Vulnerability Management Essentials
Windows Vulnerability Management
Businesses use technologies to transmit and store valuable information. They are responsible for safeguarding sensitive business data against any cyber-attacks. Hackers can invade a company’s network with the sole objective of causing cyber security issues. Therefore, vulnerability management software and various vulnerability scanners are necessary for an enterprise to protect its business environment from attacks.
Generally, businesses of all sizes use operating systems such as Windows, Linux, Mac, etc., on their computing devices. Windows is one of the most widely used operating systems in most business organizations. As a result, the widely used online platform is more prone to attacks from cybercriminals.
There are various vulnerability scanners for Windows that offer insights into real-time security issues and exploits scores, which helps to communicate the severity of the possible threats. It is also integrated with vulnerability remediation solutions to fix them as soon as possible.
Why Windows Vulnerability Scanner is Necessary for Windows Operating Systems and their Supported Servers & Devices
A Windows vulnerability scanner is an easy-to-use application. It helps evaluate the efficiency and security of operating systems, networks, and web applications used in the devices and computing environment.
Using these Vulnerability scanners, security teams detect loopholes or flaws anywhere in the systems like routers, web servers, fax machines, firewalls, operating systems, etc. Operating systems have various supporting devices and servers; therefore, window vulnerability scanners can identify security gaps in all network-connected devices.
How does Windows Vulnerability Scanner Work
The application of a Windows vulnerability scanner entirely depends on the size of an enterprise and its IT security team. IT security experts choose the vulnerability management tool as per the complexity of the computing environment. The security of Windows-supported devices and networks is as important as the security of Windows OS. Here are the three significant steps on how vulnerability scanners identify vulnerabilities and assist IT security teams in a company.
- Identification
- Risk Assessment
- Reporting
Identification
The vulnerability scanner for Windows can locate and discover various supported devices, usage of ports, and applications. The tool collects processed data from the server and compares it with the data retrieved from Windows OSs. It correlates the information to identify the vulnerability.
An IT security team in an organization configures the Vulnerability scanner tool according to the required CPU usage time. The scanning process is intrusive enough to affect the system’s performance during working hours, as it can consume enormous bandwidth. Therefore, the intensity of the process is adjusted depending on the working hours of an enterprise. The security team can also schedule the scanning process after operating hours.
IT experts can scan all OSs and connected devices simultaneously by transforming one of the devices as a network scanner or using a dedicated system for scanning. New vulnerabilities are likely to appear in networks, operating systems, or supported devices. And the scanner automatically scans whenever a new asset appears in the existing network.
Risk Assessment
Generally, a Windows vulnerability scanner will report an extended list of vulnerabilities. And vulnerability remediation is a complex process. For any IT security experts, mitigating or remediating the entire list of vulnerabilities is time-consuming and requires too many IT resources. Therefore, It is essential to assess the risks that pose the highest and the lowest threats. Here are a few factors to identify the severity using a vulnerability scanning tool:
- The severity of a vulnerability in the operating systems, supporting networks, and the level of negative impact if it exploits
- Determine whether a cyber attacker requires physical access to the business environment or just the internet to exploit the vulnerability in a system.
- The ease with which IT security experts reconfigure the existing security controls to mitigate the risks and prevent them from being exploited
- Identifying the vulnerabilities that are false positives
Reporting Vulnerabilities
The vulnerability report offers the IT team a clear understanding of remediating solutions as per the severity level of the risks. A Windows vulnerability scanner correlates the data of all its operating systems with the central Windows server and offers an insightful report about the risks.
It can also generate customized reports at the convenience of the IT team. The report allows security experts to follow the risk trends and information about specific vulnerabilities in an operating system and other supporting networks.
Types of Vulnerability Scanners for Windows
IT experts plan the vulnerability scanning process in various ways as per their company’s needs and style. However, internal and external vulnerability scans are two different types that the team adopts in an IT infrastructure.
External Scan:
An external scan is performed from outside an enterprise’s network. It remotely scans the IT assets exposed to the internet, including operating systems, web applications, ports, networks, etc. Some remote-based vulnerability scanners allow an IT team to perform scans remotely in the comfort of their locations.
Internal Scan:
Internal scans are performed inside an organization’s network. It lets you protect applications, systems, and servers that are not covered by external scans. An internal scan detects IT security flaws as follows:
- Exploited vulnerabilities by an attacker who has gained access to the workplace environment.
