Ensure Continuous Compliance Across All Devices
Rapid, Effective, and Advanced Automation to Implement Continuous Compliance
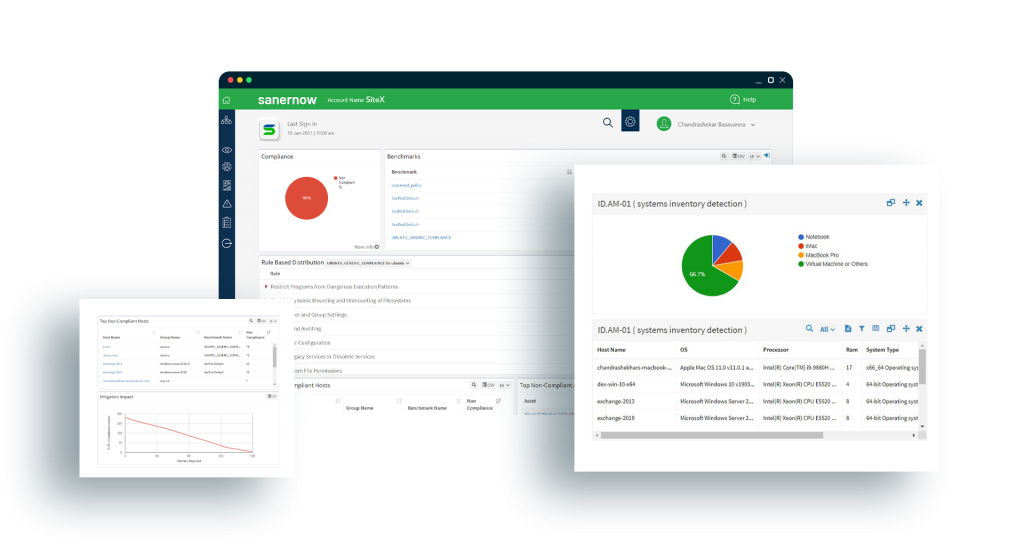
Align with Major Compliance Standards and Meet Security Obligations from the Cloud
One Smart, Multifunctional Agent for All Compliance Tasks
Implement all security compliance management tasks with one smart, lightweight, multi-functional agent that ensures continuous compliance monitoring and remediation actions.
One Console to Rule Them All
Seamlessly Regulate Security Compliance and Manage Risk Exposure
Gain Real-Time IT Assets Visibility and Control
Run continuous/on-demand IT asset scans and gather detailed hardware and software inventory. Detect outdated and rarely used hardware and software, and instantly detect the entry of vulnerable IT assets, blacklist and whitelist applications.
