Microsoft released its monthly (September’s) security update, Patch Tuesday, disclosing 63 vulnerabilities across the company’s hardware and software line. Microsoft September 2022 Patch Tuesday security update is observed to have a sharp decline from last month’s number of issues disclosed by Microsoft.
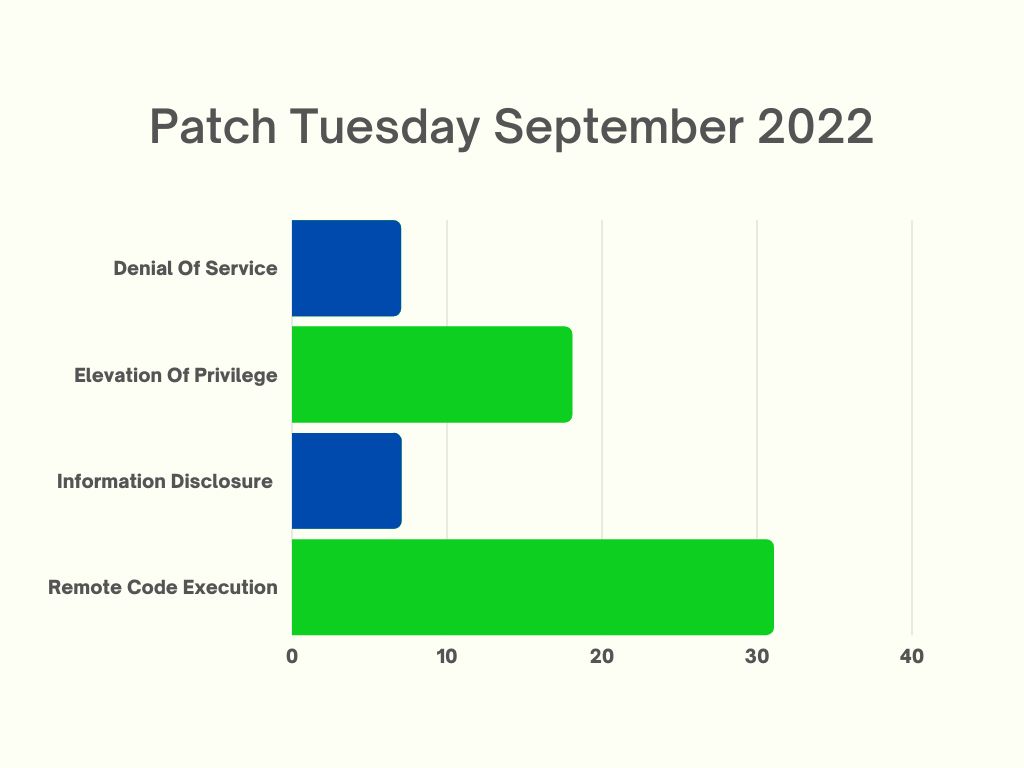
Microsoft’s Security Update addresses five critical vulnerabilities which tend to allow Remote Code Execution which is ten fewer than were included in last month’s patch Tuesday. There are two moderate-severity vulnerabilities in this very release and one low-security issue. It’s important to use a vulnerability management tool for these. The remaining are classified as “Important,” therefore those have Denial of Service (DOS), Elevation of Privilege, Information Disclosure, Remote Code Execution, and Security Feature Bypass per the advisory. A compiled list is available for reference below.
Patch Tuesday fixes 2 Zero-Day vulnerabilities, with one being designated as actively exploited* (CVE-2022-37969*, CVE-2022-23960) is said to be of Privilege Escalation and Cache Speculation Restriction, respectively. Along with this, Microsoft has speedily quashed 16 Microsoft Edge (Chromium Based)Vulnerabilities, of which one has been addressed as a Remote Code Execution (RCE) (CVE-2022-38012). Therefore the same was updated from September 1st to 3rd, 2022
Zero-Days Vulnerabilities:
CVE-2022-37969 | Windows Common Log File System Driver Elevation Of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8. An attacker should have access and the ability to run code on the target system. Common social engineering delivery methods can be used to initiate attacks for bugs of this nature, such as sending specially crafted documents and convincing users to click on the document or link. Hence, an attacker who can successfully exploit this could gain SYSTEM privileges. Therefore, this vulnerability is being actively exploited as per the Exploit-ability Assessment by Microsoft. A good patch management software can prevent these attacks.
CVE-2022-23960 | Cache Speculation Restriction Vulnerability
This vulnerability has a CVSSv3.1 score of 5.6.CVE-2022-23960 is regarding a vulnerability known as Specter-BHB. An attacker can in fact trick users into downloading and opening a specially crafted presentation file. Hence, this CVE affects Windows 11 (ARM64-based system).
In addition Please see Spectre-BHB on arm Developer for more information.
Critical Vulnerabilities (Resolved by Microsoft’s September Patch Tuesday)
In this September 2022 Patch Tuesday, Microsoft has furthermore addressed five critical vulnerabilities.
CVE-2022-37956, CVE-2022-37957, and CVE-2022-37964 | Windows Kernel Elevation Privilege Vulnerability
CVE-2022-37956, CVE-2022-37957, and CVE-2022-37964 are clubbed under the Elevation of Privilege, which is supposed to affect the Windows Kernel. All three vulnerabilities have received a CVSSv3 score of 7.8. Microsoft advisory says a successful attack against this component will reward an attacker for gaining SYSTEM privileges.
