Linux Patch Management
- Linux Patch Management
- What is Linux Patch Management?
Like patching operating systems, Linux patch management is a process of managing patches (or) updates in Linux systems. Patch Management Tool for Linux starts with scanning every Linux endpoint, detecting missing patches, downloading from their respective vendors, and deploying them.
Patches should be updated and applied regularly to minimize the risk of the surface attack. Manually patching Linux systems are sophisticated and tedious task; it will be helpful if one uses an automated approach to patch them using an automated patch management software.
As we discussed, “What is Linux patch management?” let’s now understand “How important is Linux patch management?”
Benefits of Linux patch management
Security:
It’s the top-most goal of every organization. In this modern era, security breaches are widespread, and keeping your organization safe is always important.
Breaching Linux systems is hard, but it will still be vulnerable to installed applications with root access.
Productivity:
System crashes still happen due to outdated or defective software, leading to lower productivity. Keeping your system updated with patch management software will reduce downtime.
Compliance:
Few organizations follow strict regulations for keeping their Linux devices up to date to avoid threats. Not sticking around these regulatory standards would lead to penalties.
Feature updates:
Patching is not only about fixing bugs or critical vulnerabilities. Patches also provide new features that increase the application’s performance.
Manual Method of Patching Linux Systems
Due to the various Linux distributions, manually updating Linux devices is very complicated and tedious. Using patch management tool can simplify this process. Here is a list of a few commands that must be used to update Linux systems and their respective distributions manually:
Distribution – Red Hat and Fedora-based Linux system patching
Commands –
- To check if there are any updates: yum check-update
- To update the whole system: yum update
- To run an update on a specific package: yum update <package-name>
- To revert from the previous patch: yum history undo last
- To completely uninstall a package: yum remove <package-name>
Distribution – Debian-based Linux system patching
Commands –
- To verify and sync packages with sources: apt-get update
- To download and install software packages: apt-get upgrade
- To update a current package to the latest one: apt-get install <package-name>
- To remove an installed package: apt-get remove <package-name>
Why is Patch Management in Linux More Complicated than in Windows?
Patch management in Linux is more complicated than Patch management in Windows because of the distributed nature of Linux OS. If a patch has worked ix n Red Hat, it doesn’t necessarily mean it should also work in centos, Debian, or any other Linux distribution.
Also, windows are more flexible, and its admins have more control over where to deploy patches. In Linux systems, users usually deploy patches using a terminal that might result in errors/blunders.
Best practices of Linux patch management system
Patching the right Linux system and version:
Typically, it involves scanning Linux systems for missing patches, downloading them from vendor sites, and deploying them.
Since Linux has distributed nature of OS, patches designed for one particular distribution will not apply to other distributions. Therefore, you will have to ensure patches are applied to the correct version of OS distribution.
Implementing the right Linux patch management software:
Linux distribution vendors have their own way of distributing patches. Though they might look similar, but they are quite different from each other.
A good Linux automated patch management software ensures it supports all different versions of Linux patches and can automate the whole Linux patching process. It will be beneficial if it has cross-platform support and can patch other OSs also, apart from Linux.
Always test patches before deploying them:
Testing Linux patches before deploying them will reduce error and saves time in rolling back patches that might cause an issue.
After testing and deploying patches, audit them to confirm that patches are deployed and that all the systems are up to date.
Stay updated on vendor announcements:
It is an essential step of the patch management process. If you have a Linux patch management tool, the software might automatically download and store the latest patches.
But managing the latest patches of Linux systems can be very hectic without a proper tool. Since the patching process would require you to go to the vendor website, download every single patch manually and deploy them, it is a lot more time-consuming and can be more prone to errors.
Apply patches as quickly as possible:
The need for patching is to remediate vulnerabilities instantly. It’s pointless to detect critical vulnerabilities and deploy patches weeks later.
To protect organizations from cyberattacks, it’s always a good idea to apply patches as soon as possible.
Five things to Look for in Linux Patch Management Software
- There should be support for all major Linux distributions and versions.
- All the patches should be automatically downloaded and stored from their respective vendor’s websites.
- Linux patching process should be completely automated.
- The Linux patch management software should always test and deploy patches.
- Additionally, Linux patching software can instantly remediate vulnerabilities with integrated vulnerability management.
