SanerNow
One Platform to Prevent Cyber Attacks
Take Control Of your Attack Surface with Continuous, Automated, and Advanced Architecture.

Just What You Need for Complete Control Over Distributed Diverse Infrastructure
The First Truly Unified Cyberhygiene Platform
Get all security risk and compliance controls in one platform like never before. Multiple tools don’t cut it anymore in the current world of increasing attacks.
Remote and Scalable Cloud-based Platform
Secure, monitor, and manage your distributed devices from a centralized cloud-based console. Onboard new devices with ease and scale to any number of devices.
One Powerful Agent, One Console to Rule Them All
Saner Agents installed in heterogeneous endpoints perform all assigned tasks without consuming excessive bandwidth and system resources. Control and monitor every activity from one centralized view. It also provides support for agentless scanning.
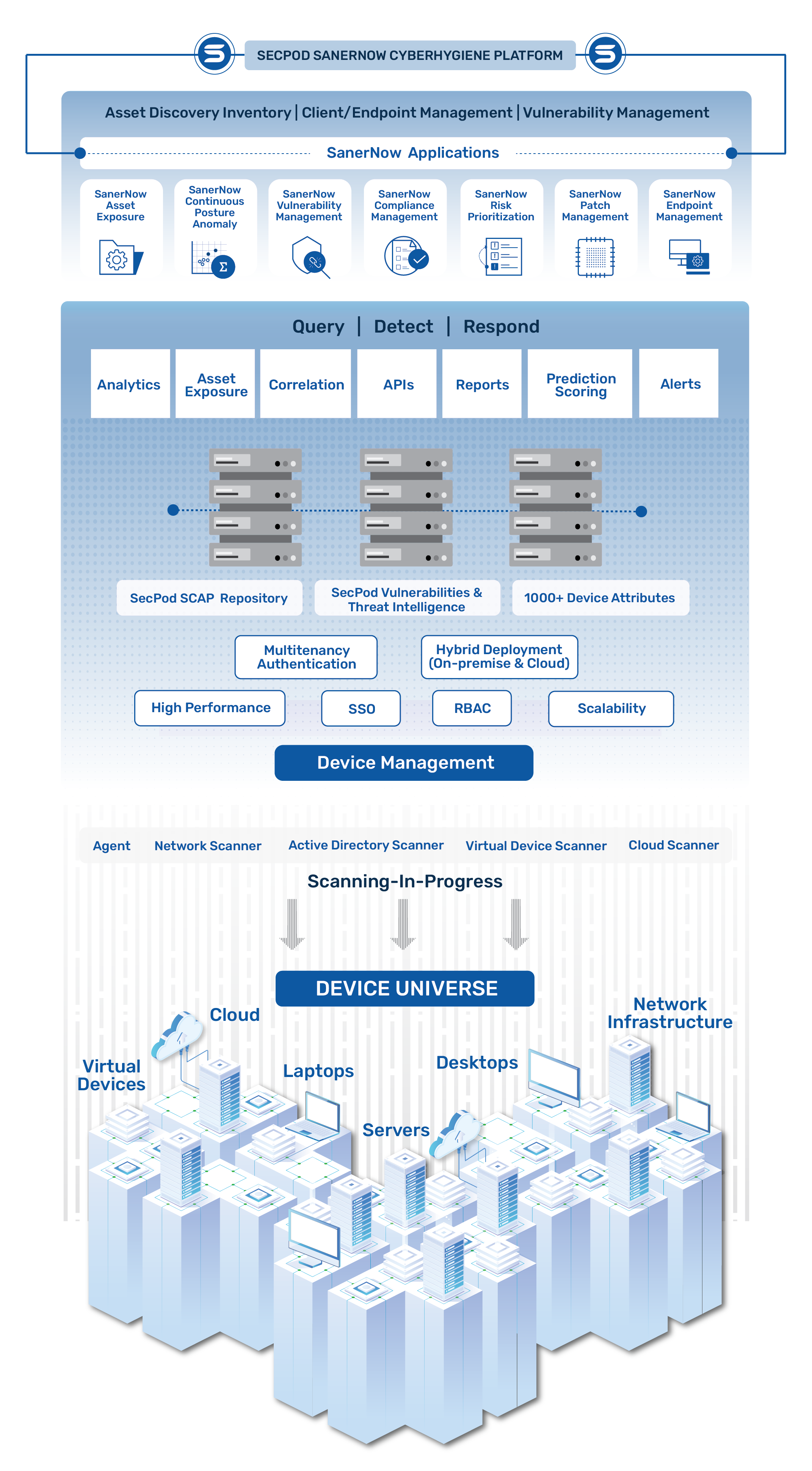
SanerNow Platform
All the Tools You Need to Build a Strong Defense, on a Single Natively-Built Integrated Console
Choose what you need from the ever-growing, vast collection of tools on the SanerNow and stay ahead of attackers. Visibility, Detection, Prioritization, and Remediation controls built on an integrated platform.
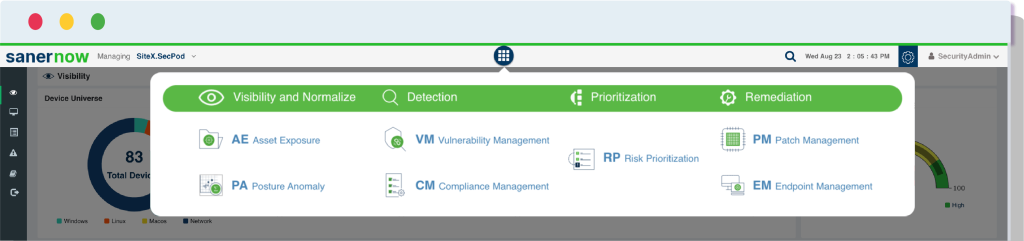
Visualize & Normalize