- The threat posed by a security bug in an application that has made its way inside the business network.
- Identify “insider threats” posed by displeased employees or contractors.
Windows Vulnerability Remediation
When it comes to addressing vulnerabilities, Microsoft announces the critical vulnerabilities in Windows operating systems and relevant patches. As a part of effective utilization of the Windows update services, all the operating devices receive the relevant patches. It eliminates the possibility of an attacker exploiting any vulnerabilities in the Windows operating system.
Organizations ensure periodic Windows updates using various vulnerability management software. It avoids any unauthorized attempt to decrypt, inject, or modify business data into devices.
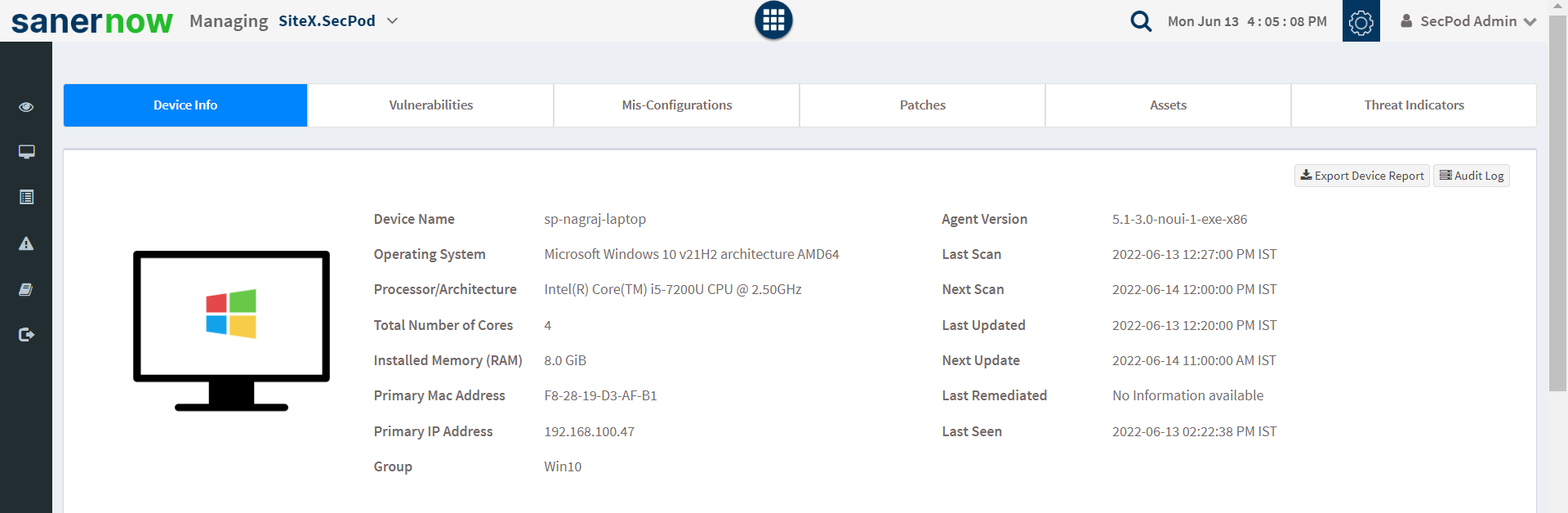
How SanerNow Manages Vulnerabilities in Windows Operating system
