The second week of the new year has arrived, and with it comes 2024’s first Microsoft Patch Tuesday. This time around, Microsoft has fixed 53 vulnerabilities, including 2 critical ones (CVE-2024-20674 and CVE-2024-20700). Perhaps as a new year’s gift to patch writers, there have been no zero days reported (that we know of), and none of the vulnerabilities are being actively exploited.
Of the types of vulnerabilities fixed, Remote Code Execution takes the prize for most common once more, with 12 flaws to its name. Information Disclosure and Elevation of Privilege follow closely behind, with 11 and 10 flaws each. The full distribution can be seen below.
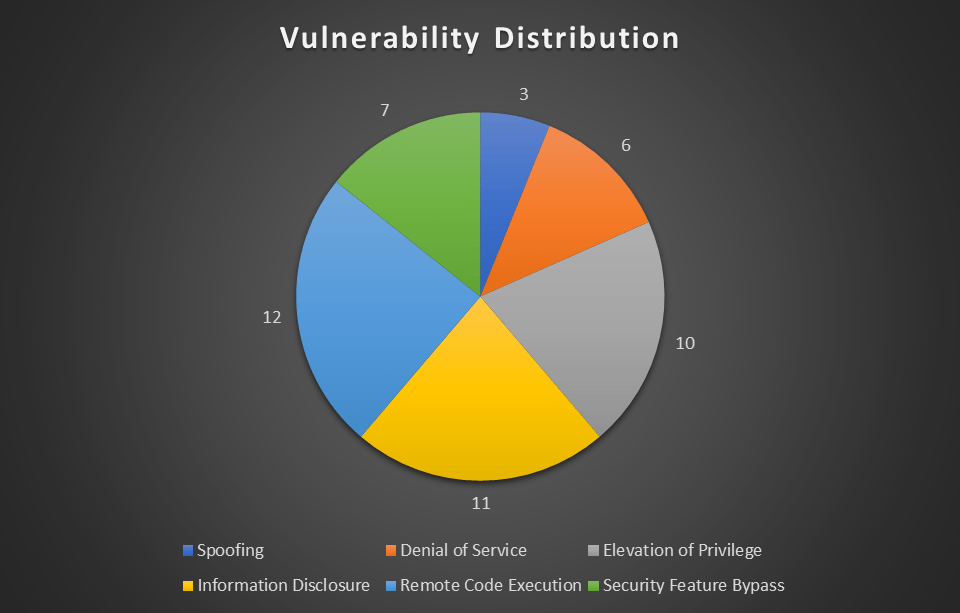
The 4 flaws not included in this visual are Microsoft Edge vulnerabilities (CVE-2024-0222, CVE-2024-0223, CVE-2024-0224, CVE-2024-0225), three of which belong to the Use After Free category, and one of which belongs to the Heap Buffer Overflow category.
Critical Vulnerabilities
- CVE-2024-20674: Windows Kerberos, Security Feature Bypass Vulnerability: Kerberos, the default authentication protocol for Windows, ensures secure user and computer authentication on a network. It forms the foundation for single sign-on and access control.
An unauthenticated attacker with access to the network could leverage a machine-in-the-middle (MITM) or local network spoofing technique. Subsequently, the attacker sends a malicious Kerberos message to the victim machine, impersonating the Kerberos authentication server.
- CVE-2024-20700: Windows Hyper-V, Remote Code Execution Vulnerability: Windows Hyper-V supports hardware virtualization, helping developers test software across operating systems. It allows the streamlined creation of virtual hard drives, switches, and other devices that can be added to virtual machines.
Successful exploitation of this vulnerability requires an attacker with access to the restricted network to win a race condition.
Products Affected
Some of the major products affected are as follows:
- .NET Core & Visual Studio
- Azure Storage Mover
- Microsoft Bluetooth Driver
- Microsoft Devices
- Microsoft Edge (Chromium-based)
- Microsoft Identity Services
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Virtual Hard Drive
- Remote Desktop Client
- SQLite
- Unified Extensible Firmware Interface
- Visual Studio
- Windows AllJoyn API
- Windows Authentication Methods
- Windows BitLocker
- Windows Cloud Files Mini Filter Driver
- Windows Collaborative Translation Framework
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows Group Policy
- Windows Kernel-Mode Drivers
- Windows Libarchive
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Message Queuing
- Windows Nearby Sharing
- Windows ODBC Driver
- Windows Online Certificate Status Protocol (OCSP) SnapIn
- Windows Server Key Distribution Service
- Windows Subsystem for Linux
- Windows Themes
- Windows Win32 Kernel Subsystem
If you’re using any of the aforementioned products, you can fix them easily with a patch management tool.
Solutions
To protect your devices, follow the steps in Microsoft’s security guides for each vulnerability and patch your software.
SanerNow Vulnerability Management, Risk Prioritization, and Patch Management detect and automatically fix vulnerabilities with risk-based remediation. Use SanerNow to keep your systems updated and secure.