A new vulnerability was discovered in the sudo utility which allows an unprivileged user to gain root privileges without authentication. CVE-2019-18634 is classified as Stack-based Buffer Overflow(CWE-121). This vulnerability can be fixed using auto patching.
The sudo exploit affects all Unix-like operating systems and is prevalent only when the ‘pwfeedback’ option is enabled in the sudoers configuration file. pwfeedback provides visual feedback(* for every key press) when a user inputs the password. Continuous and automated patch management software can protect systems from such exploits.
An attacker can exploit this bug by triggering a stack-based buffer overflow. When sudo prompts for a password, it can receive a large input via a pipe, which has the potential to overflow the buffer and cause a Segmentation Fault. Additionally, a user can craft the input in a manner that allows them to obtain root privileges.
It’s essential to have a vulnerability management tool to prevent such attacks.
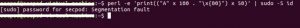
For example,
$ perl -e 'print(("A" x 100 . "\x{00}") x 50)' | sudo -S id
The advisory points out that there are two flaws which contribute to the vulnerability:
- When reading from somewhere other than the terminal, the system does not ignore the pwfeedback option. The line erase character remains at its initialized value of 0 due to the absence of the terminal.
- The code responsible for erasing the line of asterisks resets the buffer length but fails to reset the buffer position if there is a write error. This allows getln() function to write past the end of the buffer causing a buffer overflow.
When attempting to write to the read end of a unidirectional pipe, the system reports a write error. This write error causes a line to be erased, but the system fails to properly reset the remaining buffer length, thereby creating a vulnerability that can be exploited to cause a stack-based buffer overflow.
How to check if you are vulnerable by sudo exploit?
Users can enable pwfeedback by running the following command::
sudo -l
Listing pwfeedback in the “Matching Defaults entries” output affects the sudoers configuration.
Example output:
$ sudo -l Matching Defaults entries for millert on linux-build: insults, pwfeedback, mail_badpass, mailerpath=/usr/sbin/sendmail User millert may run the following commands on linux-build: (ALL : ALL) ALL
Affected Product
Sudo versions 1.7.1 to 1.8.25p1
Impact
An unprivileged user can escalate to the root account by overflowing the buffer.
Solution
The vendor has released an update to mitigate the vulnerability.