SanerNow for IT Teams
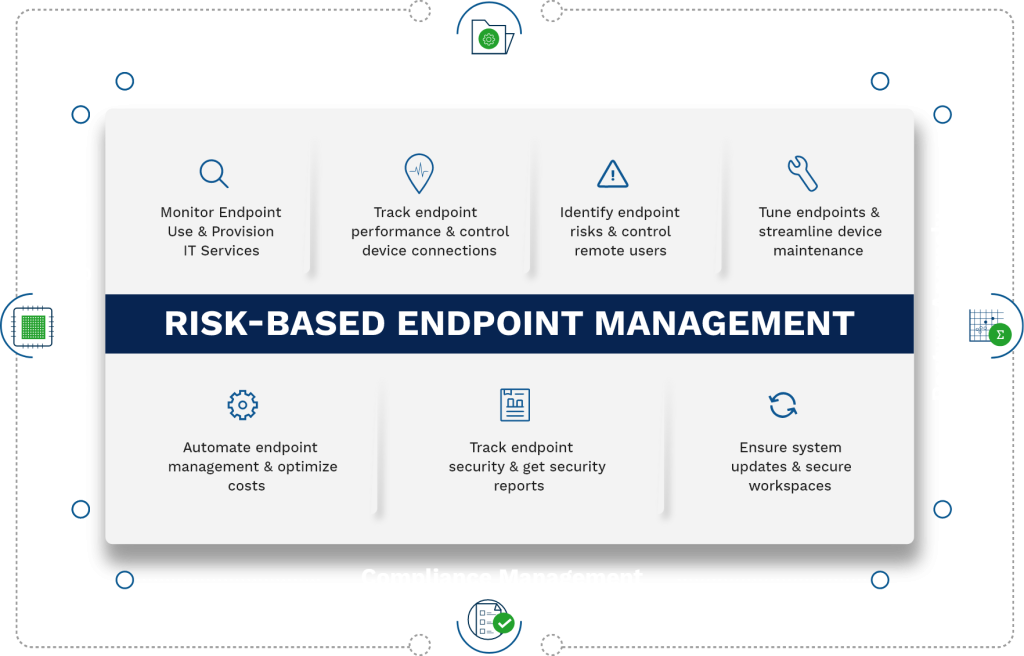
Risk-based Endpoint Management




