Vulnerability Management Essentials
What is Vulnerability Management Process?
The vulnerability management process is all about identifying, assessing, prioritizing, remediating, and reporting network critical vulnerabilities. The process involves various IT security tactics, essential to overcome the cyberattacks that harm businesses and operations.
Vulnerability Management Process Steps
The steps involved in the vulnerability management solution allow enterprises to discover security flaws in a computing network, assess and prioritize the ones with higher risks and remediate them using relevant techniques. The outcome of the vulnerability remediation process is then verified. The procedure secures the IT infrastructure against cyber-attacks.
The four crucial vulnerability management process steps are as follows:
1. Identification
2. Assessment
3. Prioritization
4. Remediation
Identifying Vulnerabilities
The identification stage involves a vulnerability scanning process. It is the primary step for detecting vulnerabilities across network devices. The scanning tool relies on a database to fetch the vulnerability information. It is constantly in synchronization with the vulnerability database to get the latest updates.
Automated or manual scans are used to identify the vulnerabilities, depending on the organization’s security needs. The vulnerability management tools help perform the scan at regular intervals of the day.
The process also involves scanning network-accessible systems and remotely accessing the network to obtain necessary security-related information. And correlate the data with the database of vulnerabilities. The scanning process sometimes may disrupt the performance of devices. Thus, the scans can be scheduled during non-operating hours or fine-tuned to be less disruptive.
Assessing Vulnerabilities
The next step after the identification process is to assess the likelihood of treats in an asset. The need to evaluate the risks arises mainly to use the available resources effectively. In addition, resolving the IT security risks involves certain standards based on the organization’s risk-based vulnerability management solution.
There are various risk rating and scoring systems for vulnerabilities. One of them is Common Vulnerability Scoring System (CVSS) scores between 0 and 10. It helps companies to focus on the issues that matter the most. Using the CVSS score, an IT security expert can decide what to remediate first. In reality, the actual risk depends on various factors beyond CVSS scores. For instance, the motivation and the expertise of attackers are always unknown. Therefore, the CVSS score is not the only security data point. And the risk is always dynamic.
How the Risk Associated with Vulnerabilities are Measured
The ease of attack using a vulnerability is measured by analyzing various parameters. Some of them are as follows:
- Whether an attacker can exploit an asset using internet access or requires physical access to the computing environment
- The level of complexity involved in causing an attack physically using a vulnerability
- Evaluate if the assets have multiple authentications factors enabled. If so, it is harder for an attacker to launch an attack.
The above factors are necessary while assessing critical vulnerabilities in any device.
Prioritizing Vulnerabilities:
After performing scans on all IT assets and their networks, the final analyzed report helps to prioritize vulnerabilities. The process ranges from the complexity of the environment to various available IT security data points. Some of them are as follows:
Prioritization by Vulnerability Severity:
Most business organizations rely purely on the severity level of the risks to mitigate them. The CVSS score is one of the popular standards to represent the severity of the risks which includes critical vulnerabilities at the top. The score has four scales: critical, high, medium, and low. IT experts perform the remediation efforts as per these severity data.
Incorporating Threat Data to Prioritization:
Security checks database stores the data that explains the way hackers use vulnerabilities to exploit an asset. This information is analyzed and taken into consideration while applying various prioritization methods. Identifying and defining several past security threats also helps prioritize the severity level. The information about assets also plays the most vital role in deciding the criticalness of the risks.
The availability of the vulnerability database decides the accuracy of the prioritization techniques. Larger the databases of security checks, the higher the accuracy of the assessment. The final reports also need re-evaluation from time to time as per the newly updated assets in the network.
Remediating Vulnerabilities
The vulnerability management software offers various techniques to mitigate the possibility of an attack in an organization. However, IT security experts, system and application owners use solid prioritization policies to determine effective vulnerability remediation methods. It varies depending on the complexity of security gaps.
Patching: It is one of the remediation solutions performed to fix security gaps in an application. Generally, software vendors release updates in the form of patches for a particular application used to repair a vulnerability. The patch also offers information on how an attacker may exploit a vulnerability. Therefore, such critical security issues are patched before being used for compromising the IT assets.
