Saner Cloud
Cloud Security Posture Management (CSPM)
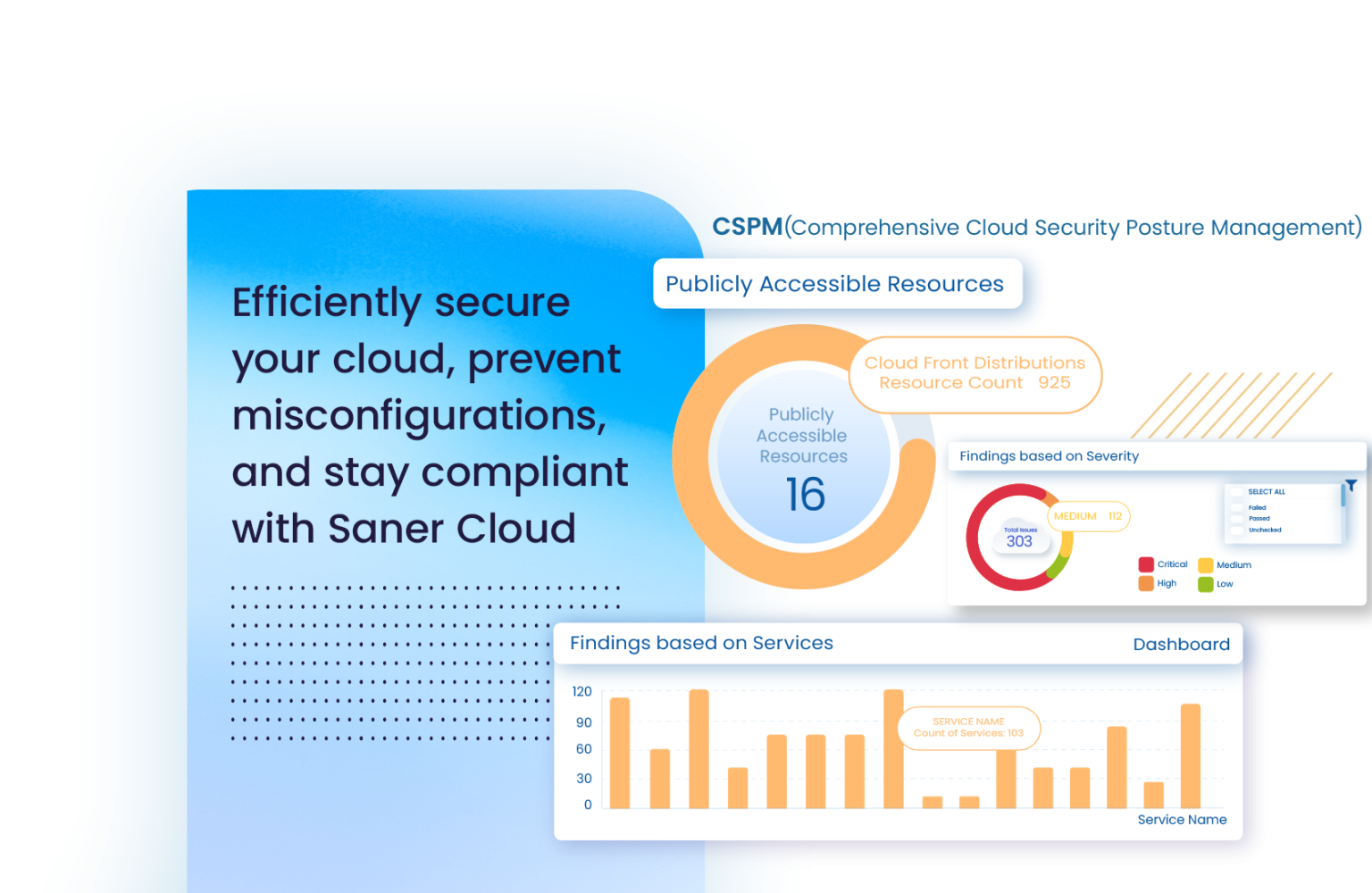
Cloud Security Posture That’s Measurable, Policy-Aligned, and Fast.
