CVE-2016-0728 is the latest zero-day flaw in the Linux kernel which affects millions of users across the world. The Linux Kernel vulnerability is there for several years and discovered only recently. This flaw exists in all the Linux kernel versions 3.8 and later. CVE-2016-0728 is basically a memory-leak vulnerability, where the flaw exists within the Linux’s security features-keyrings facility. A reference leak in the keyrings facility causes CVE-2016-0728. An attacker can exploit the vulnerability by running a malicious Linux application on the affected device. If successfully exploited, the vulnerability can allow attackers to get root access to the operating system, enabling them to do anything that a root user is allowed to do. Hence, it is essential to have a vulnerability management software.
linux kernel vulnerability exists actually due to an error in the “join_session_keyring” function within process_keys.c script of kernel code. However, below is a buggy code snippet taken from process_keys.c script for vulnerable Linux Kernel 3.18.x (3.18.25) found here. A patch management tool remediates this vulnerability.
Upon analyzing above code it is clear if a thread tries to set its current session keyring with the same one already set, the control passes over to error2 label. But there is no way that the reference for the keyring discarded in this case and resulting in reference leak error. However, below code explains the scenario.
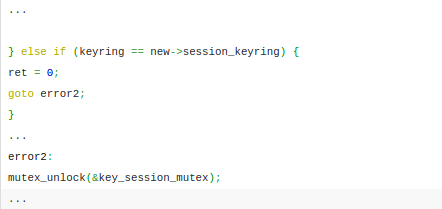
The above mentioned execution does not have a call to key_put() function so as to discard the reference for the keyring resulting in memory leak. Moreover, this memory leak error can carefully craft to create a fully-working exploit escalating users priveleges. The sequence of steps which exploit would need to do include:
1) Get hold of reference to key object.
2) Somehow overflow internal RefCount in usage field.
3) Free keyring object and hold a reference to it.
4) Allocating and controlling the kernel object that will override the freed keyring object.
5) Using the reference to the old key object and trigger code execution.
A fully Working exploit is here which successfully escalates privileges from a local user to root.
Check for Vulnerable Kernel:
The memory leak vulnerability in CVE-2016-0728 occurs when a thread replaces its current session keyring with the keyring that has been set as its session keyring. A simple program to test for this vulnerability is here.
The program simply tries to set 100 times the same keyring name that already exists to trigger the memory leak. If the program successfully creates references for the same keyring name, the running kernel is vulnerable.
Steps to Check include:
1) Compile provided test C-Code.
2) Check the keys before running the test script, by checking the contents of file /proc/keys that list all the currently viewable keys.
3) Run the created test-executable.
4) Check the contents of /proc/keys once again.
5) If 100 references for leaked-keyring are present, like the one shown below, Kernel is vulnerable.
Download SecPod Saner now and keep your systems updated and secure.
