Vulnerabilities are increasing rapidly, and attackers are on the lookout for more sophisticated ways to exploit an attack. To add to this, the security landscape is also changing, continuously adding more burden to the shoulders of security teams. With rising vulnerabilities and evolving security landscape, conventional vulnerability management platform is no longer sufficient to manage the attack surface. Today, security teams are in a tough position to upgrade their Vulnerability management program to deal with the complex attack surface.
In this scenario, one unique term is getting popular among security administrators, which is “Risk-based vulnerability management.” A risk-based approach to vulnerability management software is said to increase the efficacy of vulnerability management through detailed assessment of vulnerabilities and the risk factors leading to exploitation.
You are wondering how Risk-based vulnerability management platform is different from conventional vulnerability management? This blog has got you covered for this.
About conventional vulnerability management and how it works:
Before we dive in and see about the risk-based approach to vulnerability management, let us take a quick look at how conventional vulnerability management works. Vulnerability management is a systematic and repetitive process to discover and remediate vulnerabilities. The method comprises different steps from scanning, detection, assessment to remediation of vulnerabilities. After successful detection of vulnerabilities, security teams immediately take the process of remediation here. The major pitfall of this conventional vulnerability management is the lack of insights into the risk potential of each vulnerability. As Security teams are not aware of the risk possessed by each vulnerability, they tend to randomly remediate the vulnerabilities in their organization. This quickly creates chances for them to miss out on the most critical and high-risk ones.
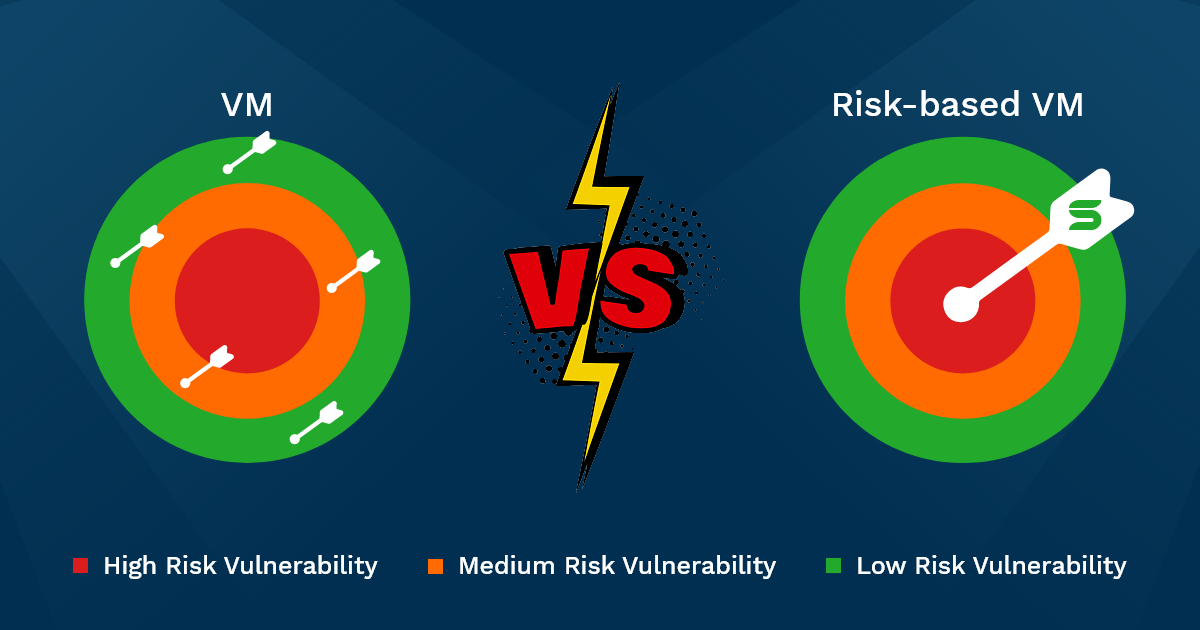
Risk-based vulnerability management software brings a solution for this by bringing accurate prioritization of vulnerabilities based on the risk levels.
Risk-based vulnerability management is the Way Forward:
What is RBVM?
Risk-based vulnerability management software is a strategic process to assess the imposed risk levels of vulnerabilities, prioritize the vulnerabilities based on the evaluated risk levels, and remediate vulnerabilities with higher risks to reduce potential attacks. Evaluating risk levels is done by considering multiple factors such as threat intelligence feeds, public risk ratings of vulnerability, asset inventory, current exploit activities, etc.
According to Gartner, by 2022, organizations using risk-based vulnerability management will suffer 80% fewer breaches. Thus, risk-based Vulnerability Management becomes the need for every organization. This provides an organization with smarter and more efficient risk remediation that strengthens the security aspect of the organization.
Why is there a need for Risk-based vulnerability management?