SanerNow
AE
Continuously monitor IT assets

SanerNow
PA
Take control over attack vectors
Detect & Prioritize

SanerNow
VM
Detect CVEs and other risks

SanerNow
CM
Achieve audit-ready compliance
Remediate & Mitigate

SanerNow
PM
Patch OSs & 3rd party applications

SanerNow
EM
Harden devices beyond patching
Cloud-First and Fully Integrated Platform
Implement end-to-end Continuous Vulnerability Exposure Management operations with a cloud-first fully integrated platform comprising of modular applications designed to build solutions for information security and infrastructure operations teams.
Simple, Continuous, Automated Approach
Easy-to-use, centralized console to reduce the complexity of vulnerability management workflows. Automate every vulnerability management task and continuously monitor the IT infrastructure to strengthen security posture.
Powered by SecPod Research Labs’ Intelligence
SanerNow is fuelled by the Security Content Automation Protocol (SCAP) repository, the world’s largest world’s largest library of 175,000+ security checks. The repository is developed by SecPod Security Research Labs and is continuously updated daily.
Global Enterprises trust SanerNow to Secure their Dynamic IT Environment
– Pradeep B
Consultant, NCIIPC, Govt. of India
– Ernest Darko Mensah
Managing Director, Spearhead Networks MSP
SanerNow has multiple modules like patch management, vulnerability management, compliance management, EDR, software deployment. Today, with rise of cyber risks it’s very important to have a single tool/console to get a visibility into all modules. It’s easy to identify, detect, and patch at the same time.
