SecPod's OEM Technology Solutions
Win More Customers with Industry Leading Advanced Vulnerability Management Technology
Leverage SecPod's Best-of-breed Technology and Drive More Revenue
Build/enhance your existing solution with SecPod’s Continuous, Automated, and Advanced Vulnerability Management Capabilities
Speed-up your Entry to Market
Integrate with SecPod’s proven OEM technology and embed vulnerability management, patch management, IT asset exposure, security controls, and compliance management capabilities to your existing solution within a matter of days and drive revenue to your business.
Seamless Integration with Flexible Licensing Models
Meet your customer demands with SecPod’s technology and deliver the next-gen solution your customers need. Our flexible model lets you choose between our APIs and SDKs to integrate with your solution. Win more customers and drive revenue to your business.
White-label or Rebrand and Sell Under Your Logo
Extensive support and Query Handling
SecPod provides extensive support during the onboarding process and assists in integration with your solution. Get developer access to the platform, API reference guides, code samples, and continuous support from experts.
Save Costs on Additional Development Overheads
Grow revenue, meet customers’ and market demand, and drive business at a lower cost and faster time-to-market. Make use of the next-gen technology built over years of research and save costs on additional development overheads.
Partner Strategically and Drive Business
Partner strategically with SecPod and build/enhance your security solutions leveraging our technology. Scale your business and bring in new revenue and customers.
Leverage SecPod's Expertise and Proven Technology
Integrate easily with SecPod's Cutting-edge Technology through SDKs/APIs
Rapid, Continuous, and Automated Operations
SecPod’s cutting-edge technology provides the industry’s fastest scans to discover vulnerabilities in less than 5 minutes and automates all security tasks to achieve continuous operations, from discovering the vulnerabilities to prioritizing them and thereafter remediating them to close the circle.
Seamless Integration and Interoperability
Multi-tenant Support with Segregated User Data
SecPod offers multi-tenant support to manage multiple business units and system users with a single server. With neatly segregated business users’ data, SecPod provides users with the ability to create various user roles with defined access rights to manage different areas of a corporate network.
High-Performance Scalable Architecture
SecPod provides a highly scalable solution with a Big Data architecture. The architecture efficiently supports the management of large number of devices.
Operates on a Lightweight Agent
SecPod’s technology works on a single, lightweight, multifunctional agent which weighs less than 20MB and executes all the tasks. The agent also takes up the role of network scanner and saves costs on integrating additional hardware. Technology partners can also choose to embed SecPod’s technology into their own agent through SDKs to prevent the installation of the additional agent.
Protects BYOD, Remote Office, and Transient Devices
SecPod ensures the security of organizations’ devices across perimeter limits. SecPod provides efficient protection and control of transient, remote, and BYOD devices from a centralized console.
Get Detailed Insights on SecPod's Robust OEM Technology

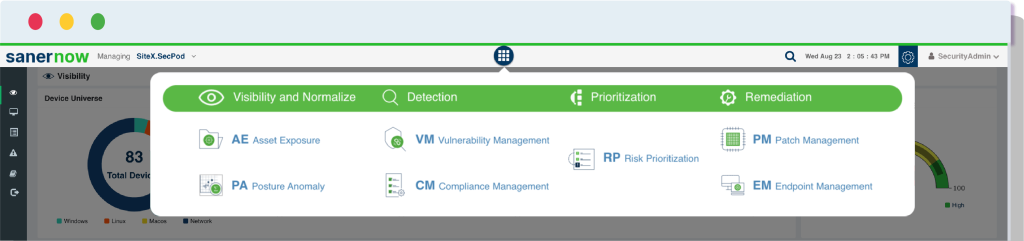
SecPod's Feature-rich OEM Technology Modules
Industry's Leading Vulnerability Management
Vulnerability detection, assessment, prioritization, and remediation are powered by the homegrown world’s largest vulnerability feed with 160,000+ checks, the industry’s fastest scanning in less than 5 minutes, and integrated patch management.
Automated Remediation/Patch Management
Automates end-to-end patch management from scanning to deployment across all major operating systems, including Windows, MAC, and Linux. SecPod also supports patching for 400+ unique third-party applications.
Industry agnostic Compliance Management
Provides an array of system hardening configurations to abide by major industry compliance benchmarks like HIPAA, PCI, NIST, ISO, and SOC-2. SecPod also provides the capability to create custom security policies.
Continuous Posture Anomaly Management
Provides visibility to IT infrastructure by collectively monitoring 100s of device parameters and 1000s of artifacts and by discovering Posture Anomalies, including the outliers, aberrations, and deviations present in your network
Security Remediation Controls Beyond Patching
Not all vulnerabilities can be fixed with patches, and they require numerous security controls for mitigation. SecPod goes beyond patching and provides hundreds of security controls to mitigate vulnerabilities. SecPod provides strong controls to block applications and devices, stop services and processes, manage firewall policies and registry settings, install and uninstall software, and much more.
Comprehensive IT Asset Exposure
Provides real-time IT asset visibility enabled by continuous scanning of hardware and software inventory, detection of shadow IT, rarely used and outdated applications, software license management, aggregated views of applications blacklisting and whitelisting, and customizable reports.
Let's Talk Business
Discover more about our OEM technology capabilities and offerings. Give a world-class experience to your product and drive revenue to your business.


