The impact of the pandemic has brought a multitude of security challenges for the IT security team and chief information security officers. One of the main challenges includes remediation of security flaws in a complex IT network and patch vulnerabilities using a patch management tool whenever necessary.
Generally, an IT security team is presented with significantly responsible tasks if security vulnerabilities reach a record high. As a result, your team should be well-equipped with the necessary vulnerability management tool and resources to meet the growing demands of remediating high-risk vulnerabilities. It prevents business enterprises from being attacked.
Your team should adopt a continuous and automated vulnerability management approach to alleviate the strain and enhance the remediation speed. It reduces the overall risk posture to a greater extent and facilitates business growth. To have a clear view, here are some practical solutions to leverage continuous and automated vulnerability remediation programs while dealing with critical cyber security flaws.
Define Risk and Vulnerability
Enterprises should grasp the significant differences between risk and vulnerabilities. The risk is a calculated assessment of possible security threats to a computing environment. In comparison, vulnerabilities are flaws or security weaknesses that may or may not exploit.
If organizations have fewer resources to deal with too many vulnerabilities, they must look beyond CVEs and monetize their remediation priorities as per the severity level. It helps to protect assets that matter the most.
While defining risk, it is crucial to focus on Zero-Day vulnerabilities, which offer an unprotected gateway through which a hacker can cause security threats. They can be misconfigurations or security flaws in software, firmware, or hardware that you and your organization aren’t aware of. It is known to software vendors or security experts only after a successful zero-day attack.
CVSS Score Isn’t the Complete Picture
While remediating a vulnerability, organizations consider CVSS scores to decide their severity. The technique isn’t the complete solution, as modern hackers have figured out various ways to outdo them. Several latest research has proven that the high CVSS score doesn’t necessarily mean the vulnerability exploits. Instead, you should focus on the possibility of security threats using threat intelligence and employ continuous and automated vulnerability management software.
Vulnerabilities Beyond CVEs
CVE is termed Common Vulnerabilities and Exposure, used to identify and track the vulnerabilities. However, not all vulnerabilities have a CVE number. You should never settle to just remediate security flaws with CVE data because hackers are on the lookout for more sophisticated ways to cause cyber threats. An increase in the vulnerabilities unassigned with CVE numbers will also create new doorways for hackers to attack the computing environment. In order to combat these challenges, a continuous and automated vulnerability management tool is necessary. It provides a data-driven approach to discover, assess, and act against all sorts of vulnerabilities.
Stay Ahead of the Cyber-criminals
Continuous scanning and assessment tackle your biggest challenges of taking cyberhygiene measures that don’t expose the computing environment to more risks. In reality, it is quite a difficult task to achieve without the aid of a continuous and automated remediation program. It offers you the necessary data to make an informed decision and remediate vulnerabilities faster than a hacker can discover and exploit them. Such automated programs are beneficial in cybersecurity battles and likely to eliminate the possibility of cyber-attacks.
Continuous and Automated Vulnerability Management
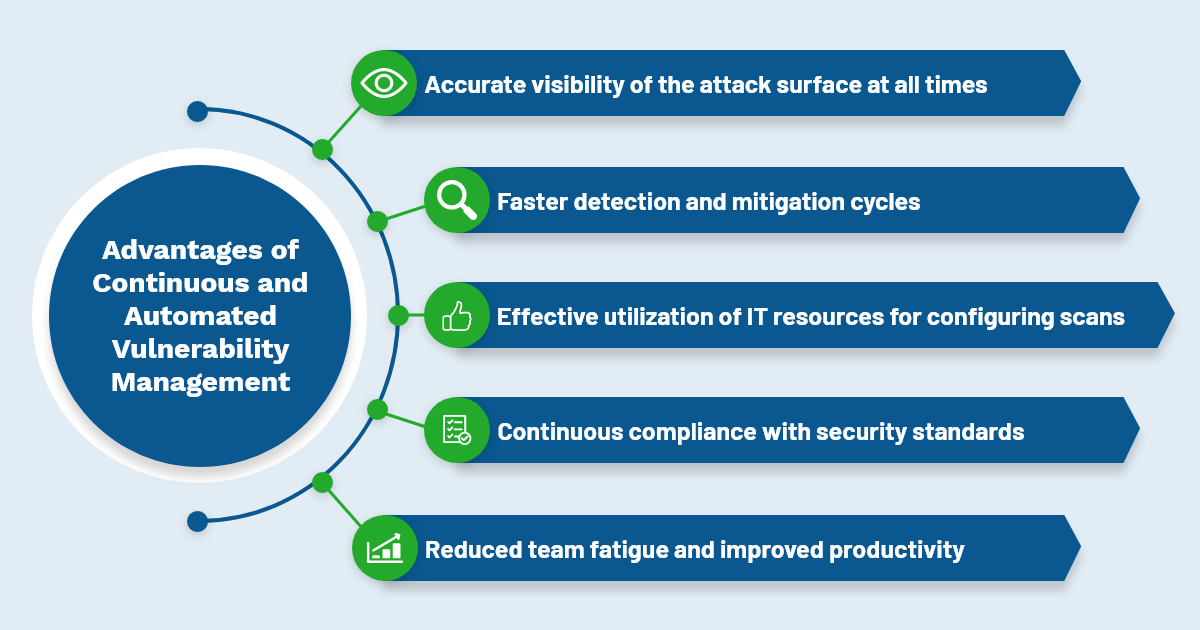
It is best to ensure that your approach is always data-driven in a complex computing network. You must accurately map the identified vulnerability to the appropriate remediation action, which is quite time-consuming. After addressing the security flaws, a final vulnerability scan needs to ensure that it is fixed. These processes consume enormous IT resources, so continuous automated vulnerability management solutions fasten the process with a timely remediation approach. It offers the following benefits:
- Accurate visibility of the attack surface at all times
- Faster detection and mitigation cycles
- Effective utilization of IT resources for configuring scans
- Continuous compliance with security standards
- Reduced team fatigue and improved productivity
Predict and Protect
An automated vulnerability management solution empowers enterprises with valuable and actionable insights to prioritize security flaws. An organization that is relying on predictive technology should make use of a continuous vulnerability management program. It provides early warning signs using sufficient data on security flaws. Therefore, you can achieve the objective of securing the IT network with minimum risk with a patch management software. You can also obtain the necessary foresight to predict which vulnerabilities the hackers intend to exploit. As a result, the remediation efforts of your entire team become proactive rather than reactive.
