Vulnerability Management Essentials
What is Risk Based Vulnerability Management?
What is Vulnerability Risk?
Vulnerability and risk are two different worlds, but they are used interchangeably as vulnerability risk, which can be managed by a vulnerability management tool. The difference between risk and vulnerability is that risk refers to the potential impact of cyber-crimes. The combination of these words refers to the flaws and their adverse effects posing on an enterprise. On the other hand, vulnerability refers to weakness in the enterprise devices prone to cyber-crimes.
Traditional vulnerability management software is not enough to protect our complex IT landscape from security attacks. No doubt they might be efficient in tackling all the vulnerability risks, but they leave blind spots in your network. In addition, they deliver a theoretical view of risks and put you in a dilemma to understand which ones pose the most critical risk vulnerability to your organization.
Prioritizing a huge pile of vulnerabilities is even more frustrating. It seems to lack context to understand them based on their level of risk. It causes security teams to chase unnecessary issues while missing the most critical flaws with higher risk vulnerability to the enterprise. Hence, risk based vulnerability management platform is the way forward.
Now that we know the difference between risk and vulnerability let us understand RBVM.
What is risk based vulnerability management?
It is a strategic process to detect and assess the risk level of the vulnerabilities that helps to mitigate the flaws. According to Gartner, using risk based vulnerability management software by any enterprise will suffer 80% lesser security breaches. Risk based vulnerability management is vital as it provides effective remediation to improve the enterprise’s security posture.
How to prioritize vulnerabilities based on risk?
- Vulnerability scans report many vulnerabilities at once. These vulnerabilities carry a different amount of risks. The risk and vulnerabilities assessment software must focus on measuring the risk levels of each flaw and remediate bigger risk threat vulnerability first. It will reduce the threats to a greater extent.
- Most enterprises rely on CVSS scores to prioritize vulnerabilities in their environment. They assign a score to the threats at the time of discovery based on their level of risk. They do not account for changing real-time threat landscape. It is a good method to start with remediating vulnerabilities.
- Along with CVSS, it is essential to consider application type and business criticality. Every application and device has different levels of operational importance in an enterprise. Hence, critical applications susceptible to vulnerabilities must be mitigated as soon as possible with the assistance of vulnerability manager, regardless of the severity level.
- Also, it is vital to consider the age of vulnerabilities. Many enterprises sweep out old vulnerabilities and assume that they are mitigated. Any flaws that can be weaponized are used in attacks. Hence, enterprises must be aware of identifying and mitigating current exploits.
- When prioritizing, enterprises should be aware of the number of affected assets. For instance, if a medium-risk threat vulnerability is found in 100 assets, it should be prioritized over a vulnerability in 10 assets.
Therefore, all these factors help prioritize vulnerabilities and mitigate them before potential exploitation. We must know which vulnerability has the highest probability of an exploit to be a step ahead. It will lead to prioritizing vulnerabilities and remediating them, resulting in a decrease in security risk. Focus on the vulnerabilities that pose the greater risk, and enterprises must update VM policies and procedures to keep pace with evolving threats.
Hence, the decisive action is to approach risk-based vulnerability management.
The risk based vulnerability management process
Let us understand the RBVM process in SecPod SanerNow. SanerNow upgraded its vulnerability management platform smarter, making the whole process more efficient. The process includes six steps for the effective management of risks.