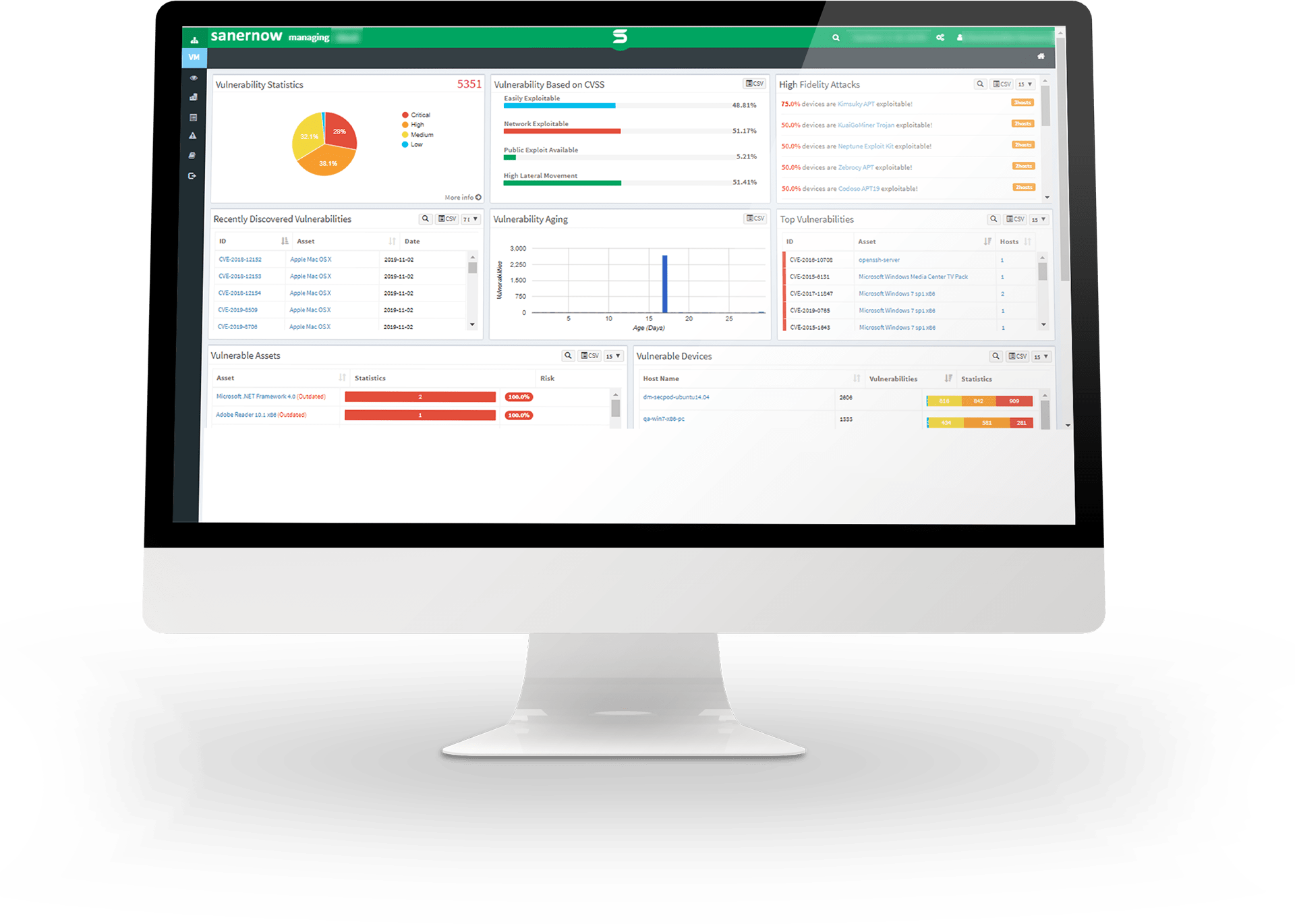
Rapidly Discover your Device Vulnerabilities with Over 175,000+ Vulnerability Checks
With the world’s largest SCAP feed with over 175,000 vulnerability checks and 500+ configuration checks per OS, and SanerNow’s intelligent scanning algorithm, vigorously scan your devices, precisely discover vulnerabilities, and analyze your cyber risk potential efficiently.
Reduce Risk Exposure with Integrated and Automated Patch Management
Remediate software vulnerabilities instantly using SanerNow’s integrated and automated patch management. Automate patching across all endpoints running Windows, MAC, Linux, and third-party applications.
