Cyber-attacks are becoming extensively aggressive with every passing day, week, month, and year. To add fuel to the gasoline, cyberattacks in the past couple of years have become the fastest-growing criminal activity globally. The world isn’t the same anymore. We are most accustomed to accessing everything by simply fiddling with our fingers. Since the pandemic, the world is more connected more accessible due to a bubble burst in digitization.
The boons that came with the inter-connectedness made it easier for people across different verticals to thrive. But the flipside to global digitization is the emergence of unprecedented cyberattacks. The cyberattacks of the past and the ones that are yet to happen can be called ‘sophisticated.’
Hackers, phishers, extortionists, and scammers are swarming like vultures for a single loophole. One loophole in any IT ecosystem is all these criminals need to blow the infrastructure to kingdom come. The recent devastating blow of 2021 came with the infamous Log4j vulnerability. Further, pointing out why protection and remediation should be paramount in 2022.
After careful and thorough research on the past cyberattacks, we think these cyberattack trends will continue to dominate the cybersphere in 2022.
Remediation Should Happen At Fundamental Levels
The core component of protecting, fixing, or remediating relies on validating the networking systems. All connected links in an IT infrastructure have to go through the to-and-fro motion to validate both preceding and succeeding networks and devices intertwined with each other. There are numerous Vulnerability Management software in the market, but they’re not adequate if you or your team doesn’t have a goal.
Security teams need to curate a holistic approach and prioritize remediating. For instance, if you understand how vulnerabilities penetrate into networks and devices, you can bring in action to keep attacks from happening. Having multiple layers of protection could benefit security teams in the long run.
Remote Workforce, The New Normal In 2022 Will Incur Massive Cyber Attacks
In the past couple of years, cybercriminals did manage to bring a wave of attacks globally. These attacks didn’t just showcase the perfect coordination but also were powerful enough to get organizations to their knees. The remote workforce also played a crucial role in escalating the magnitude of cyberattacks. The inescapable fact is remote working module is here to stay even if organizations are more exposed to bad actors. At-home networks and working from personal devices are the fundamental reason why attacks will continue to happen in 2022.
So, what really drives cyber attacks on the remote workforce?
1. Low visibility on home networks
2. Not an advanced vulnerability management in place
3. Periodic vulnerability scanning
4. Missing out on patching vulnerabilities upon getting the notification
As mentioned earlier, a Remote or Hybrid Workforce isn’t going anywhere. As the pandemic is said to become a permanent part of everyone’s lives, the need for adopting new measures and strategies to protect devices has become quintessential now. Since the inception of the internet and the times that we’re living in where the internet is indispensable, managing risks has never been this important.
Cyberattacks do more than just jeopardize networks and devices intertwined in an organization. It has a direct impact on productivity. Today it’s not only up to security admins to understand the essence of protecting devices. Employees should be educated regarding cybersecurity norms, irrespective of their professional background. With the advancement in vulnerability management, everyone has the avenue to seize the opportunity to protect devices and networks. Employees often are unaware that they are leaving the back door to bad actors.
It’s a brave new world that we’re living in; the world’s more innovative than ever, connected than ever. Driving awareness regarding cyber security and cyber attacks is the least that everyone sitting at the comfort of their homes and working while spending those little moments with loved ones can do.