– Sumit Birajdar
Infosec Manager, Acko General Insurance
Out-of-box Capabilities Pioneering the Technology Innovation in Vulnerability and Exposure Management
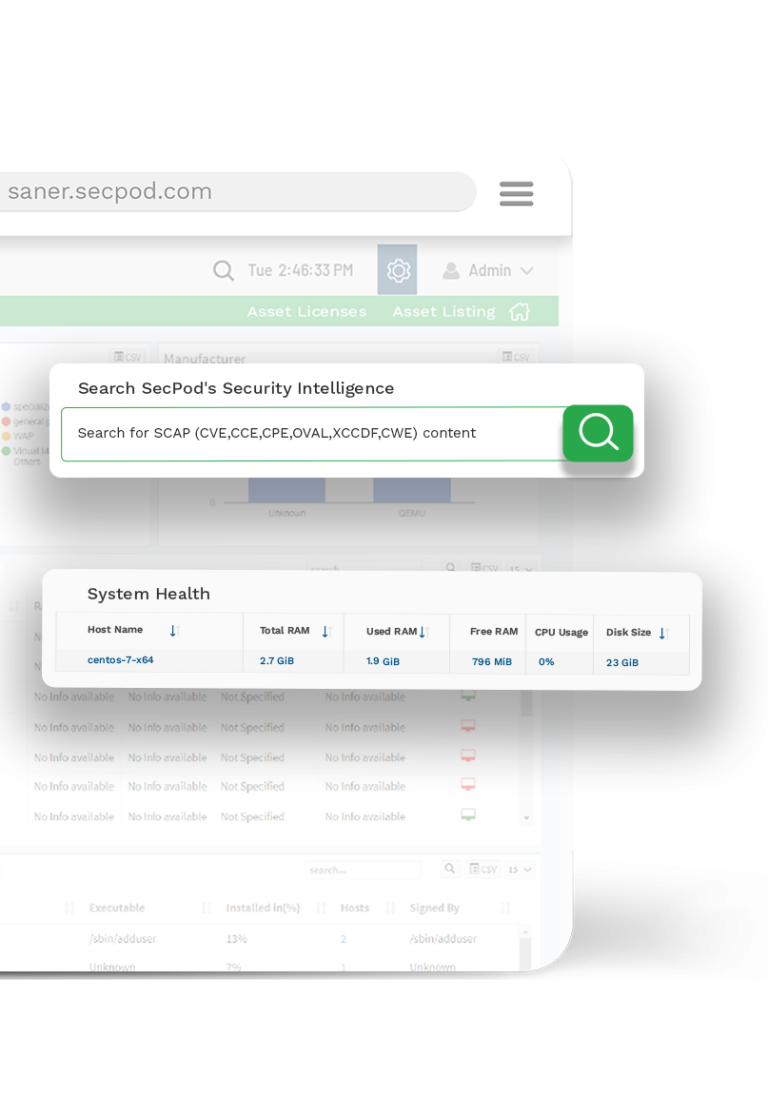
Supports Natural Language Search Queries
The innovative metadata model of the platform supports instant searches using unstructured natural language queries. SanerNow is the only fully compliant platform with well-established standards like SCAP & SOC II.
Multi-tenant Support With Segregated User Data
Efficiently manages multiple business units and system users with a single server. Neatly segregates business users’ data and offers the ability to create various user roles with defined access rights to manage different areas of a corporate network.
Seamless Integration and Interoperability
The flexible architecture of the platform allows integration with various systems. The REST APIs enable access to all collected data from endpoints and supports search queries.
High Performance Scalable Architecture
The platform is highly scalable with a BigData architecture, efficiently supporting the management of a large number of devices through a single server without performance degradation.
Protects BYOD, Remote Office and Transient Devices
Ensures security of organizations’ devices across perimeter limits. Provides efficient protection and control of transient, remote, and BYOD devices from a centralized console.
Robust, Natively Built, and Truly Integrated Solution