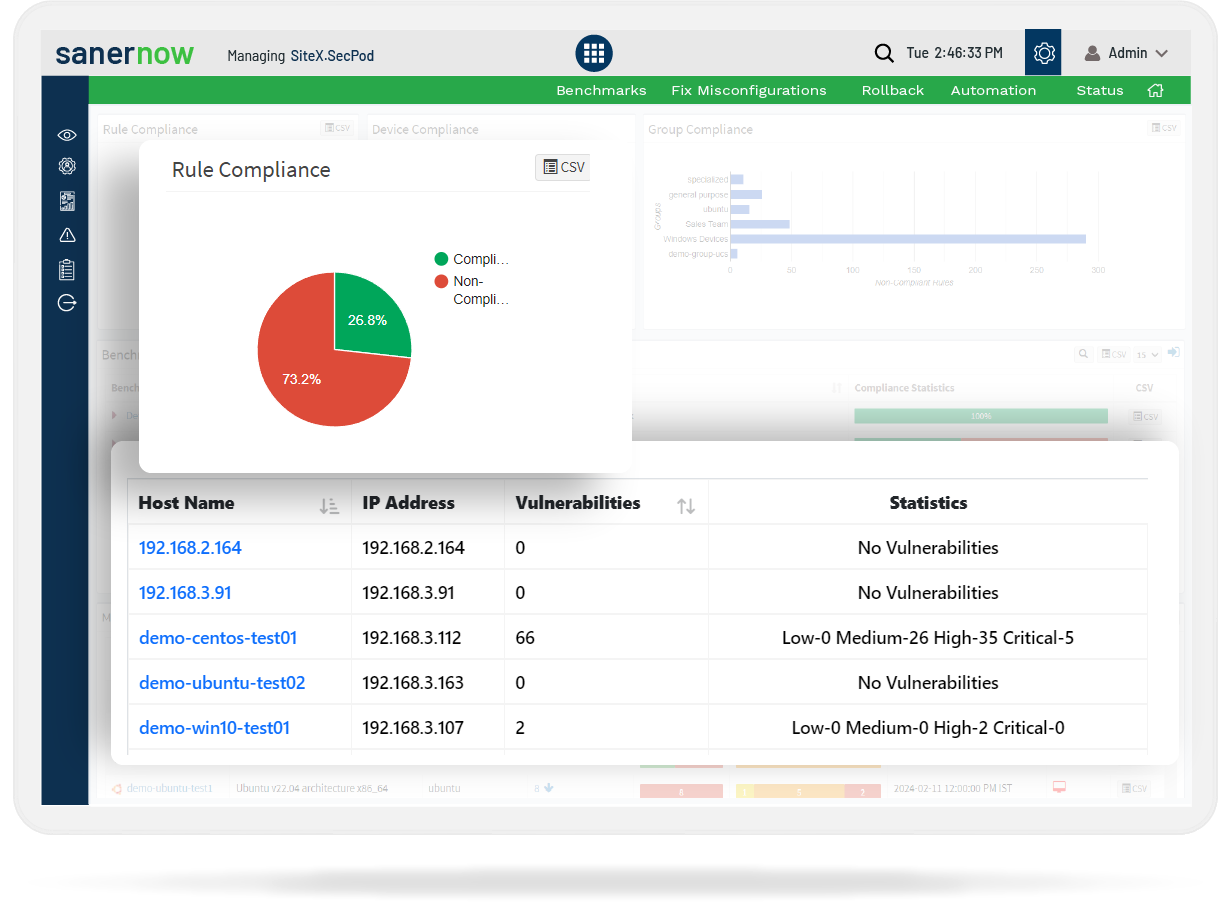
Scan and Identify Deviation from Standards, and Detect Non-Compliant Devices
SanerNow CM runs continuous scans to detect non-compliant or deviant devices and provides instant remediation suggestions. It monitors system deviations in real-time to ensure continuous compliance.
Support all Major Industry Compliance Benchmarks and Enables Creation of Customized Security Policies
SanerNow supports industry-standard requirements on policies and configurations out-of-the-box for HIPAA, PCI, ISO, NIST 800-53, and NIST 800-171. Further, it allows creation of customized policies to enforce specialized industry or organizational compliance policies. Build a continuous compliance framework with all security policies.
Strengthen your Endpoint Security Posture and Keep your Endpoints Healthy
Monitor antivirus deployments, the status of important system services and files, registry keys, rogue processes, etc., to keep endpoints healthy. Enable firewall policies and other security checks, quarantine or isolate devices or networks, discover and protect sensitive data, etc.
Block Malicious Applications and Devices, Reduce Attack Surface Instantly
Block any suspicious or malicious or unwanted applications and devices on your network. Implement effective application and device control across your endpoints and prevent security breaches to safeguard your network from emerging cyberattacks.
Detect and Respond to Threat Incidents Without Leaving any Security Gaps
Actively hunt for incidents of threats in your network and respond to them immediately. SanerNow allows you to detect any indications of attacks and system compromise across your devices and enables you to act upon them immediately.
Gain End-to-end Visibility of Your Enterprise Devices and Control them Instantly!
Get free unlimited access and try it yourself.