Linux patch management with SanerNow
SanerNow patch management platform proactively helps you to manage patches. You can manage most-critical patches, missing patches, patches based on OS, security patches and much more in a single unified dashboard. It’s an automated process where it will detect, prioritize, and deploy missing patches.
With SanerNow, you can get insightfully customizable and auto-generated reports! It has the world’s largest security intelligence feed with 175,000 continuous checks. SanerNow also supports 450+ unique third-party application patching.
Linux patching can be broken down into quick, easy steps with SanerNow:
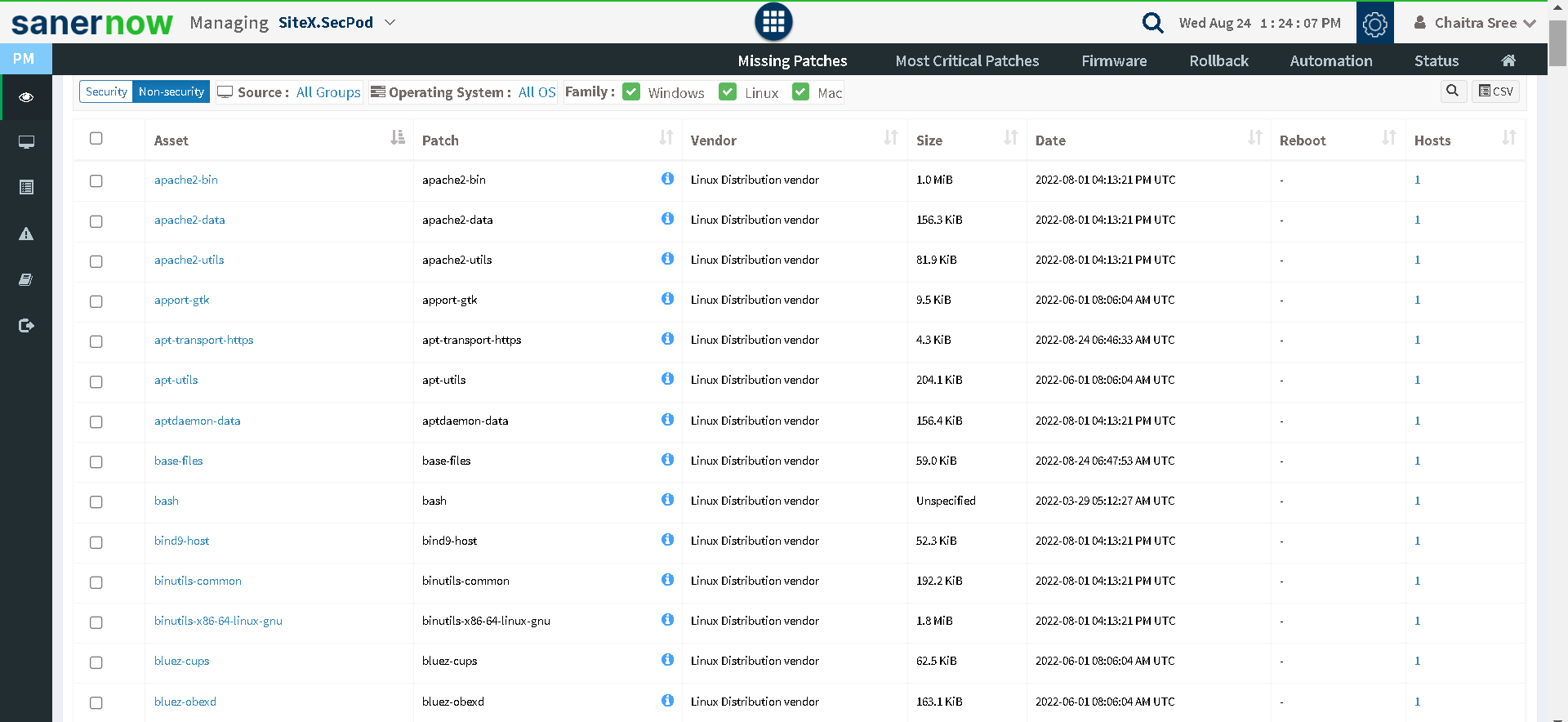
- In the SanerNow Patch Management dashboard, you will be able to find all the missing non-security and security patches present in your organization.