- The rise in vulnerabilities and data breaches
In 2020, the National Vulnerability Database (NVD) recorded hefty vulnerabilities for 18,353. It was all-time high leakage of records that was 140 percent higher than in 2019.
Vulnerabilities are rising exponentially every day. The rise in vulnerabilities determines several ways hackers can attack and the time restraint faced by security teams to detect and remediate. Risk-based vulnerability management aids smarter and faster remediation with a focus on high-risk ones.
- Correspondence of ransomware and vulnerabilities
Vulnerabilities are an open window for Ransomware attacks. They penetrate through the first point of contact and move among devices. One such disaster took place in 2017, the WannaCry attack. Old vulnerabilities that are not patched or reported are associated with ransomware groups. Ransomware groups make these vulnerabilities a weapon to readily execute the attack. Faster remediation of high-risk vulnerabilities like this would have easily prevented this attack. Risk-based vulnerability management will assist this by aiding you to remediate the most critical ones first. Risk-based vulnerability management with integrated patch management software will remediate vulnerabilities that pose more threats and eventually patch every vulnerability, leaving no chance for attackers to take advantage of older and unpatched vulnerabilities.
- The increasing size of the organization
The size of the organization is directly proportional to the number of vulnerabilities. It means as the size of the organization increase, the bandwidth of vulnerabilities exceeds. Practically, you cannot fix every vulnerability. When a vulnerability scanner gives a pool of vulnerabilities, the more scalable approach is to have a standard vulnerability prioritization process instead of remediating every vulnerability firsthand. Risk-based vulnerability management with automatic prioritization with the factors such as exploit activity, availability, age, leverage to ransomware, should be a default feature to make a real difference in your vulnerability management.
- Reduce the security gaps
To prevent attacks, the speed of vulnerability detection and remediation plays an essential role. Many organizations detect vulnerabilities sooner but lag in remediating them. This leads to security gaps taken advantage of by the attackers. According to a recent study, the median time is 22 days to develop a fully functional exploit. Hence, quick remediation after detection will reduce exploitable vulnerabilities. Inculcating risk-based approach to vulnerability management will speed up the detection and remediation process to reduce security gaps in the organizations.
- Asset heterogeneity
As the organization grows, the list of assets increases rapidly. The heterogeneity of devices is diversifying an organization’s IT asset portfolio. These factors lead to a rise in volume and complexity of vulnerabilities in the environment. The practical way to handle this is risk-based vulnerability management where you can easily manage the most critical vulnerabilities first, prevent a wide array of potential attacks.
How to calculate and analyze the risk levels of vulnerabilities?
Noting that risk levels of vulnerabilities are always dynamic, multiple factors contribute to measuring risk levels of vulnerabilities. A combination of all risk factors will classify each vulnerability and categorize based on severity.
- CVSS score
CVSS (common vulnerability scoring system) is a scoring system and framework for rating software vulnerabilities based on their severity levels, maintained by the NVD (National Vulnerability Database). CVSS is not the only factor for risk assessment. Considering only CVSS is a serious flaw because the scores provided by CVSS are disclosed at the time of vulnerability disclosure. Hence, it does not account for the current state of vulnerability in the real world. They are good, to begin with, but not the only way to assess the risks.
- Application type and business criticality
Every application and device occupies different levels of operational importance in organizations. Admin should take precautions when critical applications or devices have vulnerabilities. They must be considered critical no matter the level of vulnerabilities. For instance, web servers of e-commerce websites, database servers where downtime would have an impact on the revenue and reputation of the business. Hence, business users should be educated about necessary downtime to save the systems from attacks.
- Exploit activity
A study found that exploit development time is usually relatively short. In their data, 71 percent of the exploits were developed in a month, almost a third (31.44 percent) were developed in a week or less, and only 10 percent took more than 90 days to exploit.
Zero-day vulnerabilities have a critical level priority. Sometimes, even a critical vulnerability may not be actively exploited. There might be other constraints like the ease of developing an exploit and other factors. Availability of vulnerabilities makes technical work easier for attackers since the exploit is readily available to weaponize and deploy. When the exploit is available and actively preferred by attackers, its priority level increases.
- Impact of a potential exploit
The damage caused to exploited devices, the environment, and businesses are effects of exploitation. The ease of developing exploits makes the attacker choose to exploit aggressively. One such technical impact is a worm-able vulnerability that exploits future malware and propagates from one vulnerable device to another.
- Vulnerability age
Of the 223 ransomware attacks that involved vulnerability exploits, 213 (96 percent) vulnerabilities were reported in the US National Vulnerability Database (NVD) before 2019.
The common mistake of an organization is to sweep out the old and low severity vulnerabilities. But these vulnerabilities have a higher risk of causing more attacks than new ones. Hence, security teams should be aware of the vulnerabilities and current exploit activity in their environment and be ready to mitigate them sooner.