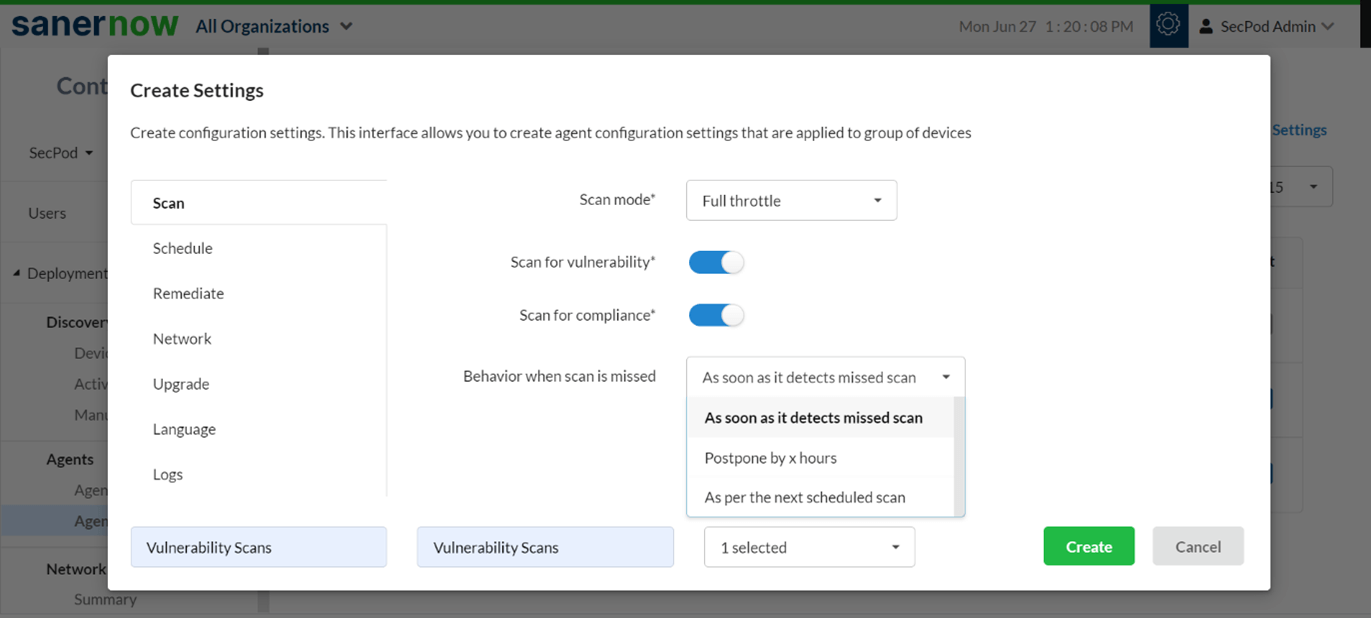
- Rapid scanning
SecPod SanerNow has an efficient intelligence-augmented scanning algorithm. This algorithm can scan and detect the vulnerabilities in less than 5 minutes on your devices. It will aid in gaining clear visibility and control over your attack surface.
- Precise detection
SecPod SanerNow facilitates accurate detection of flaws without producing any false positives with its state of the art vulnerability management system. As the world’s largest vulnerability database with more than 175,000+ security checks, it helps precisely detect risks. It also supports various major operating systems like Windows, Linux, MAC, and other 450+ third-party applications.
- Rigorous assessment
SecPod SanerNow detects and assesses vulnerabilities, and risk vulnerability levels are determined. It aids in the decision-making process on mitigation of flaws. Predictive analysis of risk threat vulnerabilities is one method that helps to improve the security posture by predicting the probability of new threats. It is done through the recorded occurrence of previous threats. Hence, the vulnerabilities found are assessed and thoroughly analyzed to mitigate them.
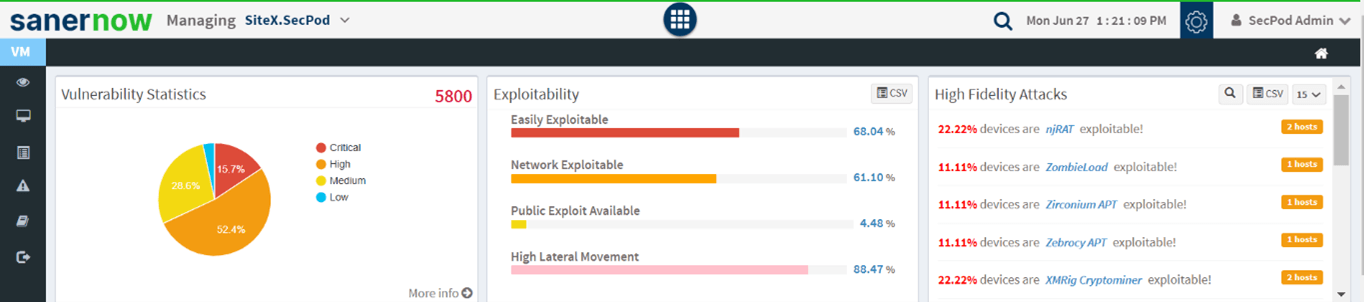
- Accurate prioritization
SecPod SanerNow prioritized the vulnerability risks with the CVSS model. It helps enterprises in vulnerability remediation of high-risk vulnerabilities first. Often, enterprises blindly try to mitigate all the flaws. Therefore, they tend to ignore high-risk vulnerabilities. CVSS model provides scores ranging from 1 to 10, where 10 depicts high-risk levels. SanerNow also provides details on the exploitability range of vulnerabilities to understand the risks possessed.