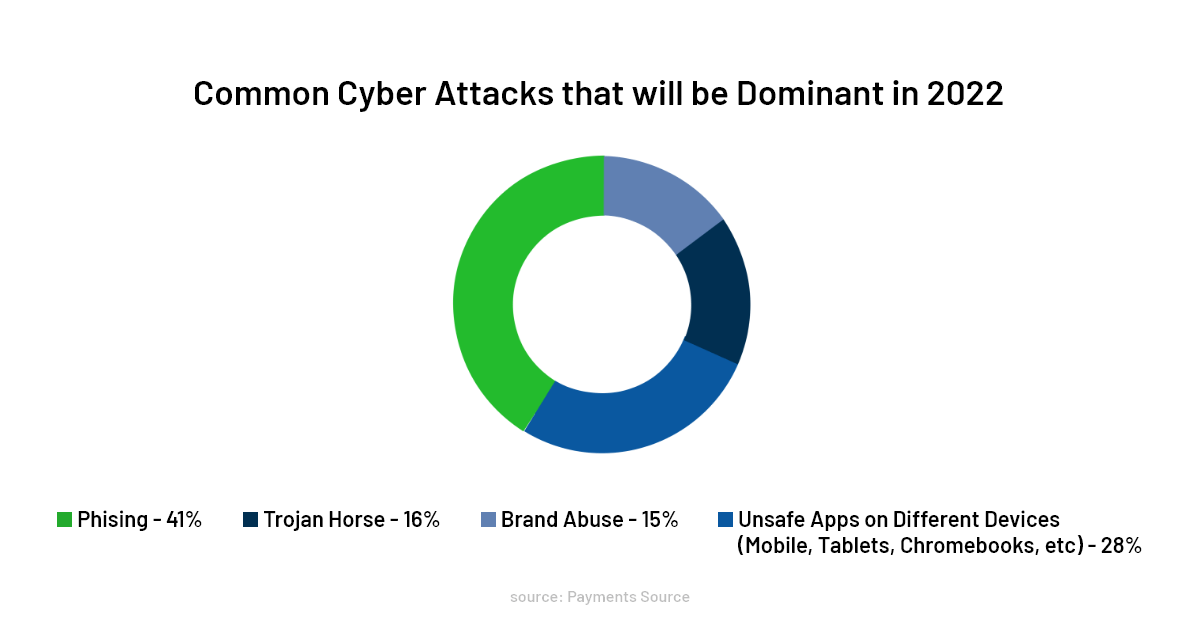
Common Cyberattacks That Will Continue To Dominate In 2022
Before we get into the types of cyberattacks that will dominate in 2022, let’s take a little detour into the history of cyberattacks. The following revelation isn’t make-believe, but the first-ever cyberattack was nothing but a game. Back in 1971, a computer program was curated by Bob Thomas to traverse between computers connected. Thomas’ program wasn’t harmful; instead, the message that the program displayed was, “I’m the creeper: catch me if you can.” This might take you back to the 90’s film Hackers, which showed the familiar people how things could become in the foreseeable future. Well, we are living in that future now with the internet becoming more widespread now!
The first malware program was AIDS Trojan which Joseph Popp brought back in 1989. All the program did was scramble the names of files due to a flaw in its design. But today, a simple virus can disrupt an entire network in an organization. Let’s get into the kind of cyberattacks that would put organizations in peril without further ado.
1. Advanced Ransomware And Massive Use Of RaaS
Ransomware attacks reached their peak in 2021; that wasn’t the endgame. It showed organizations how despicable the attackers are becoming with these cyberattacks. Ransomware attacks are going to increase in months to come. Attackers are working relentlessly and looking for that one loophole to get into the network.
As more and more devices are connected to the internet, the chances of exploitation in the wild increase. Checking for patching and security updates should be a regular practice. Ransomware is the black hole of cyberspace, and with RaaS becoming the ideal practice among attackers, attacks are becoming more widespread.
The birth of RaaS empowered attackers with zero-to-minimal technical skills, knowledge, and ideas to launch cyberattacks rendering the victims decapitated. If you’re laid back in safeguarding your ecosystem, how can you put an end to these affiliated attacks? 2021 was the worst year for cyberspace, and it will get worse as the day passes by.
Attackers are relying on Ransomware as it brings multiple forms of extortion. As the attacks increase in range and intensity, victims face tough times by paying the ransom. Ransomware will worsen security admins and businesses as it is in continuous innovation. Before things get better, they always tend to get worse; that’s how the world has worked since time immemorial. Security admins should be vigilant as the first line of defense, and each alert should be investigated upon detection.