As per the Exploit-ability by Microsoft, only CVE-2022-37957 has been designated as “Excitability More Likely.”
CVE-2022-34721 and CVE-2022-34722 | Windows Internet Key Exchange (IKE) Remote Execution Vulnerability.
CVE-2022-34721 and CVE-2022-34722 together are RCE vulnerabilities in the Windows IKE Protocol. Both have been given a CVSSv3 score of 9.8, and the Exploitability Assessment by Microsoft is “Less Likely.” An unauthenticated attacker could send a specially crafted IP packet to a target machine running Windows and IPSec enabled, hence enabling remote code execution exploitation. All Windows Servers are affected because they accept both V1 and V2 packets.
CVE-2022-37958 | Updated: New Flaw Discovered (Resolved by Patch Tuesday).
As of December 21, 2022, CVE-2022-37958 severity has elevated from important to critical.
A new flaw has been discovered, which works like Eternal Blue and hence could be exploited remotely without any authentication required. Reportedly the bug is “wormable,” which means it can self-replicate and laterally move to hit other vulnerable systems in the network and hence might arise a new problem.
The flaw in CVE-2022-37958 is not limited to the SPNEGO Mechanism, which resides in the Server Message Block (SMB) protocol. It can also affect RDP, SMTP, and HTTP.
Microsoft fixed the previously existing bug in September 2022 with its Patch Tuesday rollout, which also fixes this new flaw.
Microsoft Security Bulletin Summary for September 2022
- .NET and Visual Studio
- .NET Framework
- Azure
- Azure Arc
- Cache Speculation
- HTTP.sys
- Microsoft Dynamics
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Windows ALPC
- Microsoft Windows Codecs Library
- Network Device Enrollment Service (NDES)
- Role: DNS Server
- Role: Windows Fax Service
- SPNEGO Extended Negotiation
- Visual Studio Code
- Windows Common Log File System Driver
- Windows Credential Roaming Service
- Windows Defender
- Windows Distributed File System (DFS)
- Windows DPAPI (Data Protection Application Programming Interface)
- Windows Enterprise App Management
- Windows Event Tracing
- Windows Group Policy
- Windows IKE Extension
- Windows Kerberos
- Windows Kernel
- Windows LDAP – Lightweight Directory Access Protocol
- Windows ODBC Driver
- Windows OLE
- Windows Photo Import API
- Windows Print Spooler Components
- Windows Remote Access Connection Manager
- Windows Remote Procedure Call
- Windows TCP/IP
- Windows Transport Security Layer (TLS)
Product: Microsoft Windows
CVEs/Advisory: CVE-2022-23960, CVE-2022-26928, CVE-2022-30170, CVE-2022-30196, CVE-2022-30200, CVE-2022-33647, CVE-2022-33679, CVE-2022-34718, CVE-2022-34719, CVE-2022-34720, CVE-2022-34721, CVE-2022-34722, CVE-2022-34723, CVE-2022-34724, CVE-2022-34725, CVE-2022-34726, CVE-2022-34727, CVE-2022-34728, CVE-2022-34729, CVE-2022-34730, CVE-2022-34731, CVE-2022-34732, CVE-2022-34733, CVE-2022-34734, CVE-2022-35803, CVE-2022-35830, CVE-2022-35831, CVE-2022-35832, CVE-2022-35833, CVE-2022-35834, CVE-2022-35835, CVE-2022-35836, CVE-2022-35837, CVE-2022-35838, CVE-2022-35840, CVE-2022-35841, CVE-2022-37954, CVE-2022-37955, CVE-2022-37956, CVE-2022-37957, CVE-2022-37958, CVE-2022-37959, CVE-2022-37969, CVE-2022-38004, CVE-2022-38005, CVE-2022-38006
Impact: Elevation of Privilege Security Feature Bypass Information Disclosure Remote Code Execution Denial of Service
KB’s: 5017367 5017305 5017370 5017377 5017365 5017327 5017315 5017308 5017316 5017328 5017392
Product: Microsoft Office
CVE/Advisory: CVE-2022-38010 CVE-2022-37962 CVE-2022-37963 CVE-2022-35823 CVE-2022-37961 CVE-2022-38008 CVE-2022-38009
Impact: Remote Code Execution
KB: 5002166 5002178 5002264 5002267 5002159 5002269 5002142 5002258 5002257 5002271 5002017 5002016 5002270
Product: Microsoft Edge (Chromium-based)
CVE/Advisory: CVE-2022-3075 CVE-2022-3058 CVE-2022-3057 CVE-2022-3056 CVE-2022-3055 CVE-2022-3054 CVE-2022-3053 CVE-2022-3047 CVE-2022-3046 CVE-2022-3045 CVE-2022-3044 CVE-2022-3041 CVE-2022-3040 CVE-2022-3039 CVE-2022-3038 CVE-2022-38012
Finally, these were the highlights of Microsoft’s September Patch Tuesday.
SanerNow VM and SanerNow PM detect and automatically fix these vulnerabilities and hence by applying security updates. Use SanerNow and keep your systems updated and secure.