According to F5, a critical security vulnerability in BIG-IP is being actively exploited after its public disclosure. CVE-2023-46747, resulting in remote code execution, is being further used to exploit CVE-2023-46748, an SQL injection vulnerability.
Both flaws have high CVSS scores of 9.8 and 8.8, respectively. F5 advises updating the software to the latest patch, which you can do with a Patch Management tool.
How does the exploit chain work?
Put simply, CVE-2023-46747 allows an unauthenticated attacker to bypass Configuration utility authentication. CVE-2023-46748, on the other hand, allows an authenticated attacker with access to the Configuration utility to perform an SQL injection.
With that information, you can probably piece the exploit chain together! The first vulnerability is used to access the Configuration utility, where the second vulnerability (SQL injection) can be exploited.
Technical Details
This blog focuses on CVE-2023-46747, the initial vulnerability in the exploit chain. Project Discovery released the proof of concept for it, which will be explained in this section.
The exploit was found after examining BIG-IP’s httpd software to find an HTTP request smuggling flaw, similar to another vulnerability known as CVE-2022-26377. This flaw allowed attackers to carry out AJP (Apache Jserv Protocol) request smuggling.
To exploit this flaw, a message with a mandatory POST body length of 0x204 was submitted. The AJP listener would interpret it as an AJP post request and send it wherever the attacker wanted. This confusion in message interpretation resulted in request smuggling, and the knowledge of this vulnerability was used to find CVE-2023-46747 in a BIG-IP appliance.
After searching ‘/usr/share/tomcat/conf/server.xml’, the appliance examined was confirmed to be using AJP to route requests to the backend. This was done through /tmui (Traffic Management User Interface) endpoints, which forwarded requests to the AJP service.
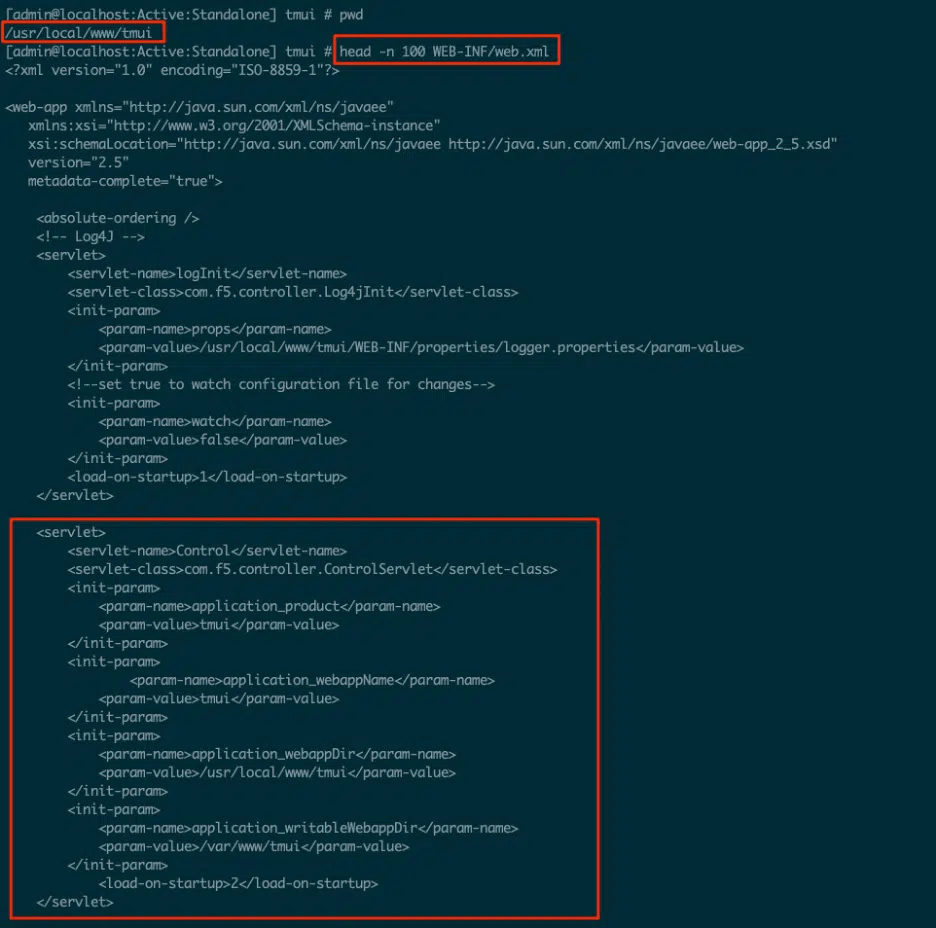
As seen in this image, the ‘/usr/local/www/tmui’ directory contained relevant Java code and handlers. This meant AJP smuggling could be inconsistently triggered by targeting any ‘/tmui/’ url.
Since the possibility of AJP exploitation was confirmed, the backend Java servlets connected to AJP were examined. Request information was given to a servlet through an HTTPServletRequest object, and response information was written into an HTTPServletResponse object. The HTTPServletRequest object contained information from AJP packets, including user information such as username and privilege level.
In conclusion, it was found that a smuggled AJP packet with arbitrary content could create administrator credentials and run arbitrary commands through the ‘mgmt’ API. Once it was discovered that this was doable without authentication, it was clear that the flaw could compromise the appliance.
Affected Products
The following BIG-IP modules are vulnerable:
- BIG-IP 17.1.0
- BIG-IP 16.1.0 – 16.1.4
- BIG-IP 15.1.0 – 15.1.10
- BIG-IP 14.1.0 – 14.1.5
- BIG-IP 13.1.0 – 13.1.5
Solutions and Mitigations
F5 released an advisory regarding this flaw, containing a hotfix and steps for users to follow. We recommend going through it and carrying out all the remediation processes detailed by F5.
Recommended mitigations include installing a pre-written script for versions after 14.1.0 and blocking the Configuration utility through either self-IP addresses or the management interface.
You should check whether your version of BIG-IP is vulnerable, and install the fix immediately if it is! SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Use SanerNow and keep your systems updated and secure!
Have any questions on how to fix CVE-2017-8529 specific to your IT? Let’s discuss.