Automate Endpoint Management. Ensure Zero-Touch Deployment, Improve Visibility,Enhance Security, & Optimize Operations.
Automate deployment/uninstallation of multiple business applications & productivity tools, help business functions monitor/address IT issues, automate workflows to onboard/offboard employees, automate endpoint maintenance & updates, including system tune-up.
No need of on-prem hardware, automation of security & maintenance tasks to reduce downtime, reduce the need for multiple solutions & administrative overheads by zero-touch deployments for instant availability.
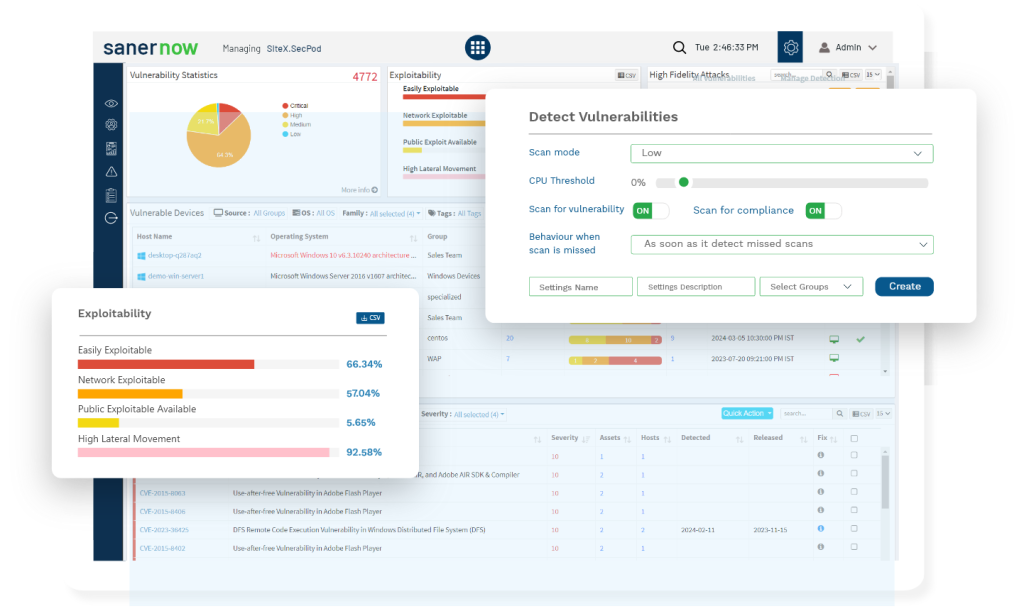
Detect vulnerabilities & deploy patches to every distributed device, view latest & missing patches, test & approve patches, roll back error-prone patches, & prioritize deployment of patches. Get the latest patch from approved vendors in 24 hrs.
Get a single, unified console to manage devices, reduce IT staff workloads by automating routine tasks, track hardware/software to manage licenses, set alerts, get detailed insights and reports to track device performance, usage and security posture.
Accommodate any number of endpoints & users, cloud console to manage wide range of services based on business demands to maintain agility, manage various groups of device types across functions and networks.
Protect devices by remediating vulnerabilities & misconfigurations, including network vulnerabilities. Get enterprise-wide visibility of anomalies, shadow IT, data exposure, suspicious traffic, processes or connections, including malicious devices & software & remediate them.
Cloud Console for Continuous Endpoint Management
Asset Exposure Management
Posture Anomaly Management
Patch Management
Endpoints Controls Management
Compliance Management
The Right Fit to Manage your Enterprise Endpoints
Preventive tactics to drive efficiencies & ensure faster issue resolution
Oversee the utilization of devices across the network, efficiently deliver & manage IT services for end users, deploy or uninstall applications, stop or start services, configure endpoint settings, manage hardware resources, grant user access & permissions

Gather telemetry data from devices to assess endpoint health, performance, and security to investigate & troubleshoot them proactively without interrupting users. Block malicious apps and unauthorized devices, including USBs & peripheral devices.

Detect endpoint security risks across networks by building custom queries from a range of probes and attributes. Use these queries to enforce IT policies & compliance standards and gain visibility to every endpoint activity. Stay remote-ready, Reduce administration overhead in managing remote users & easily manage distributed IT environments

Cloud-based centralized console for IT admins to reduce downtime, inspect system health, fine-tune endpoint performance by cleaning registries & hard disks, purging rare or unused files, troubleshoot endpoints in real-time, and track device locations

From heterogeneous OS deployment or updates, application whitelisting or blacklisting to optimizing the functioning of security controls, troubleshooting systems, continuous endpoint monitoring, installing patches, monitoring software usage, running compliance scans, patching vulnerabilities, and misconfigurations. Improve IT team productivity & streamline endpoint operations to reduce costs.

Guarantee software and hardware updates, including service packs & firmware patches. Control deployment of software, debug and resolve issues, manage and secure Win, macOS & Linux devices, configure user settings, confirm safer connections to the enterprise network, ensure BitLocker status in always-on to secure hard drives & automate patch management.

Ensure every endpoint security control is functioning, discover attack vectors, detect and remediate security deviations, monitor anti-virus status, check firewall functioning, verify the status of system files & registry keys, including the existence of rogue processes or devices, quarantine or isolate devices and get insights from customizable reports for audits.

From Executing daily IT Tasks to Mitigating Security Risk, the Solution Manages More Than 100M Endpoints Worldwide
Continuous endpoint risk management
Patch compliance across endpoints
Endpoint audit readiness
Increase in execution speeds
Cost optimization by reducing TCO
Accuracy & adherence to security goals