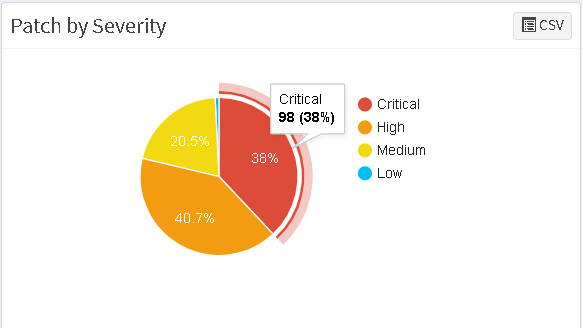
All the patches will be prioritized based on their CVSS scores and severity level so that the most-critical patches can be deployed first.
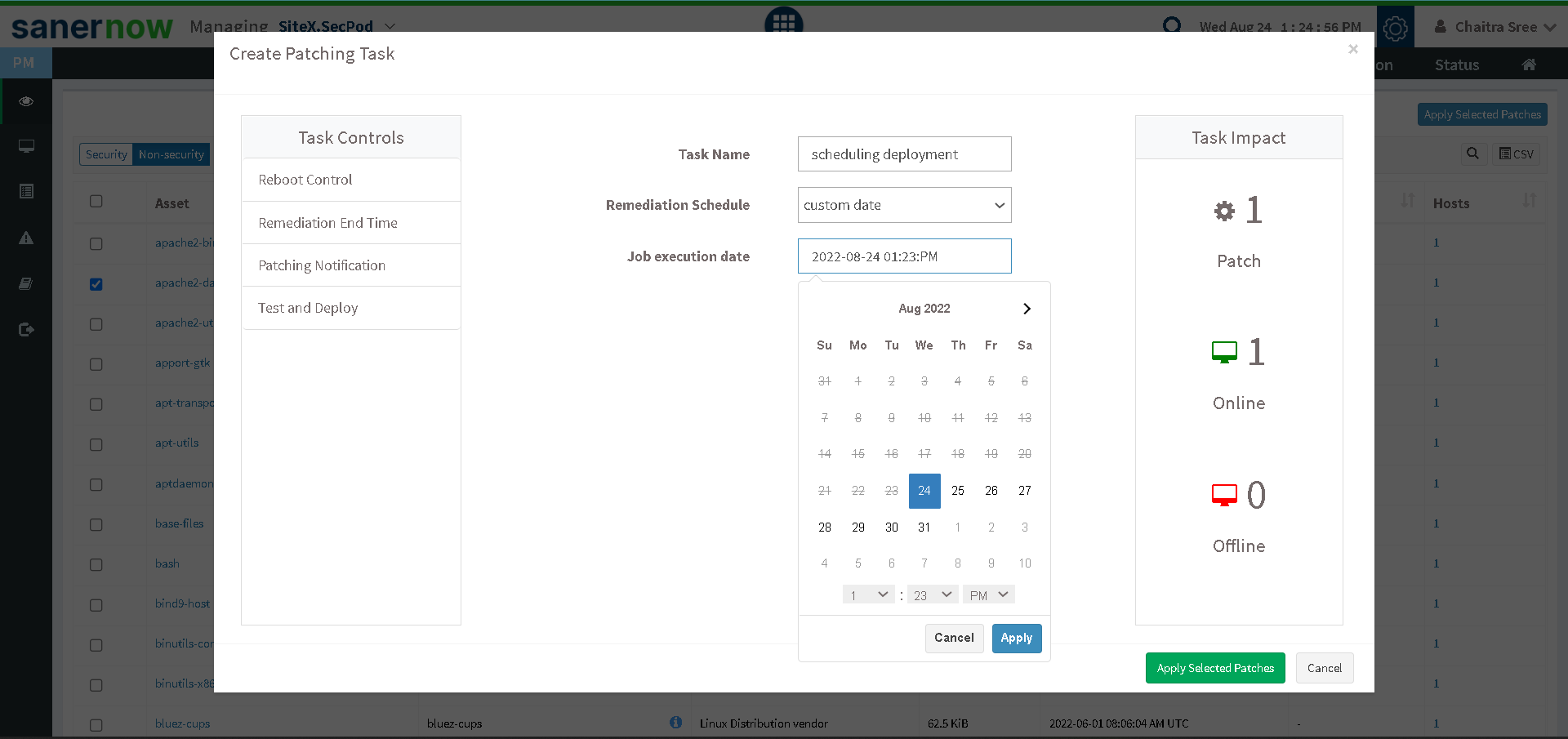
You can schedule deployment based on your requirements.
