issues and errors in firmware.
Every organization has a different structure, and generalizing business impact reduces the efficacy of risk prioritization. Saner Risk Prioritization can configure and customize risk prioritization based on your organization’s structure and calculate the business impact to tailor-make risk prioritization and significantly reduce the attack surface.
Saner patch management tool supports multi-platform patching for all major operating systems like windows, macOS, linux, and 550+ third-party applications. SanerNow’s automated patching solution additionally maintains a pre-built patch repository for third-party application patches.
Patch rollback is made easier with the Saner automated patch management tool to avoid disruptions in business operations. It rollbacks the last stable version with zero downtime and a single click to easily deal with incompatible and error-prone software patches.
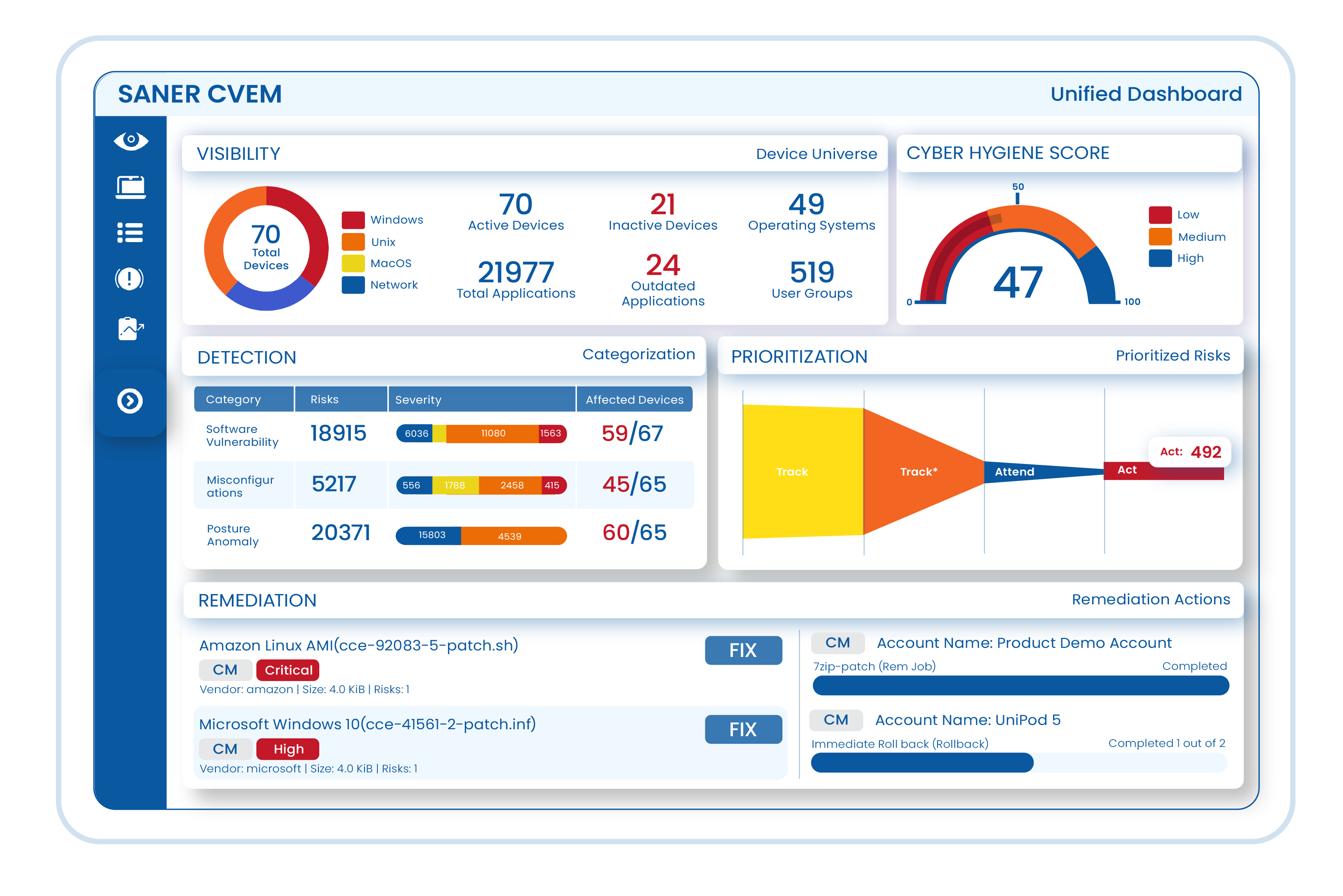
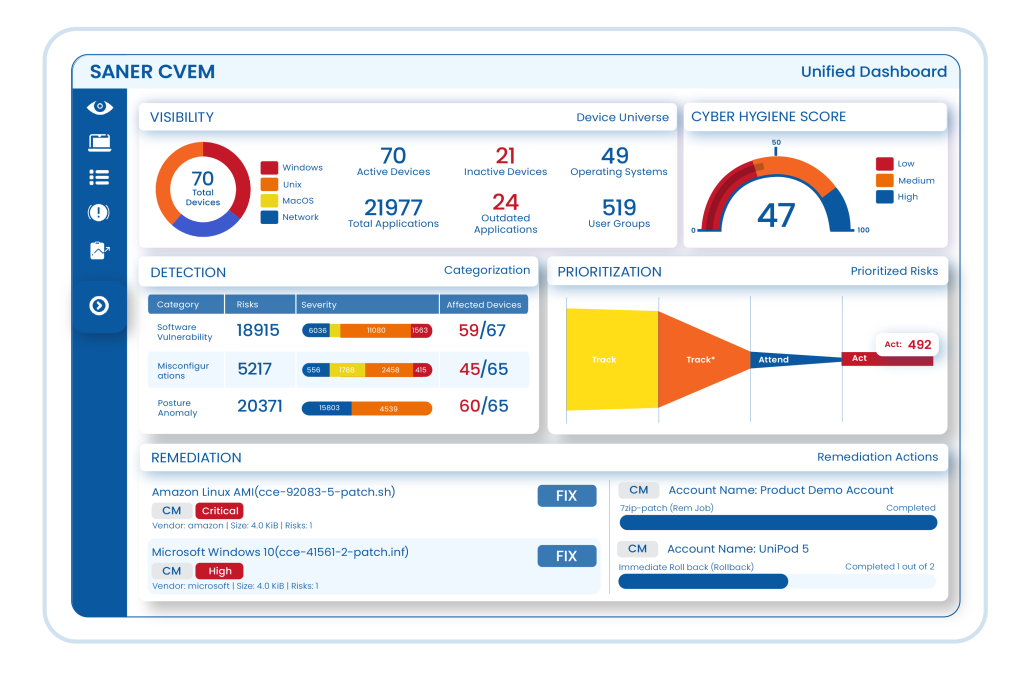
Keep an eye on all your IT all the time