- Count of affected assets
The probability of an exploit increases if a more significant number of devices are attacked with vulnerability leading to a ransomware attack. When a vulnerability is found in too many devices, the rating of critical severity increases by default. For instance, consider a vulnerability is found in 100 assets. This should be more important to prioritize than critical vulnerability in 10 assets.
Reinforce your defense with SanerNow Risk-based vulnerability management:
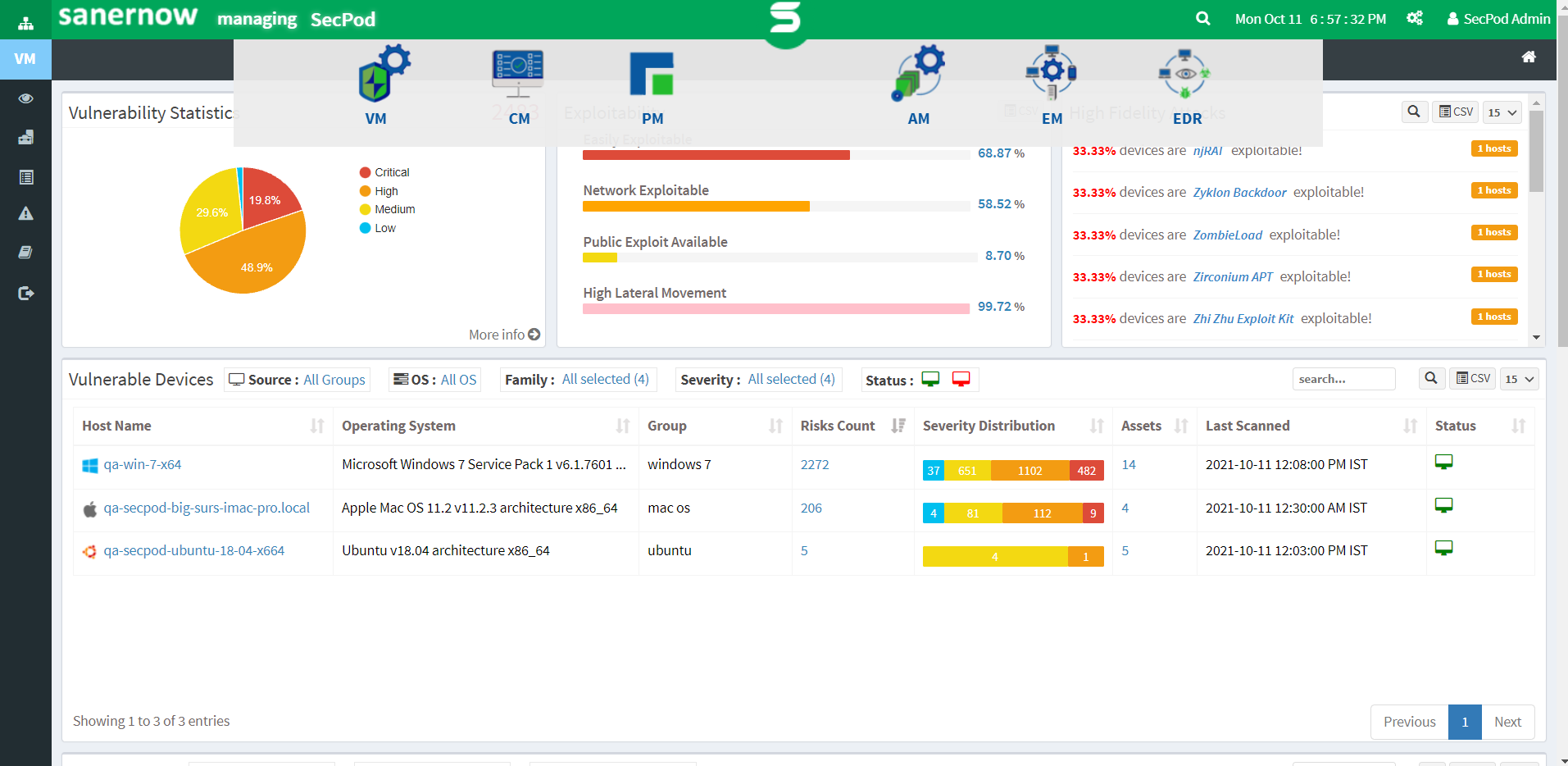
SanerNow Vulnerability management is a cloud-based tool that calculates and analyzes exact risk levels of every vulnerability considering all factors.
With SanerNow, you can,
- Prioritize vulnerabilities accurately and determine the exact risk level they pose to the environment.
- Automate vulnerability scans to tackle upcoming vulnerabilities continuously.
- Leverage the homegrown, world’s largest vulnerability database with 175,000+ security checks to detect risks effortlessly.
- Perform vulnerability scans in under 5 minutes to immediately detect critical risks.
- Mitigate risks to avoid security gaps with an integrated patch management tool.
- Build custom reports to plan the vulnerability management process effectively.
Schedule a demo with SanerNow vulnerability management and go beyond your conventional vulnerability management.