Continuous Misconfiguration Detection
Detect cloud configuration issues within minutes using 1,000+ posture rules across AWS and Azure.
Unified Cloud Security Monitoring
Gain consolidated visibility into security posture, risks, and compliance across AWS and Azure.
Automated Risk Remediation
Apply policy-based remediation to fix misconfigurations and reduce manual work.
Why Saner CSPM Outpaces the Competition
Saner Cloud
Posture Evaluation with Benchmark Frameworks
Saner Cloud CSPM uses over 1,000 benchmark-aligned posture checks to evaluate resource configurations across AWS and Azure. These checks validate cloud infrastructure against predefined rulesets that reflect compliance frameworks such as CIS, HIPAA, PCI DSS, and NIST 800-53. Each scan evaluates configuration settings, resource status, access controls, and network exposure to identify misalignments and non-compliance risks.

Severity-Based Risk Categorization
Findings are classified as Critical, High, Medium, or Low based on the risk posed to the cloud environment. Critical findings include unrestricted access, outdated authentication methods, or sensitive data exposure. Each issue includes metadata like resource type, affected service, region, and number of impacted instances to support focused remediation.
Centralized Visibility Across Providers and Regions
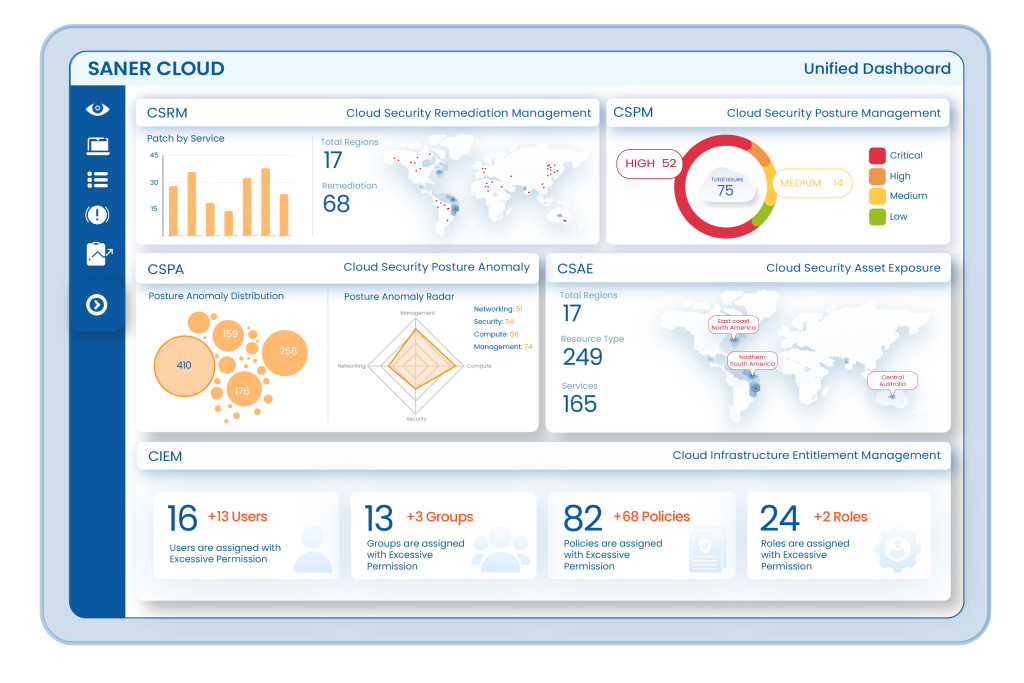
Security teams can monitor AWS and Azure accounts through a unified dashboard. Findings are visualized by region, service, and severity to track deviations and recurring risks. Dedicated views highlight trends across time, allowing teams to identify persistent or seasonal misconfigurations and take corrective action.