SecPod SanerNow’s Windows vulnerability management software operates across all major operating systems: Windows, Linux, Mac, and other third-party applications. The platform is hosted on the cloud and supports the following list of Windows operations systems:
- Microsoft Windows 7
- Microsoft Windows 8.1
- Microsoft Windows 10
- Microsoft Windows Server 2008
- Microsoft Windows Server 2008 R2
- Microsoft Windows Server 2012
- Microsoft Windows Server 2012 R2
- Microsoft Windows Server 2016
- Microsoft Windows Server 2019
- Microsoft Windows Server Semi-Annual-Channel
Here are the Features of SanerNow Windows Vulnerability Management
Industry’s Fastest Scanning Process
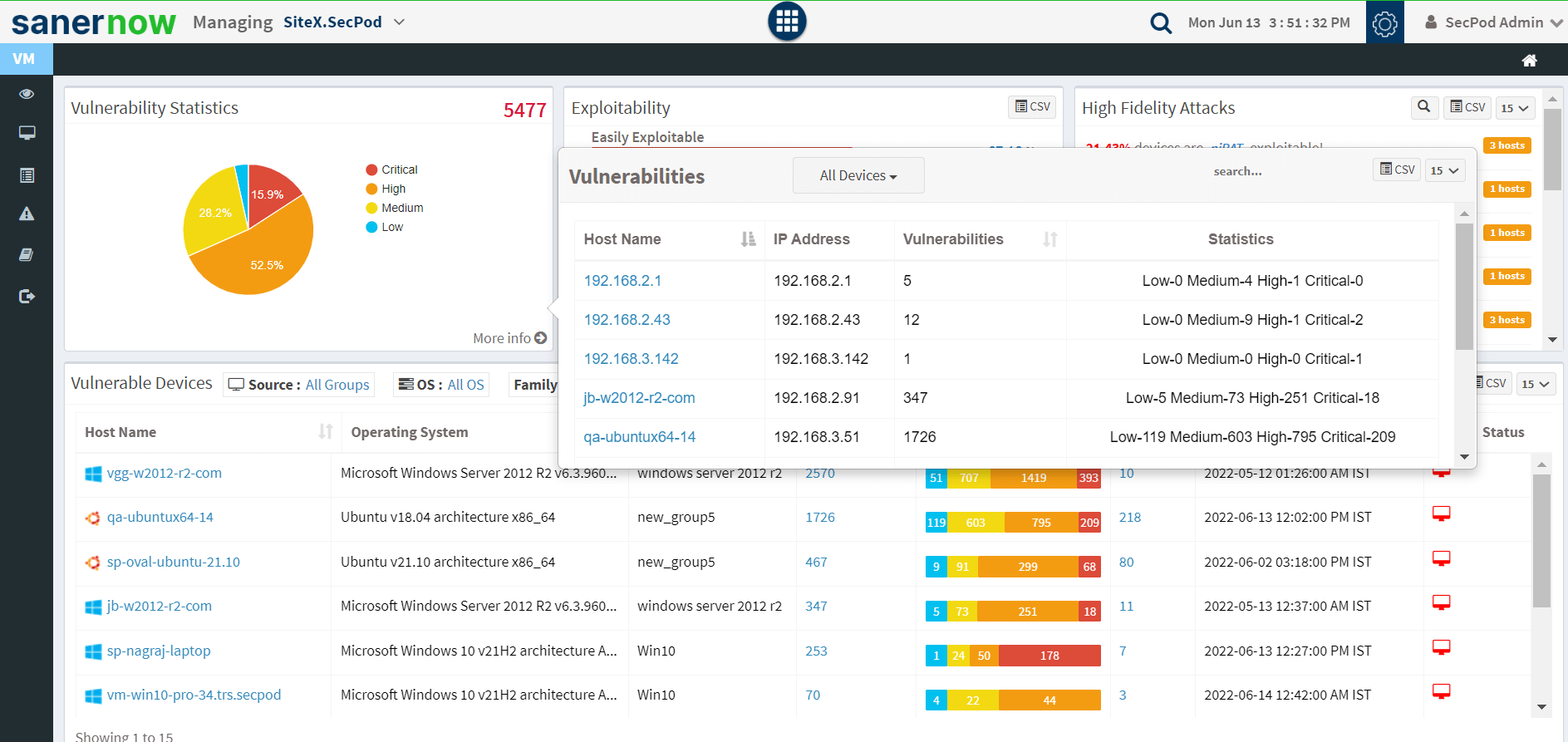
While scanning devices operating on Windows and their supported devices & servers, SanerNow’s vulnerability scanner for Windows correlates the gathered data with Microsoft’s Windows database and delivers the vulnerability report. The Vulnerability management platform offers real-time scanned data of the entire Windows operating system and its supporting devices in less than 5 minutes.
