In today’s Information-rich era, data security is a top concern for organizations. As per the study, cyber-attacks are launched 2,244 times daily, i.e., every 39 seconds. An organization’s vulnerability management security team plays the most vital role in protecting sensitive data against information security risks and also in selecting a vulnerability manager that will best suit the organization’s IT environment. A Vulnerability Management Software can prevent these attacks.
In this article, let’s dive into the new-age post-pandemic responsibilities that vulnerability management demands from the IT Security teams. A good Vulnerability management tool can solve these issues.
Adopt Continuous Vulnerability Management Security tools
An IT team’s role is to address the cybersecurity issue and take the necessary initiatives to use the organization’s IT resources effectively. Therefore, employing a suitable vulnerability manager and technologies will help them reduce attack surfaces with minimum IT resources. Businesses should not employ various services from multiple vendors for each data security module. You should be able to control endpoints using a single platform.
An organization with a complex environment will have devices with different operating systems. It is ineffective to use multiple tools for managing devices with other OS in the longer run. Therefore, you must choose a continuous vulnerability management program that supports operations on all OSs from a single console.
Also Read: How Continuous Automated Vulnerability Management Differs from Traditional Programs
Automate Recurring Cyber Security process
In today’s evolving threat landscape, enterprises should quickly remediate security flaws before attackers exploit them. Several companies are still using a ticketing system to resolve cyber security flaws. Moreover, it is not practical to create a ticket per vulnerability.
Instead, you should automate the existing manual process using an automated vulnerability manager. It would create tickets based on the designed algorithms and fasten the process of remediating the security flaws in the network.
Without automation, you might have to deal with an increasing number of cyber security alerts and possible threats. It would require several hours to resolve, and false positives kill more time. Several such repetitive processes don’t need human interventions always. Therefore, the use of automation frees up a lot of your time dealing with real cyber security threats.
Manage Complex IT Computing Environment from Cloud
The new normal due to the pandemic has resulted in the way businesses operate. It has brought several challenges to the roles of IT admins as you need to manage IT assets from remote locations. Therefore, organizations adopt cloud-based strategies to address cybersecurity issues from anywhere. Your vulnerability management security team should be well versed in managing devices from a remote location and gain the necessary skill on cloud technology platforms instead of just relying on an on-premise network.
When it comes to a complex lT environment, you might require to execute elaborate workflows for deploying patches or any configuration changes. Certain proprietary software assets might introduce a different level of challenges, whether installed remotely or on-premises devices.
Preparing Comprehensive Reports
The task of remediating IT security flaws should be easy and effective. In order to make it happen, your vulnerability management security team should ensure continuous and automated vulnerability manager is embedded in enterprises’ objectives. It is advantageous for your teams to have insightful and ready-to-use reports that enable you to accomplish cybersecurity goals. Therefore, a thorough analysis of tools and technologies is essential to adopt cyber hygiene measures built on the cloud platform.
Responsibilities are only applicable to vulnerability management operations. They differ from their regular duties based on the organization’s size from small to large enterprises.
How SanerNow Helps Vulnerability Management Security Team Prevent CyberAttacks
SecPod’s SanerNow is a CyberHygiene platform that prevents cyberattacks using continuous and automated vulnerability management solutions. Constant visibility of the computing environment helps identify vulnerabilities, misconfiguration, and implement necessary automation techniques. The platform works on the Agent-Sever model. In order to facilitate the IT security admins’ role, the agent installed on all devices receives input from the server and continuously executes the tasks automatically.
