Vulnerability Management Essentials
Vulnerability Scanning
Vulnerability scanning is needed to carry out scans across network devices. It is an automated platform that serves the vulnerability management tool. Once after detecting, an enterprise can quickly proceed with further remediation steps of the vulnerabilities.
Now, let us understand “what are vulnerability scanners?”.
What are vulnerability scanners?
A vulnerability scanner, known to be an automated vulnerability scanning tool identifies security issues. It also provides a list of all assets in an enterprise network. Furthermore, it collects all operational asset information like the operating system, open ports, installed software, and other attributes. Thus, it continuously monitors to be safe from attacks.
We came to know “what are vulnerability scanners”. Let us dive to look at the techniques to perform vulnerability scans.
Vulnerability scanning techniques
- Static analysis
Static analysis is a fast and reliable technique to detect flaws. It focuses on analyzing program structure in various ways. It mainly highlights on code of the program structure and analyzes it thoroughly. There are many other vulnerability scanning techniques in static analysis like lexical analysis, constraint analysis, type inference, etc.Let us focus on the general aspect of static analysis and how it works.
Various vulnerability management tools are available to perform static analysis. These tools use simple algorithms like pattern matching. False positives determine the performance of these tools. Many tools have low false positives; some have accurate, and others with high false positives.
For instance, a database or loophole library helps validate vulnerabilities in the program. But the problem is, when an unknown vulnerability is detected, it is impossible to compare it with the existing loophole library for validation.
Thus, a dynamic detection strategy with static analysis can help resolve such problems.
- Attack graph analysis
The attack graph represents all paths that a hacker follows in the network. The hacker’s path involves damaging the network, gaining complete access over the network, etc. Attack graph analysis is the widely used approach for network security. Let us know more about the attack graph.The attack graph determines the security flaws that lie in the network. System administrators use attack graphs to analyze the network. It determines the flaws present in the network that might allow a hacker to exploit it. These graphs are large and represent the complete network with its flaws.
Hence, they are complex to understand and analyze. It is essential to generate and analyze the attack graph to protect the network from security breaches. Analyzing vulnerabilities in the network with a vulnerability management software helps to generate an attack graph with an attack graph generator. There are various techniques to generate and analyze attack graphs. Some of the techniques are:
a. ranking algorithm
b. adjacency matrix clustering algorithm
c. game-theoretic approachThus, attack graphs are a good approach when we are concerning network security as a key aspect.
Now we know these vulnerability scan techniques briefly, we will move on to the different methodologies used in vulnerability scanning.
- Hacker-powered scans
It uses a community-driven approach to vulnerability scanning and encourages freelance hackers to find bugs. With this method, enterprises can continuously monitor their systems and prevent potential attacks. Many programs offer rewards to push these hackers.
- Internal scans
Internal scans run inside the network. They use the privilege escalation technique to run. Internal scans project lights on how internal members of an enterprise implement permissions and find vulnerabilities. It prevents an insider attack from gaining access to servers and sensitive information.
- External scans
External scans mainly focus on assets that connect to the internet. They include login pages, open ports, websites, etc. With external scanning, an enterprise can determine the vulnerable assets and take actions accordingly.
- Continuous scans
Continuous vulnerability scanning refers to scanning networks regularly. It scans the complete network and produces a comprehensive report of all vulnerabilities for further remediation. It overcomes periodic scans that run once or twice a month. It also eases the process of manual scanning by scheduling scans daily.
- Application-based scans
Application-based scanning focuses on a particular aspect of the business. For instance, non-technical teams can relate to vulnerabilities posed to their assets. They can understand risks and take action to protect their assets.
These were some of the vulnerability scan techniques. Let us know the tools used for finding these vulnerabilities.
Types of Vulnerability Scanning tools
Vulnerability scanning tools play a major role in scanning flaws. These tools improve the security network and keep hackers at bay. Every enterprise should have vulnerability scanning tools to prevent potential attacks.
Now let us understand the types of vulnerability scanning tools.
- Host-based scanners
Host-based scanners identify vulnerabilities in the server, network hosts, etc. They provide complete visibility in the configuration settings. They also help locate potential attacks from hackers.
- Network-based scanners
Network-based scanners discover unknown devices on the network. The network scanning can be on wired or wireless networks. They find unknown perimeter points like remote access servers, insecure networks, etc.
- Wireless scanners
Wireless vulnerability scanners help to identify notorious access points. It also validates the enterprise network and its security configuration.
- Database scanners
Database scanners locate weak points in the database to prevent potential attacks.
- Application scanners
Application vulnerability scanners run on websites to identify software faults and network errors.Now we know briefly about types of vulnerability scanners. Let us gain some knowledge about the SanerNow scanner.