Audit-Ready Compliance Mapping
Saner Cloud CSPM maps each failed check to a compliance benchmark and generates exportable reports that include benchmark name, rule ID, service type, and affected resources. Compliance views are structured for audit teams and regulatory reviews. Users can apply benchmarks globally or regionally and assess which rules are failing across accounts.

Security Posture, Compliance, and Risk Remediation in One Platform
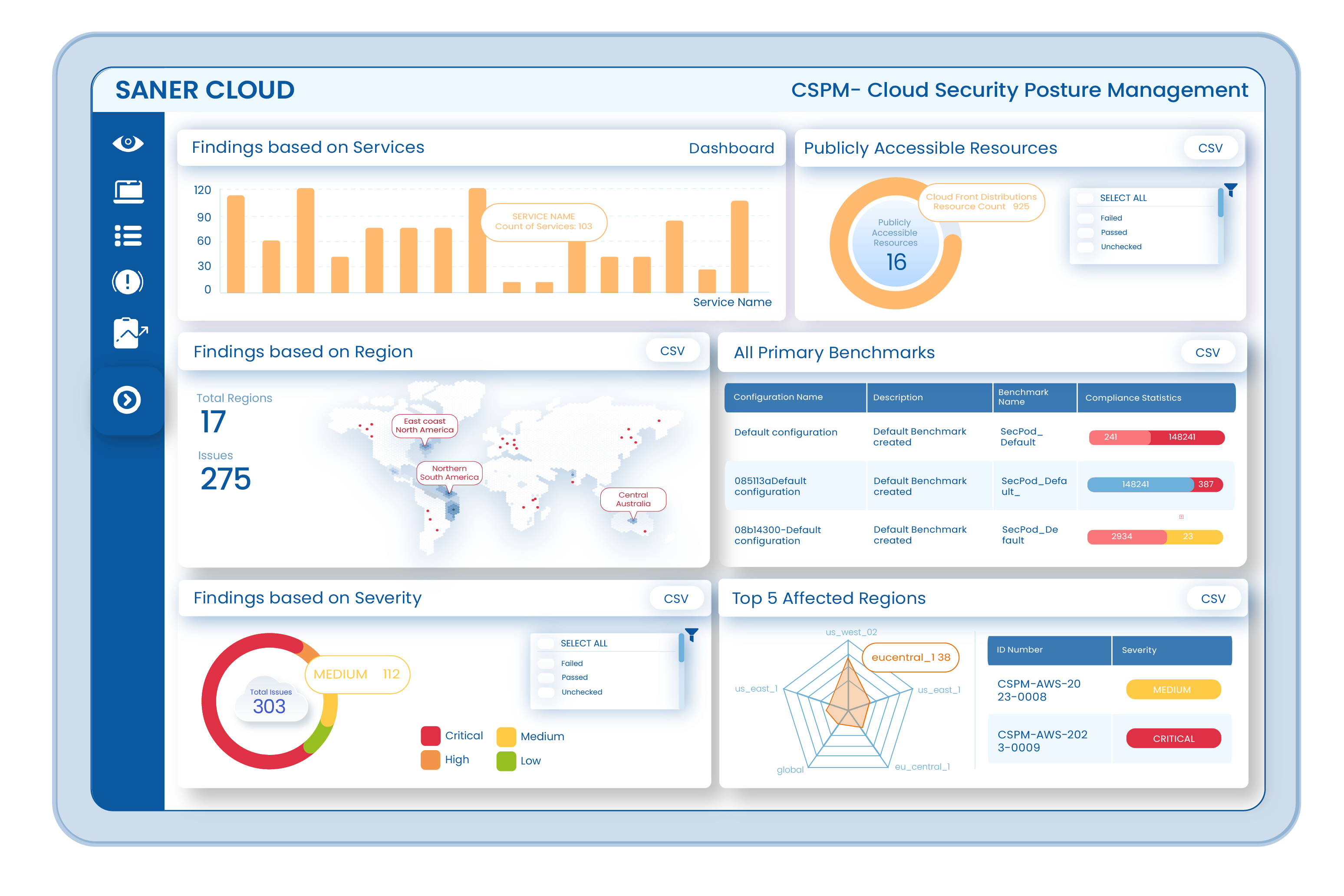
Saner Cloud CSPM performs frequent posture scans using a security ruleset of over 1,000 checks. Resources such as IAM roles, storage buckets, databases, and virtual networks are continuously assessed for policy violations, exposure, and security drift.