2. Malware
Malware is the most go-to attack that is widely used globally. It enters a device and steals, deletes, and encrypts data. It takes control of a computer’s core functionalities and monitors users’ activity. Malware can be found in different forms such as Trojan, viruses, spyware, and worms.
Malware often slows down the productivity of an organization. Hackers use malware to steal sensitive information, and passwords lock people out of their workstations. In the worst-case scenario, it can create a scenario where a massive chunk of funds will be required to fix things.
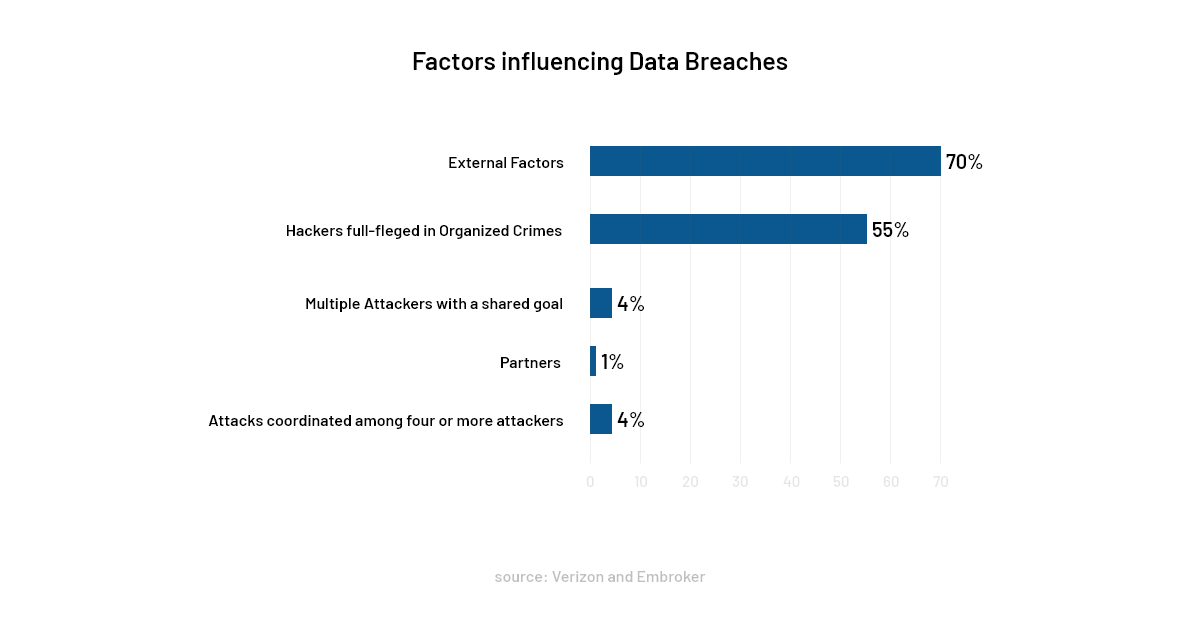
3. More Widespread Data Breaches
Attackers are likely to demand more in ransom after breaching data this year. There is a highly possible chance that data breaches will be more large-scale by targeting organizations’ businesses partners and customers. The ransom that they will procure from these parties will ultimately allow them to make big bucks.
In the past six months, MSPs, the public sector, and finance industries were significantly hit by attackers. The trend will get more potent in time to come!
4. Supply Chain Will Become A Focal Point For Attackers
This type of cyberattack is the new fun-toy for attackers. In the past year, we saw several attacks on supply chain management due to poor management of systems and software not being up-to-date. Attackers use the vulnerability to infiltrate the digital ecosystem via outside providers and partners that can access both data and systems. Since the epitome of connectedness due to the availability of technology, both service providers and suppliers have access to sensitive data more than ever.