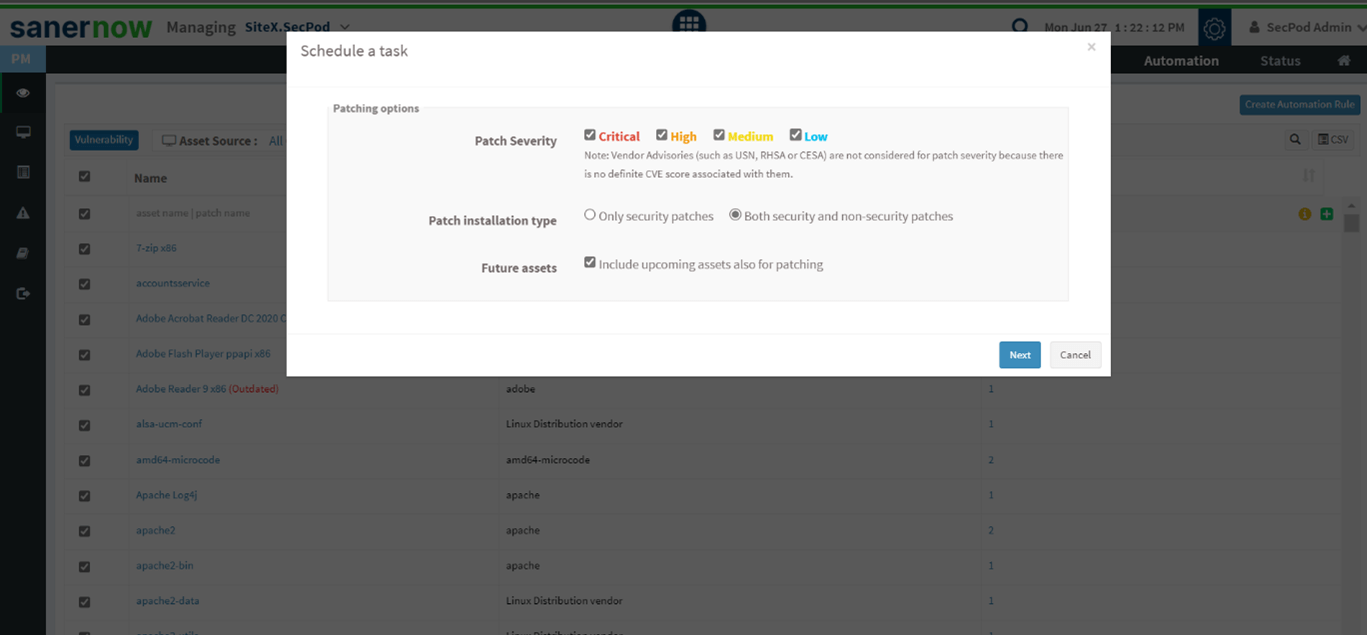
- Integrated patch remediation
SecPod SanerNow provides an integrated and automated patch remediation module. Once you have assessed and prioritized the vulnerability risks, you can quickly remediate them using SanerNow patch management system. It reduces the security gaps by remediating flaws soon after detection. Patches are available accordingly to mitigate these flaws immediately.
- Custom reports
SecPod SanerNow provides comprehensive reports with customizations. These reports help to retrieve actionable insights on vulnerability details.
Difference between vulnerability management and risk-based vulnerability management
Conventional vulnerability management system includes scanning, detection, and assessment to mitigate flaws. The major pitfall is a lack of accurate insights into the risk potential of each flaw. Hence, enterprises are not aware of the severity that a vulnerability possesses. They tend to mitigate them randomly, creating chances of missing out on the most critical flaws. Risk based vulnerability management facilitates accurate prioritization based on risk levels. To know more about the importance of RBVM, refer to this link.