Configuration results are mapped to selected benchmarks, such as CIS, HIPAA, and PCI DSS. Findings are marked as Passed, Failed, or Unchecked. A dedicated dashboard block displays results by region, service, and severity to support informed compliance planning.
CSPM calculates severity based on the compliance rule, resource type, and exposure level. The dashboard displays critical findings in a filtered view, so teams can respond to the most pressing configuration risks first. Each finding includes detailed evidence and remediation suggestions.
Clicking the “Fix” icon in the dashboard links to the CSRM module, where users can initiate guided remediation steps. The workflow includes selecting affected resources, applying corrective templates, and scheduling execution. The system tracks job progress with statuses such as Not Initiated, In Progress, or Success.
CSPM surfaces IAM misconfigurations including over-privileged roles, unused credentials, and non-compliant permissions. These are identified through policy analysis and compliance rule violations, helping organizations reduce access risk and policy sprawl.
Each benchmark report includes identifiers, rule titles, service names, region metadata, and number of affected resources. Reports are exportable in CSV format and organized by status, severity, and benchmark association. These help with audit prep, tracking remediations, and stakeholder communication.
Exploring Saner CSPM's Advantage
Saner Cloud CSPM applies its rule library across IAM, compute, storage, network, and monitoring services in AWS and Azure. Each scan flags resource states that violate security baselines and benchmarks. Misconfigurations are visualized with region and account context for operational clarity.
Saner Cloud CSPM tracks changes in misconfiguration patterns, seasonal vulnerabilities, and recurring risks using the Date-Wise Affected Resources Trend feature. These insights help security teams evaluate the impact of remediation actions and adjust posture strategies across AWS and Azure environments.
Remediation workflows in the CSRM module guide users from detection to resolution. Each task includes a job name, remediation ID, selected template, and status view. Security teams can track the outcome of each remediation job, including failures requiring reconfiguration.
Cloud misconfigurations, compliance gaps, and exposure risks are tracked across all connected AWS and Azure accounts. Findings can be filtered by benchmark, region, severity, and service type. This centralization reduces effort in reporting and scaling secure configuration.
Saner Cloud CSPM offers pre-built and customizable benchmarks aligned with CIS, NIST, HIPAA, PCI DSS, and SOC 2. Users can define rule sets per region or globally, apply severity levels, and assign rules to accounts. The dashboard tracks compliance scores and benchmark-specific findings to streamline reporting and remediation.
Frequently Asked Questions (FAQs)
CSPM detects configuration issues across IAM, network exposure, encryption, and public accessibility using over 1,000 rules. Each issue includes metadata such as resource type, affected region, and associated benchmark rule.
CSPM benchmarks map to CIS, NIST 800-53, HIPAA, PCI DSS, and SOC. The default SecPod benchmark includes rules drawn from these standards.
Findings are assigned severity levels based on factors such as affected services, region, resource count, and compliance alignment. “Critical” severity is used for high-impact, high-exposure issues.
No. CSPM supports only AWS and Azure environments.
Remediation tasks are launched from the CSPM dashboard via the “Fix” icon. The CSRM module provides a step-by-step workflow: select resources, apply a remediation template, schedule, and execute. Task status is tracked across stages including in-progress, success, or failed.

Detect, Prioritize, and Remediate Cloud Security Risks in Minutes with Saner Cloud