Mitigation: The possibility of the threat is minimized or made almost negligible during the mitigation process. The method is beneficial only when a patch for a particular vulnerability is unavailable. It is usually a buying time strategy for an enterprise when the required non-security or security patch is missing. As a result, it will be a more challenging target for an attacker to exploit the vulnerability. The best possible mitigation efforts are as follows:
- An enterprise can choose not to indulge in certain activities to avoid any exploit that causes danger to the business.
- Continuously monitoring the changes in the impact of the associated vulnerabilities
Reporting Vulnerabilities
A compelling reporting process involves various ways to represent the vulnerability assessment software data. The report is essential to effectively address multiple security gaps in a business environment. It also helps evaluate the effectiveness of the vulnerability management program.
The key findings concerning assets, flaws, and overall risks help IT teams determine the best remediation techniques. Today, an enterprise can view these comprehensive in-built reports in a single cloud console and find solutions to various cyber security concerns. As a result, it amounts to the fact that vulnerabilities are remediated with limited resources and efforts.
How SanerNow Automates Vulnerability Management Process?
SanerNow vulnerability management platform is an integral part of the Cyber-hygiene platform. It offers simplified vulnerability management process steps essential for today’s complex IT surface.
Industry’s Fastest Vulnerability Scans
Often, IT security teams complain about the long duration of the scanning process. SanerNow runs the industry’s fastest scans and identifies the vulnerabilities in less than 5 minutes. It allows users to schedule and automate the scan every day using the agents installed on all devices. These agents also take up the role of network scanner to scan vulnerabilities across all IP-enabled devices. Thus, making vulnerability scanning a continuous process.
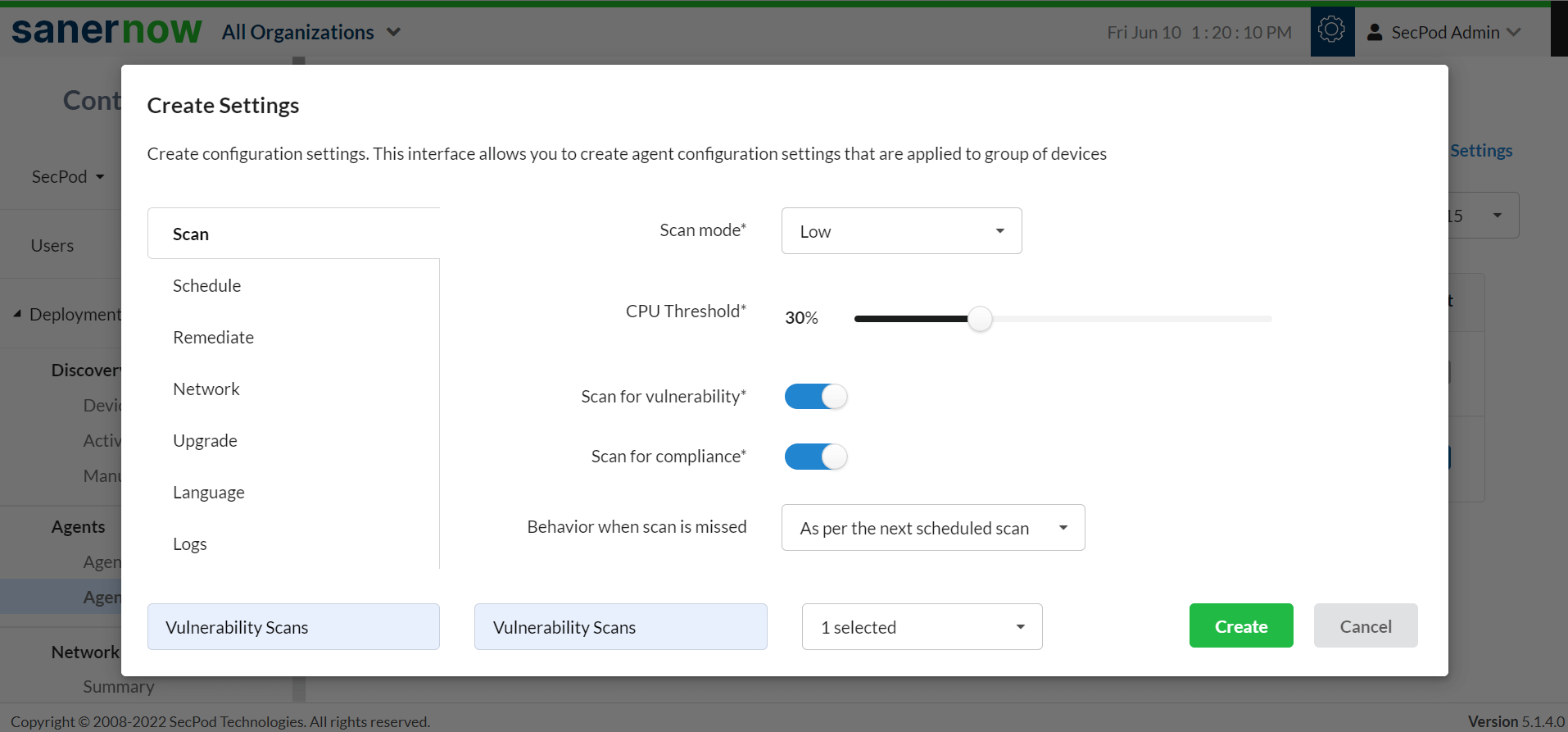
Powered by the World’s Largest Vulnerability Database
It is backed by the world’s largest home-grown vulnerability database. The database is built over years of security research, and it consists of more than 175,000 checks. It is updated daily to ensure accurate vulnerability detection with zero false positives.
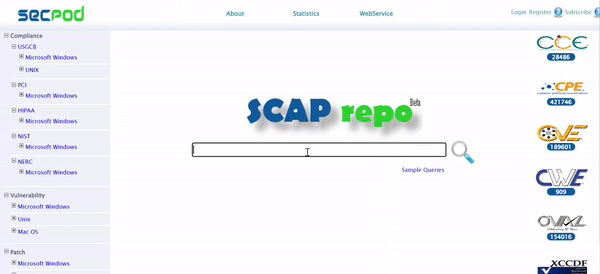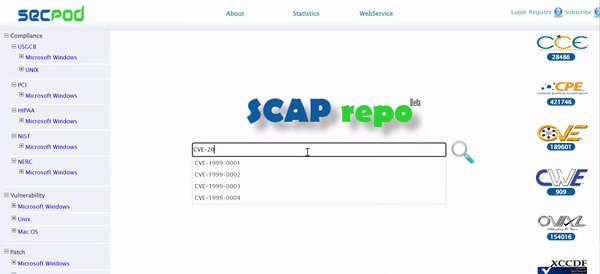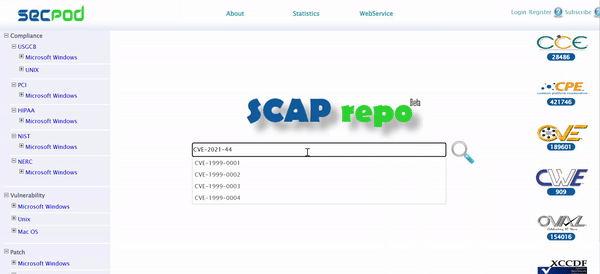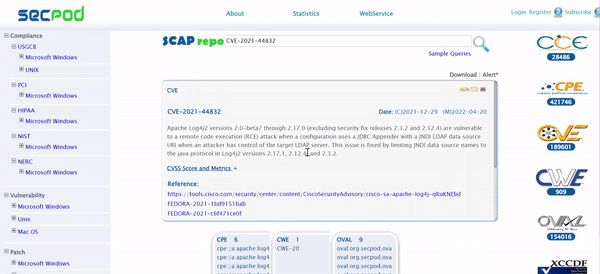
Prioritization and Remediation
Addressing the less critical vulnerabilities may limit the resources required to resolve high critical ones. And it provides an opportunity for an attacker to exploit the network, causing damage to the entire business. Therefore, SanerNow assesses the risks and prioritizes them as per the severity level. IT security experts can use these data and effectively employ their company’s resources during remediation.