SanerNow Vulnerability Scanner
You can reduce your attack surface with real-time, on-demand, and continuous vulnerability scans with SanerNow. SanerNow offers the fastest vulnerability scanning tool that scans in less than 5 minutes. It scans the entire network and the asset in the bandwidth of less than 5 MB. You can also automate and schedule these scans daily.
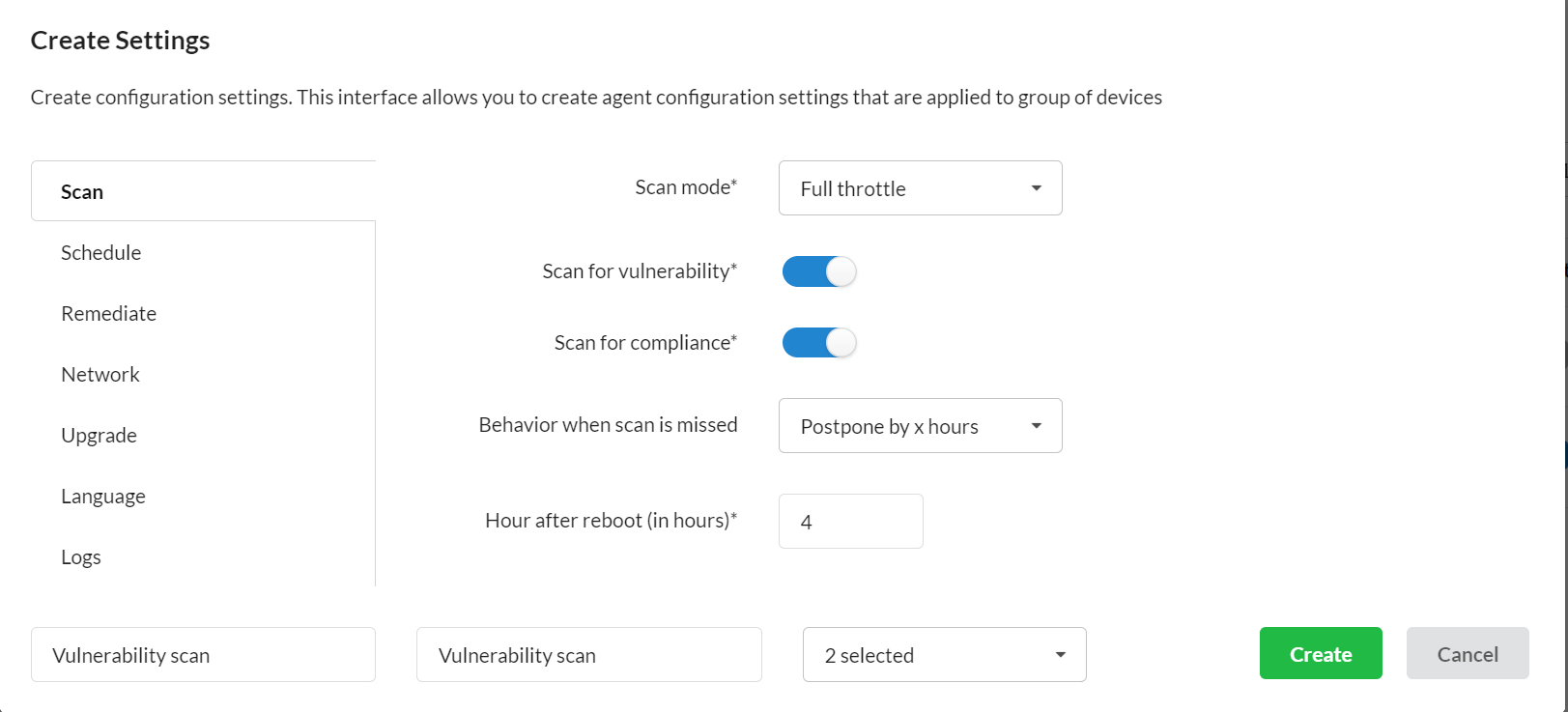
Furthermore, you can either run low scans or full throttle with the scan mode option. Low scans reduce CPU consumption, and full-throttle scans are for quick scans. SanerNow vulnerability scanner runs silently in the background without disturbing the user. SanerNow works on a powerful agent-server model. The agents installed across the endpoints also take up the network scanner’s role to scan other devices in the network, saving investment over additional hardware. SanerNow’s vulnerability scans are backed by its homegrown world’s largest vulnerability database with more than 175,000+ security checks. It ensures the vulnerability detection is accurate with zero false positives. SanerNow also supports integration patch remediation to remediate the vulnerabilities instantly.