SanerNow Cyberhygiene platform is built completely in-house to provide a truly integrated solution. All security tasks can be easily performed from a single place without having to juggle different tools.
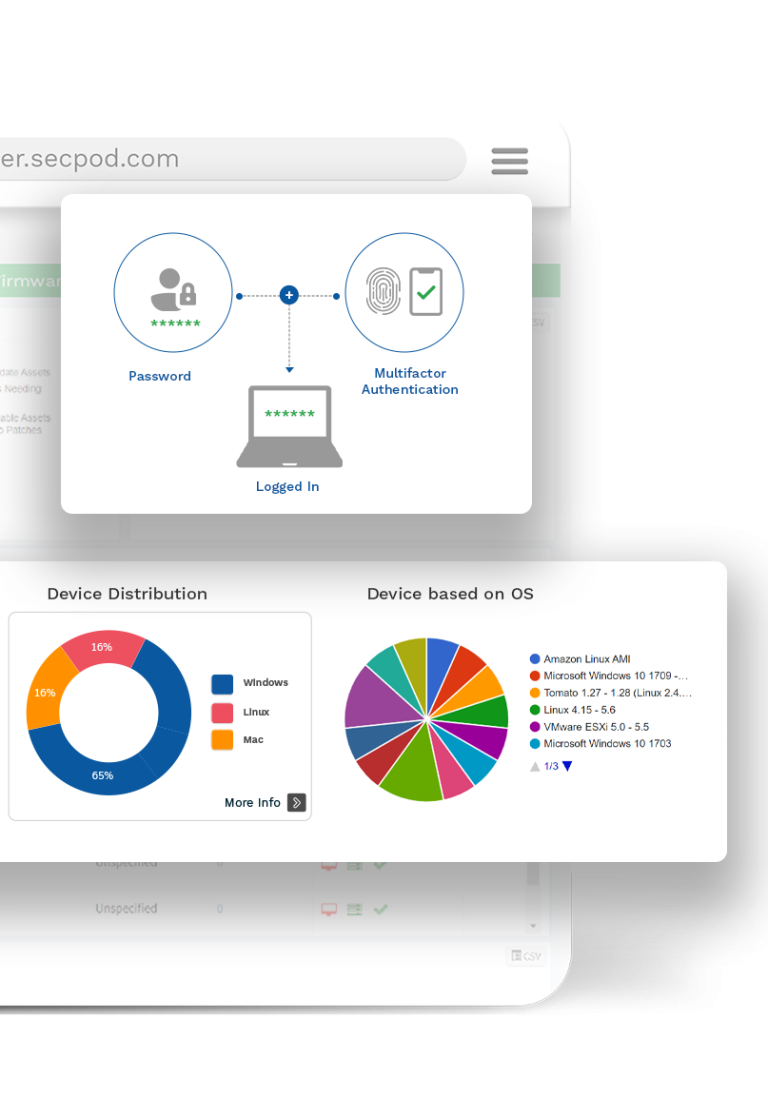
Provides Multi-factor Authentication
The platform provides multi-factor authentication to protect the SanerNow account and add an extra layer of security.
Operates on a lightweight Agent
SanerNow platforms work on a single, lightweight, multifunctional agent which weighs less than 20MB and executes all the tasks. The agent also takes up the role of network scanner and saves cost on performing additional hardware.
Real-time Communication with Distributed Devices
SanerNow allows you to talk and respond to your devices anytime and anywhere in real-time. You can run on-demand operations and establish real-time communication with your organizational devices.
Leverage Machine Learning to deep learn IT
SanerNow analyses various parameters in the network and uses machine learning concepts to provide deep insights into the IT infrastrucre and discover outliers.
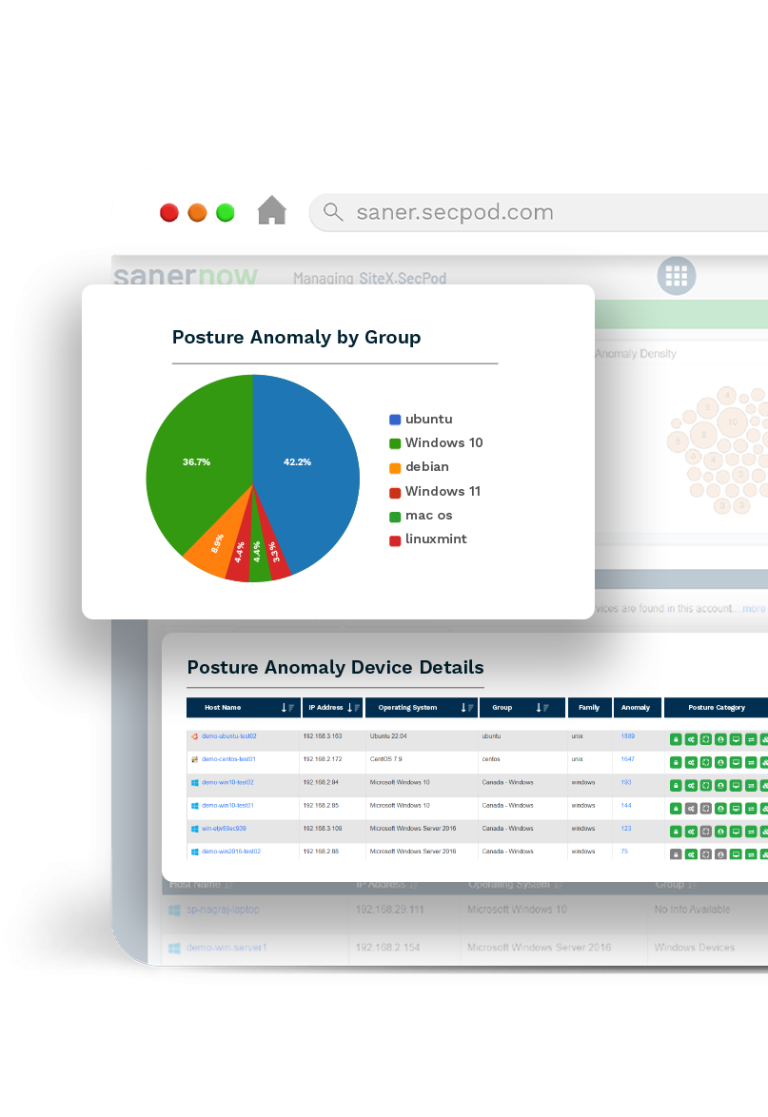
Rule & Trend based Analysis to Discover Anomalies
SanerNow uses rule and trend-based analysis where it collects some parameters over a period to spot any aberrations or abnormalities in regular pattern.
Deviation Computations of Standard Configurations
SanerNow uses 40+ checks to assess if configurations are set differently from others. Through this it identifies the deviated configurations that needs to be looked upon immediately.,
Key Resources
Join the Reinvention of Vulnerability Management
Get free access and try it yourself.