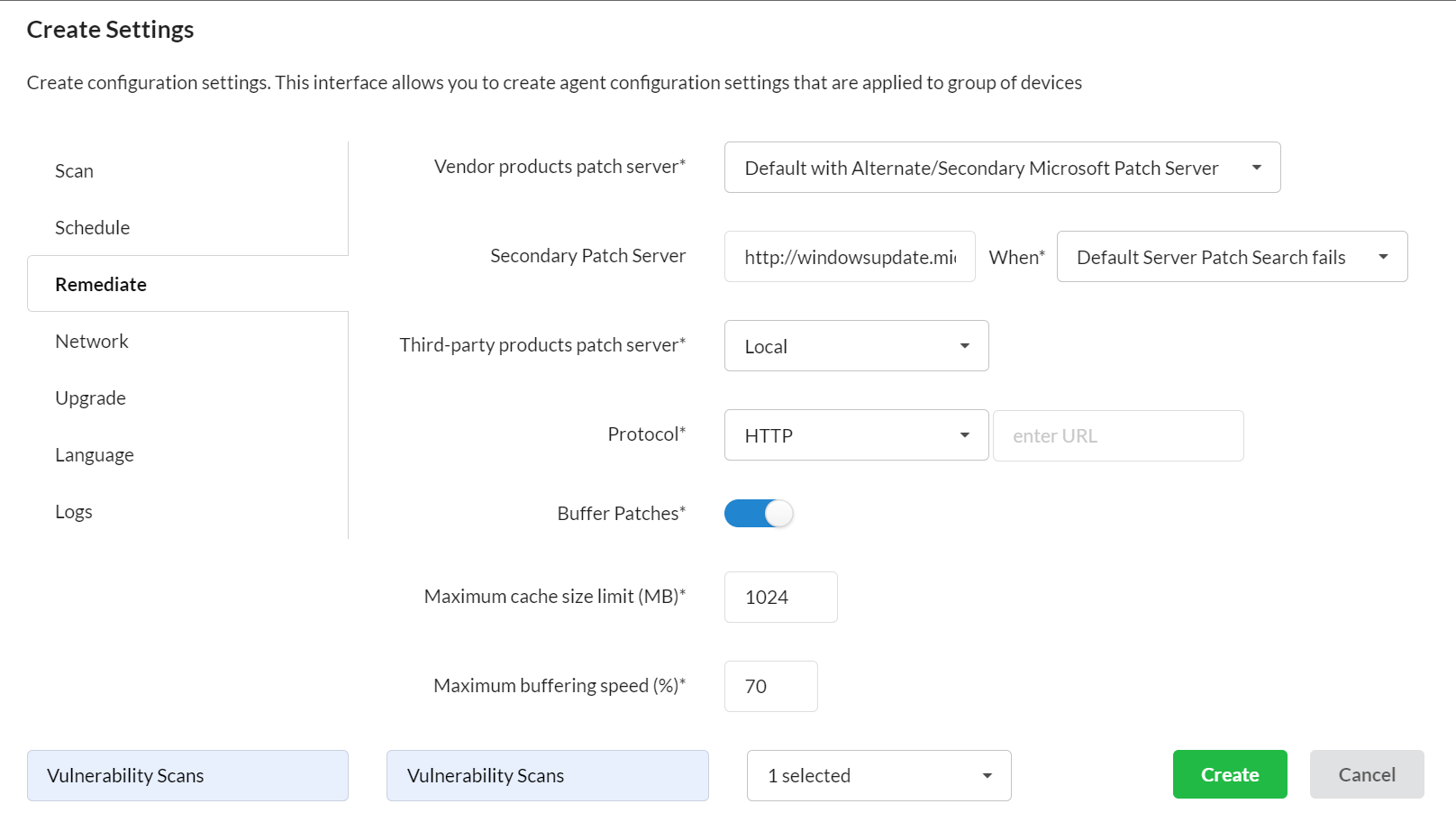
Risk-based Assessment and Prioritization
SanerNow assesses the scanned report of all the Windows operating systems in a network. The high-risk vulnerabilities are assigned a severity score against the less critical ones in this stage. The final risk-based scoring report helps IT admins focus on the high severity issues and spend less effort on less critical ones.
Integrated Patch Remediations
Further, SanerNow employs a dedicated patch management server to remediate Windows vulnerabilities. All the devices equipped with Windows OS are in-sync with SanerNow’s server through a multi-functional agent. Also, the agents will help all operating systems receive new patches from the Windows update server. Then, IT security experts remediate the specific vulnerabilities using integrated patch management features. The platform can automate the remediation process to save both time and resources for IT teams.