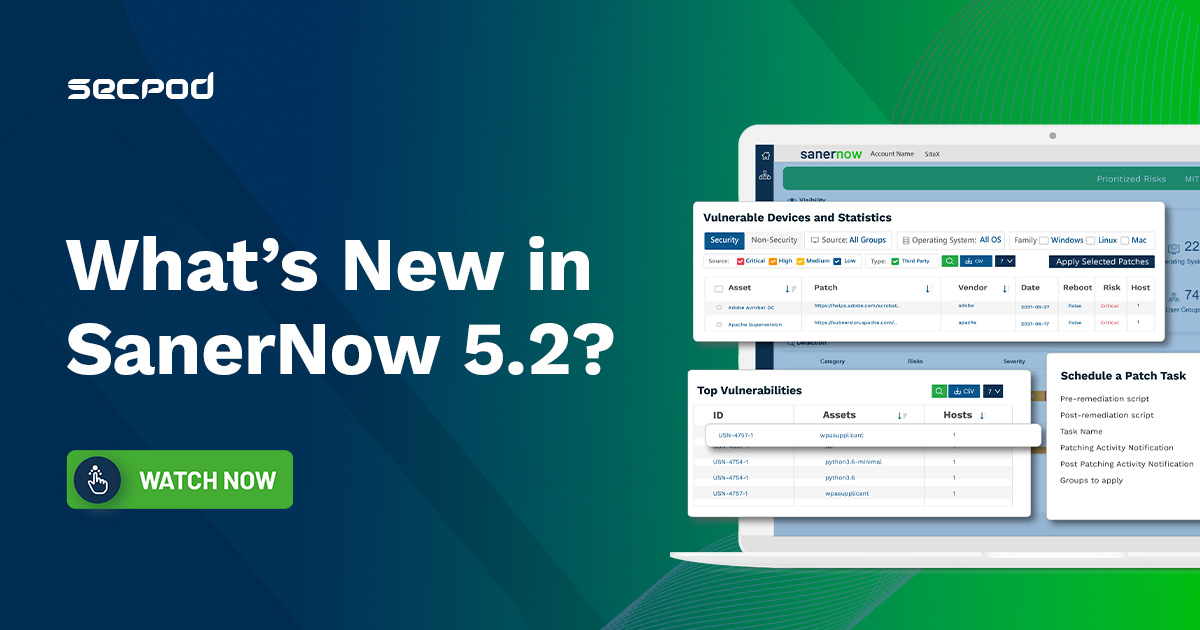
[On-Demand] Implementing Continuous Vulnerability Exposure Management (CVEM) Practices using SanerNow
SecPod’s SanerNow platform fully embraces CVEM practices to implement vulnerability management programs successfully. The platform focuses on viewing security from