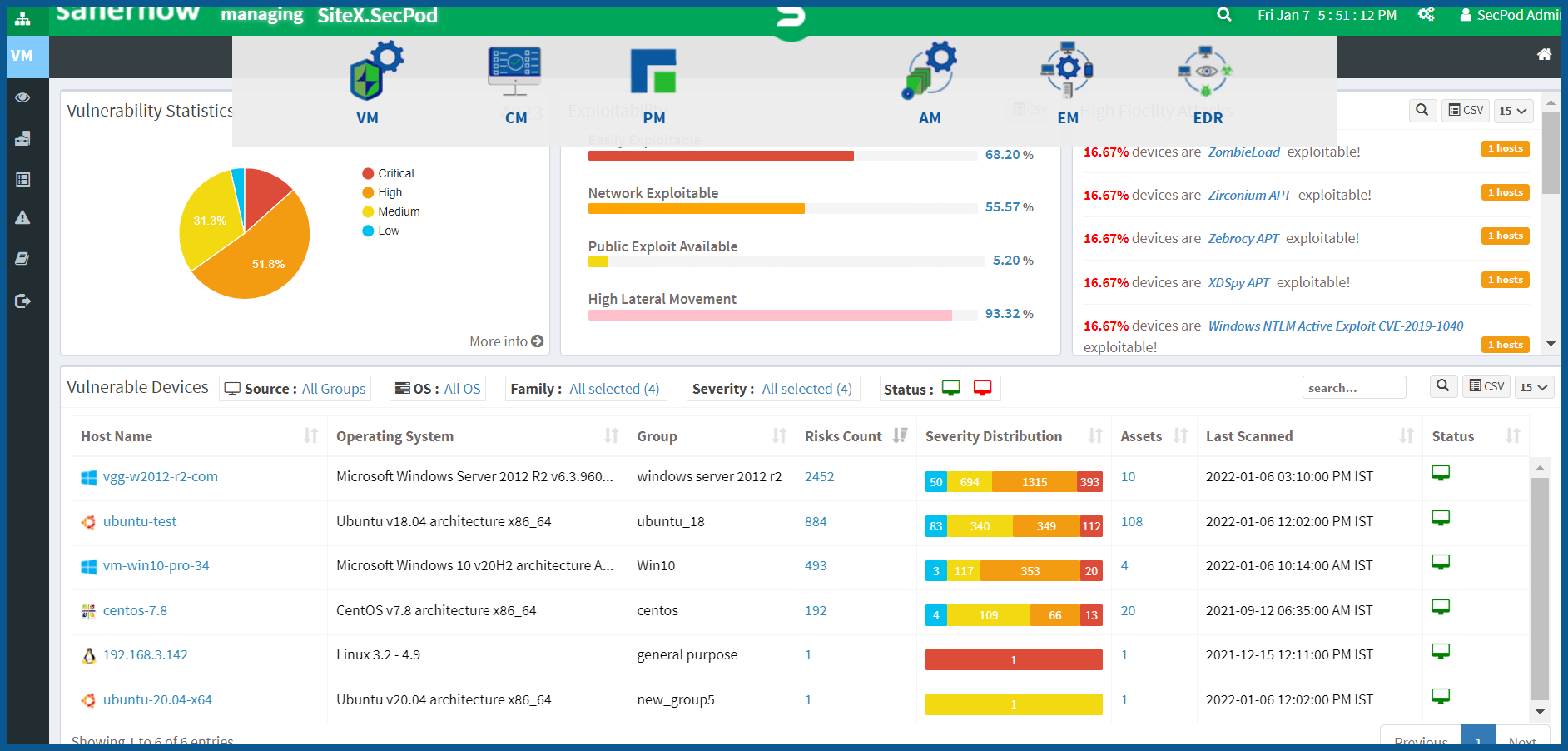
SanerNow agent continuously scans the entire computing network and delivers accurate vulnerability data, which helps in faster remediation. The platform houses 160,000+ security checks, which results in a reduced security gap between discovering and remediating vulnerabilities. The accuracy of the scanned vulnerability data is very high as the large database of large security checks backs it up. It helps IT teams take appropriate remediation measures and prevent cyberattacks.
Schedule a demo of SanerNow and strengthen your vulnerability management process. Prevent cyberattacks using continuous and automated vulnerability management solutions.