You can always test your patches before deploying them in your production environment.
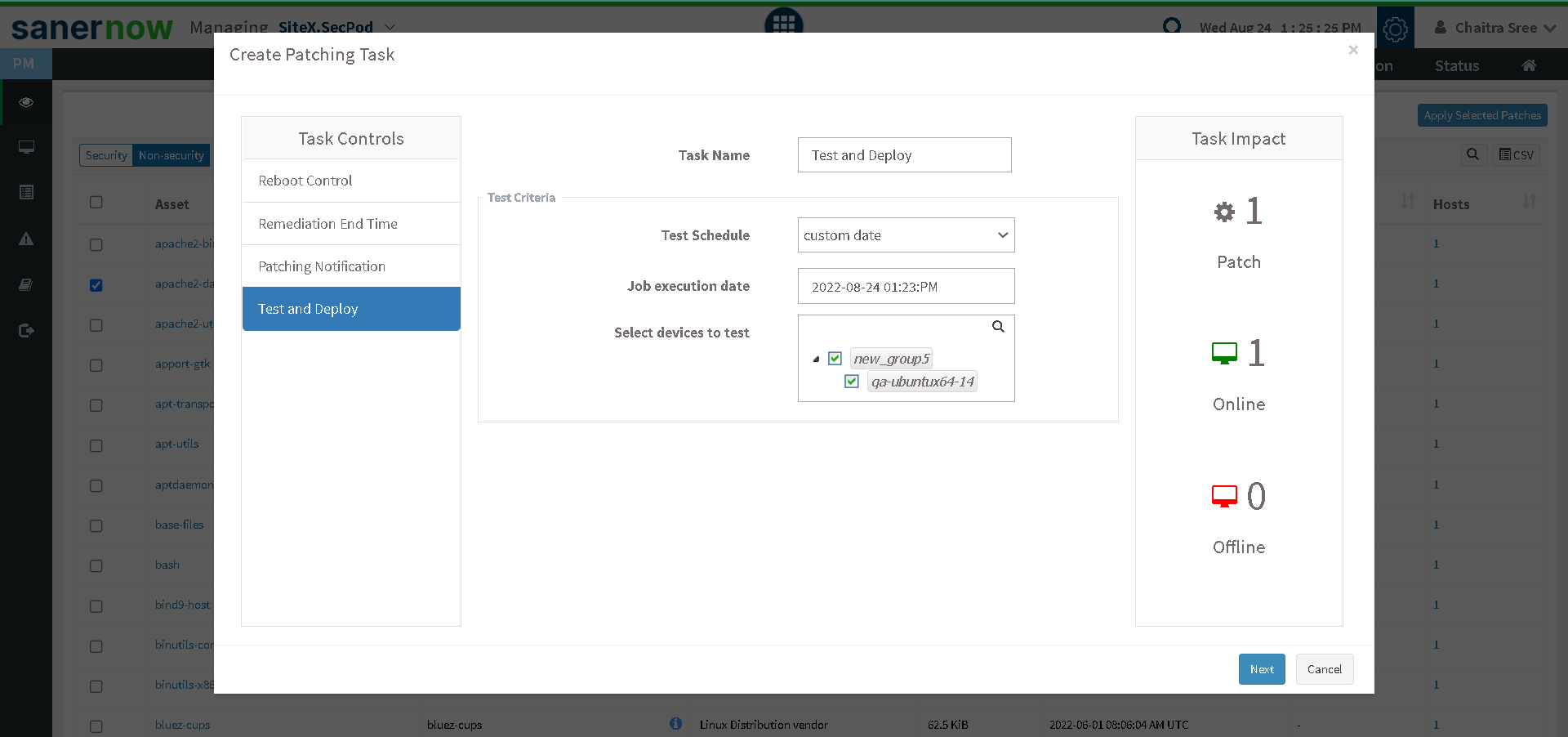
Fig 4: Test and Deploy
In case of patch failure, you can roll back it to the previous stable version.