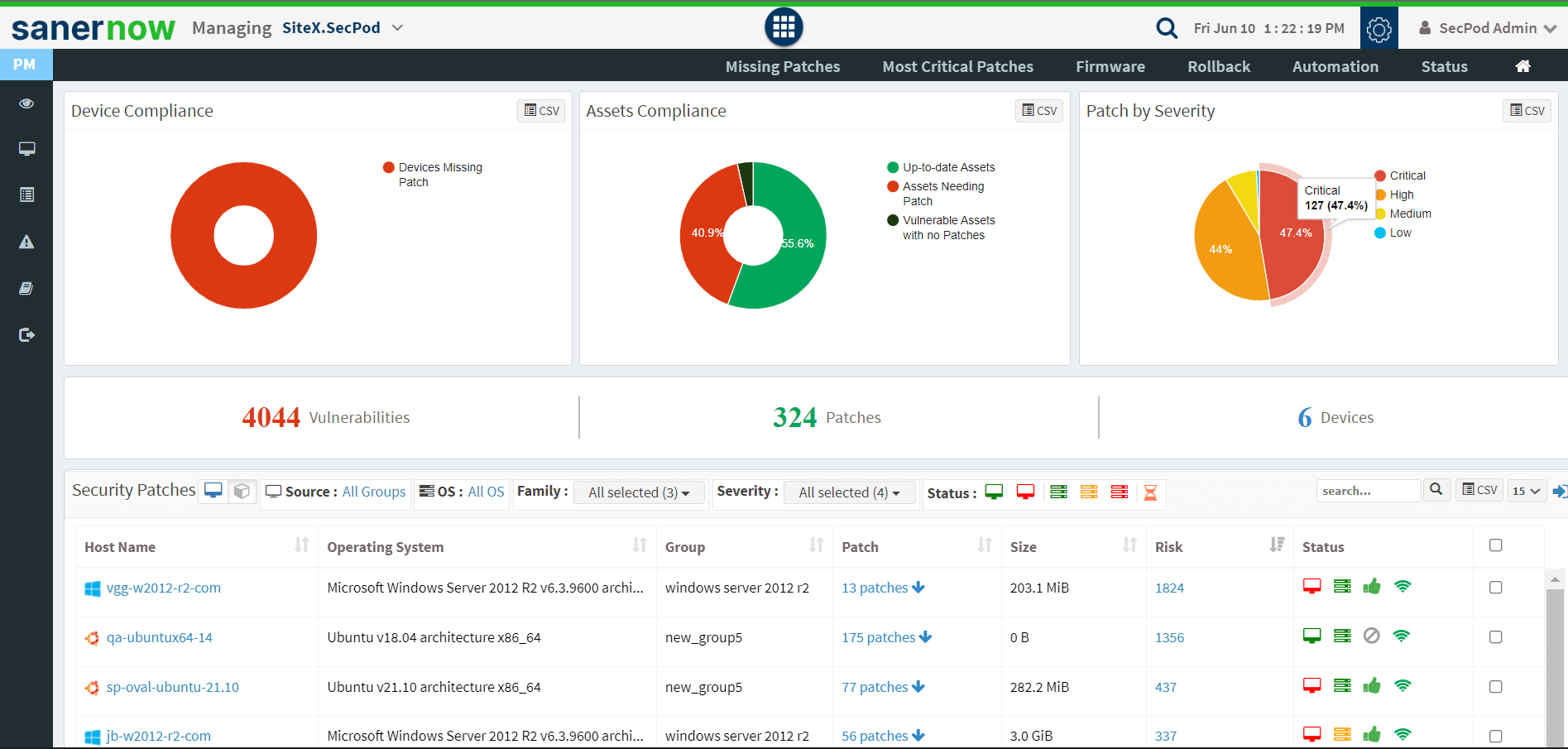
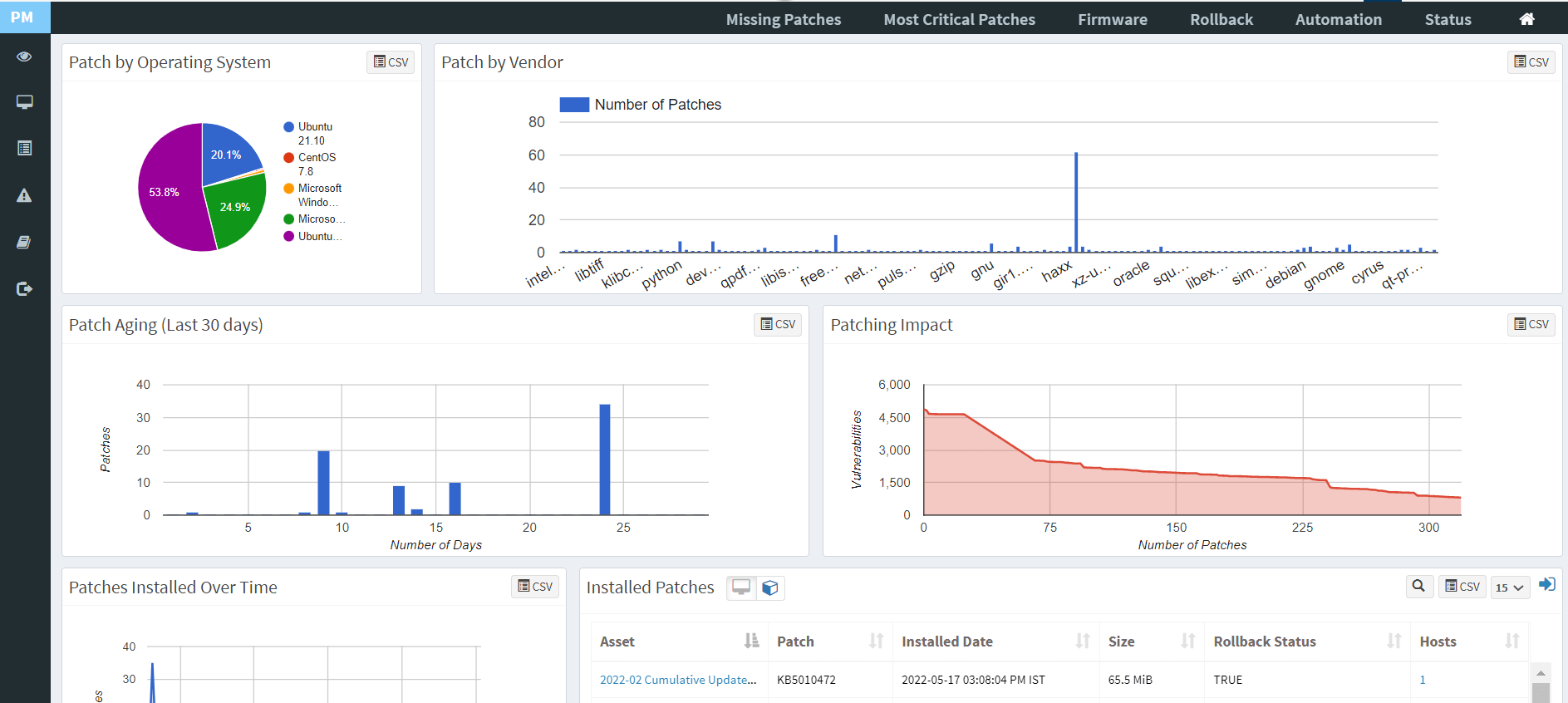
Integrated Patch Remediation
SanerNow’s integrated patch management solutions allow IT teams to remediate vulnerabilities from a single cloud-based console instantly. In addition, it supports patching for all major OSs and a variety of third-party applications.