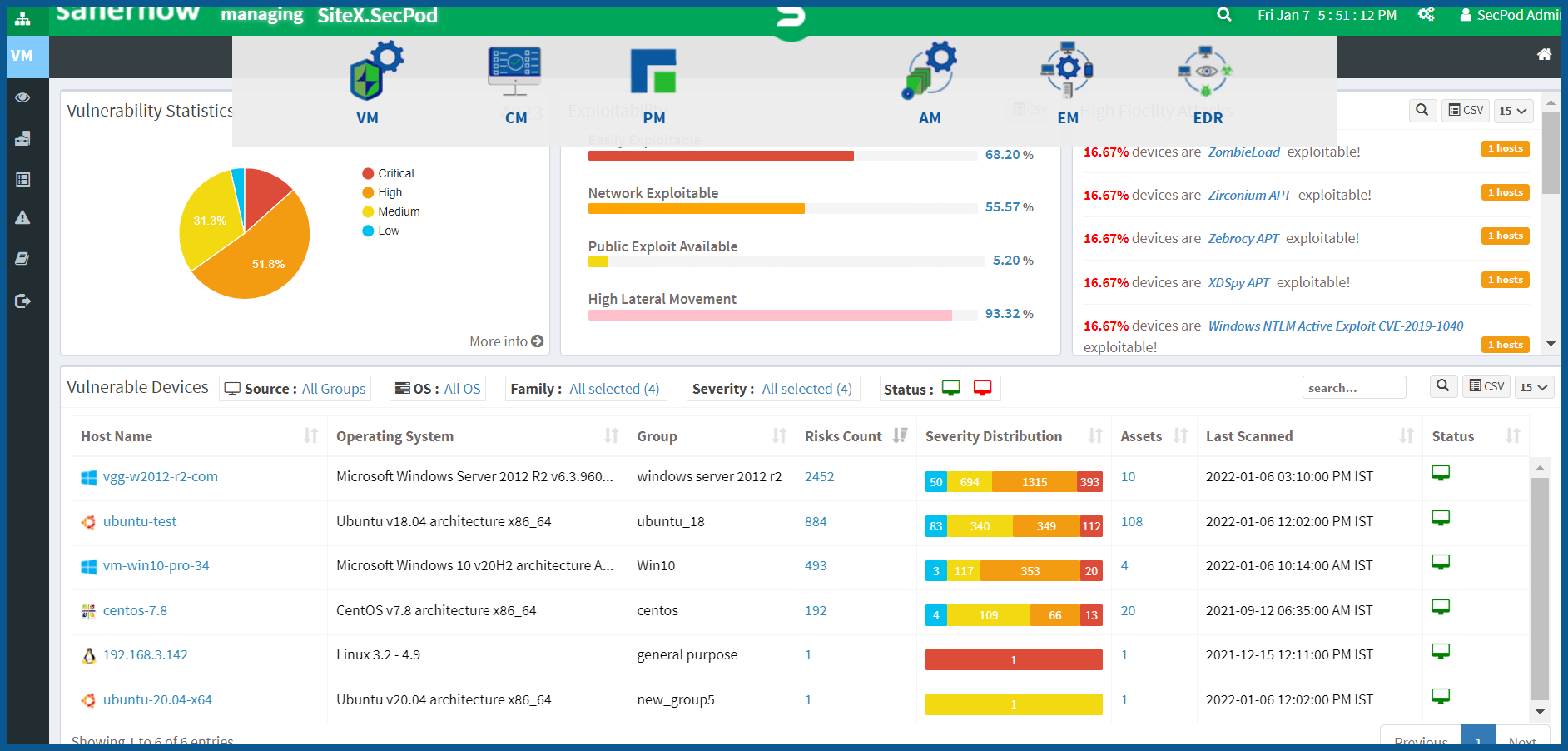
SanerNow’s Way of Remediating Vulnerabilities
SanerNow is a Cyberhygiene platform that provides continuous and automated vulnerability management solutions. You can gain complete and constant visibility of the complex computing environment, identify vulnerabilities and remediate them instantly, which helps your team eliminate attack-surface. It helps find security flaws in real-time with a data-driven approach resulting in 360-degree visibility over security exposure. SanerNow’s cyber hygiene platform ensures that cyber attackers have difficulty penetrating a computing network.
Schedule a demo of SanerNow and remediate vulnerabilities before getting exploited. Build a strong defense for your computing environment using continuous and automated vulnerability management solutions.