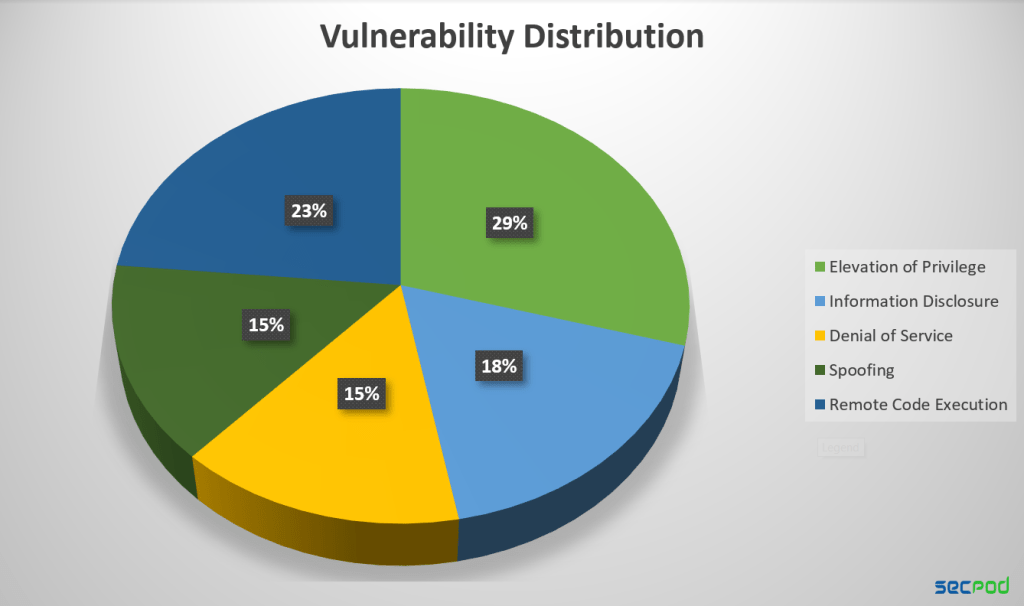
Microsoft addressed 34 security flaws in its December 2023 Patch Tuesday, including one previously known vulnerability in AMD CPUs. While eight of these vulnerabilities were classified as remote code execution (RCE), only three were considered critical by Microsoft. In total, four vulnerabilities were deemed critical: one related to spoofing in Power Platform, and three RCE vulnerabilities – two in Internet Connection Sharing and one in Windows MSHTML Platform.
Zero Day Vulnerabilities solved by Microsoft Patch Tuesday, December 2023
Microsoft’s December 2023 Patch Tuesday includes a fix for a critical zero-day vulnerability in AMD processors that was publicly disclosed in August.
CVE-2023-20588 – AMD, division-by-zero vulnerability: Speculative Leaks are a type of bug known as a “division-by-zero.” This means that there is an error in the code that causes the processor to try to divide a number by zero, which is mathematically impossible. As a result of this error, the processor may leak sensitive data that should not be accessible to attackers.
To address this vulnerability, AMD recommends developers implement smarter practices in their code. This includes ensuring that privileged data is not utilized in division operations prior to changing privileges.
Critical Vulnerabilities solved by Microsoft Patch Tuesday, December 2023
CVE-2023-35628 – Windows MSHTML Platform, Remote Code Execution Vulnerability. This vulnerability allows attackers to exploit email clients with a specially crafted message that triggers remote code execution on the victim’s machine.
User interaction, such as opening the email, reading it, or clicking on a link, is not required for the attack to succeed. This poses a significant threat as users might not even be aware of the attack taking place.
CVE-2023-35641 and CVE-2023-35630 – Internet Connection Sharing (ICS), Remote Code Execution Vulnerability. Exploiting this vulnerability requires the attacker to send a specially crafted DHCP message targeted at a server running the Internet Connection Sharing service.
This vulnerability is limited by its dependence on direct network communication. As such, it cannot target systems located on different network segments.
CVE-2023-36019 – Microsoft Power Platform Connector, Spoofing Vulnerability. This vulnerability can be exploited by sending a malicious file or link to the victim. If the victim opens it, the attacker’s code will run on their computer and potentially compromise the machine.
Products Affected
- Azure Connected Machine Agent
- Azure Machine Learning
- Chipsets
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Office Outlook
- Microsoft Office Word
- Microsoft Power Platform Connector
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows DNS
- Windows Cloud Files Mini Filter Driver
- Windows Defender
- Windows DHCP Server
- Windows DPAPI (Data Protection Application Programming Interface)
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Media
- Windows MSHTML Platform
- Windows ODBC Driver
- Windows Telephony Server
- Windows USB Mass Storage Class Driver
- Windows Win32K
- XAML Diagnostics
SanerNow Vulnerability Management, Risk Prioritization, and Patch Management detect and automatically fix vulnerabilities with risk-based remediation. With SanerNow, you can keep your systems updated and secure.