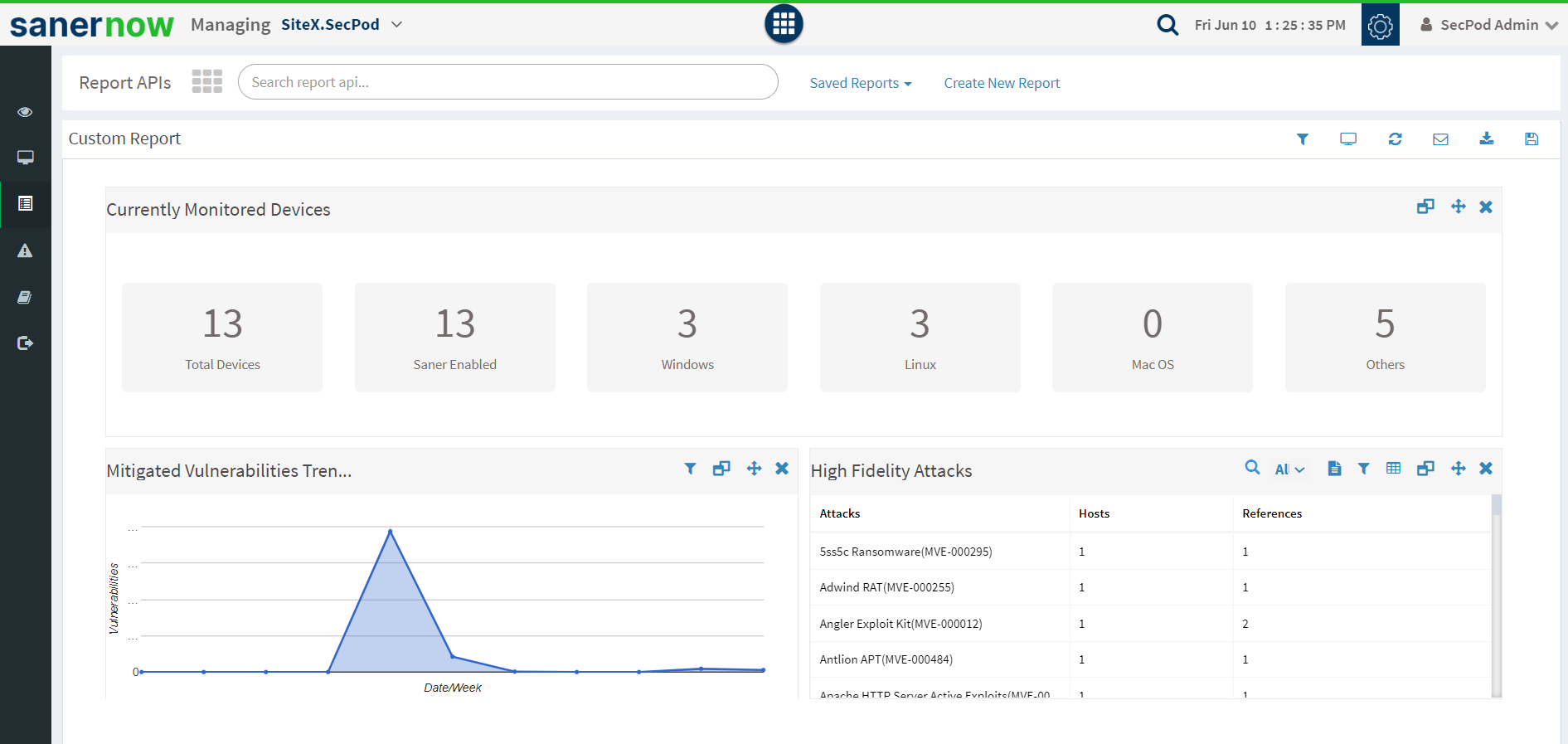
Insightful Customized Report
IT security teams can easily extract in-built and customized reports of the vulnerabilities to their mail. IT teams can assess these reports and make strategic decisions while managing vulnerabilities.
The above vulnerability management tool from SanerNow will help you manage the attack surfaces effectively and keeps your network a step ahead of cyberattacks.