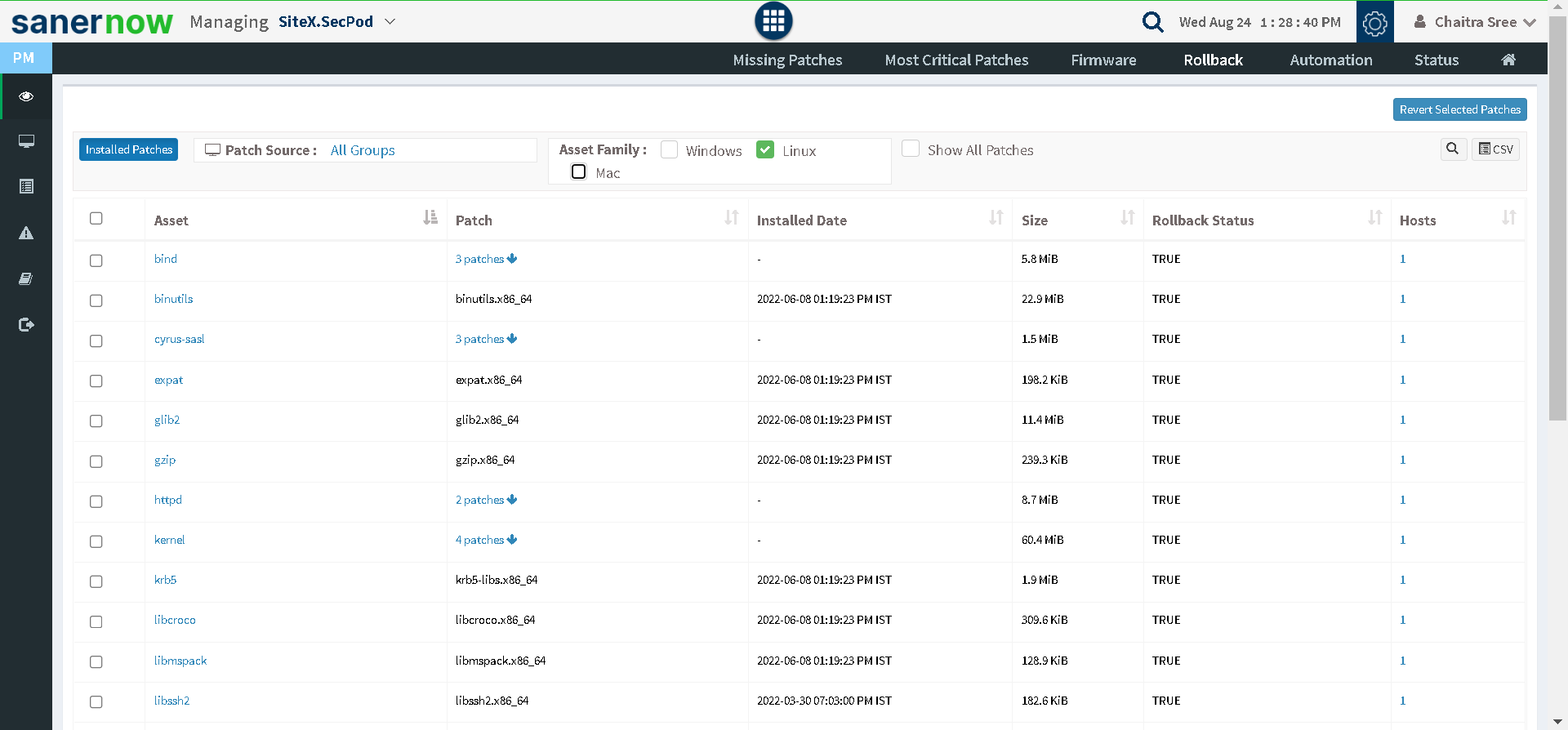
Fig 5: Patch Rollback
You can get insightful canned and customizable reports.