Keep track of every piece of hardware and software in your network using one dashboard. Decide which asset is okay, and which isn’t.Ensure Cyber Safety with broad awareness
Know your IT system inside out and fix anything unusual. Find and remove obvious risk factors promptly.Find Vulns and fix them quickly
Respond quickly to threats by scanning continuously to find and fix vulnerabilities in your company’s IT. Use the world’s largest vulnerability database with 190,000+ security checks.Prioritize Security Risks
Our SSVC-based framework, the world’s first, uses unique algorithms to prioritize security risks based on business context, exploit potential, automation feasibility, and more.Achieve Compliance with Regulatory Standards
Harden your system configurations to reduce your threat exposure. Remotely scan and address any vulnerable or deviant devices to proactively remediate risks.Patch OSs and Third Party Applications
Stay up to date with your patching across your hybrid heterogeneous infrastructure and assets. Ensure minimal risk with a fast-to-market, fully tested, and automated remote patching.Keep your systems safe with 100+ security checks
Watch over and manage your devices to make them stronger against attacks. Keep an eye on over 100 different things like threats, software updates, and device settings. Make sure everything is running smoothly by checking for mistakes and fixing them as needed.Quantify and Improve Cyber Hygiene
Measure your organization’s attack surface, quantify cyber hygiene, and fine-tune your remediation strategies. Leverage a data-driven proprietary scoring model to improve the cyber hygiene of your organization.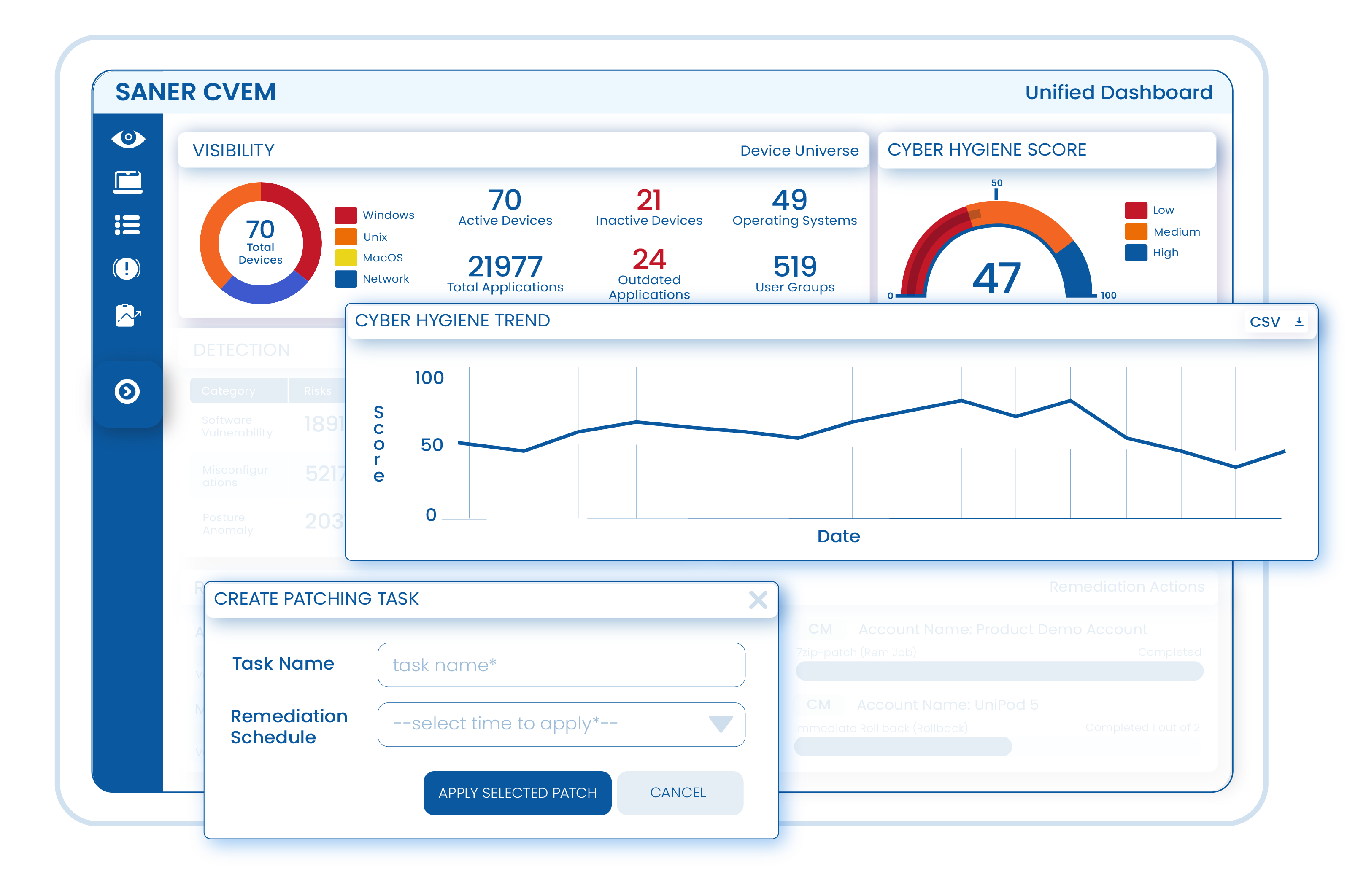
Global Enterprises trust Saner CVEM to Secure & Manage
their Attack Surface
IT Manager
Large Enterprise, Financial Sector
Saner is a great tool with some really good features like integrated automated patch management and configuration management. It’s a perfect fit for this space. Saner has reduced the time our IT teams spend in remediating risks.
CISO
Large Enterprise, Manufacturing Sector
CTO
Large Enterprise, BFSI Sector
Ready to Experience the Best Solution for End-to-End Vulnerability and Exposure Management?
Request a product walkthrough demo with one of our solution experts.