Any software and hardware vendor worldwide are subjected to supply chain attacks. It’s essential to have the best possible end-to-end vulnerability management to safeguard your IT infrastructure and capital.
5. Evolution Of Cyberattacks On Operational Technology
If you carefully look at the evolution of attacks on Operation Technology in the past decade, you’ll find that the threat factor has increased significantly. This year, the amalgamation between Operational Technology and Industrial Control System needs to be vigilant. As attackers are heading towards disrupting this sector, it will not only disrupt productivity; instead, cost humans their lives alongside damage to physical infrastructures.
It is a tremendous challenge for the said industry to step up and face the music, but it isn’t pleasant or soothing this time! Some of the critical challenges that OT face today are:
- Lack of visibility in device inventory makes it impossible for organizations to protect their assets. Accompanied by a complete lack of control makes it hard to deploy patches or run security audits.
- Even in 2022, OT relies on the conventional means of using technology. The physical access is heavily restricted, the components aren’t up to the industry standard, and there is a huge communication gap.
- They also rely on aging or almost obsolete hardware or software, which are easy to breach today. Most of these devices aren’t compatible with modern-day digital defenses.
Tug Of War Between The Good Guys And The Bad
Today cybercriminals do not need a massive team to function. They are the opposite side of the same coin; they, too, have resources and technology at their disposal. The modern-day cybercriminals are nothing but relentless; they are nimble and aren’t scared of getting caught. All they need to do is compel victims to lead them into a network.
The other side of the coin features the security admins who are resourceful. If security admins engage in AI and automation to learn the patterns of attacks, they can bring the next-gen security solutions into existence. A vulnerability management program with AI capabilities could help them generate reports regarding vulnerabilities in real-time. In addition to AI, automation makes monitoring, discovery, accessing, prioritizing, and remediating an absolute breeze. The vulnerability database is better; the better the accuracy in remediating the security admins have. In response to escalating cyber threats, pursuing a cyber security internship offers a foundational step for individuals to actively engage in combatting these sophisticated attacks and safeguarding digital infrastructures.
Many vulnerability management tools in the market only provide solutions after an attack. Simply monitoring isn’t enough today. Instead, changing the game by preventing cyberattacks at all costs would yield different and better results.
Inducing Anxiety And Paranoia Among Security Admins
The conundrum that exists in the realm of cybersecurity is inducing anxiety and insecurity among business leaders, CEOs, and security admins. Since the pandemic, cyberattacks have tripled. We are witnessing attacks on supply chains, cloud platforms, networks, devices, among others, in the most sophisticated manner. The time for learning lessons and sulking is done, now is the time for action.
Prevent Cyberattacks With SanerNow
Going toe to toe against cyberattacks is nothing less than preparing for war. Cyberattacks have become a present and visible danger as attackers are getting into places beyond our wildest dreams. Digital infrastructures in financial systems, IT, healthcare, to supply chains that rely on cyberattacks have touched several corners of operations. Simply put, the world has moved pretty fast from the bone-chilling Cold War to the unprecedented Code War. Today, even technology can’t keep up with the sophisticated attacks orchestrated by attackers; you always need something up your sleeve to keep your digital infrastructure protected.
SecPod SanerNow CyberHygiene platform is a truly unified platform that strengthens your digital ecosystem with robust automation. Its comprehensive vulnerability management solution prevents attacks by providing 360-degree visibility over devices. Built upon the world’s largest vulnerability database with over 160,000 security checks makes it a formidable choice to identify vulnerabilities, assess them, and mitigate loopholes by eliminating them.
With SanerNow Vulnerability Management, you can:
- Scan vulnerabilities under 5 minutes
- Eliminate any unprecedented risks with complete visibility over your digital ecosystem
- Prioritize remediation based on the severity
- Generate audit-ready reports in no time, to name a few
Schedule a quick demo make use of next-level automation, discovery, assessment, remediation, and enhance your cyber hygiene practice.