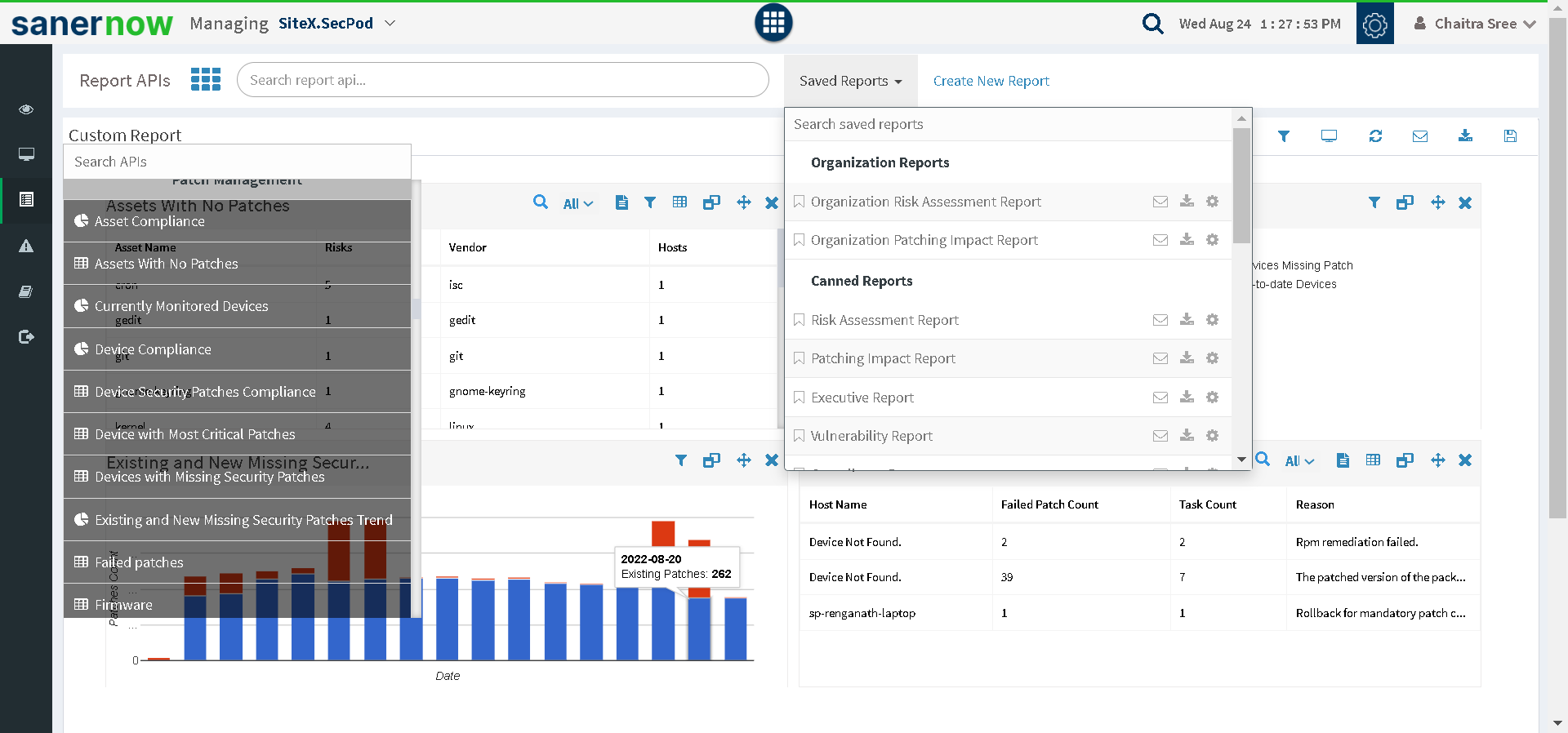
Fig 6: Customizable Reports
Supported Linux devices
- Ubuntu 14.04
- Ubuntu 16.04
- Ubuntu 18.04
- Ubuntu 18.10
- Ubuntu 20.04
- Ubuntu 21.04
- Ubuntu 21.10
- Ubuntu 22.04
- Debian 8
- Debian 9
- Debian 10
- Debian 11
- Amazon Linux
- Amazon Linux 2
- AlmaLinux 8.4
- AlmaLinux 8.5
- Rocky Linux 8.3
- Rocky Linux 8.4
- Rocky Linux 8.5
- Redhat Enterprise Linux 6
- Redhat Enterprise Linux 7
- Redhat Enterprise Linux 8
- Redhat Enterprise Linux 9
- CentOS 6
- CentOS 7
- CentOS 8
- Oracle Linux 6
- Oracle Linux 7
- Oracle Linux 8
- Fedora 27
- Fedora 28
- Fedora 29
- Fedora 31
- Fedora 32
- Fedora 33
- Fedora 34
- Fedora 35
- Fedora 36
- Linux Mint 17
- Linux Mint 18
- Linux Mint 19
- Linux Mint 20
- Alpine Linux 3.6
- Alpine Linux 3.7
- Alpine Linux 3.8
- Alpine Linux 3.9
- Alpine Linux 3.10
- Alpine Linux 3.11
- Alpine Linux 3.12
- Alpine Linux 3.13
- Alpine Linux 3.14
- Alpine Linux 3.15
For complete list visit: docs.secpod.com

