The most recent Cisco breach is the infamous news in the industry today, with the networking giant being hacked by the Yanluowang Ransomware group.
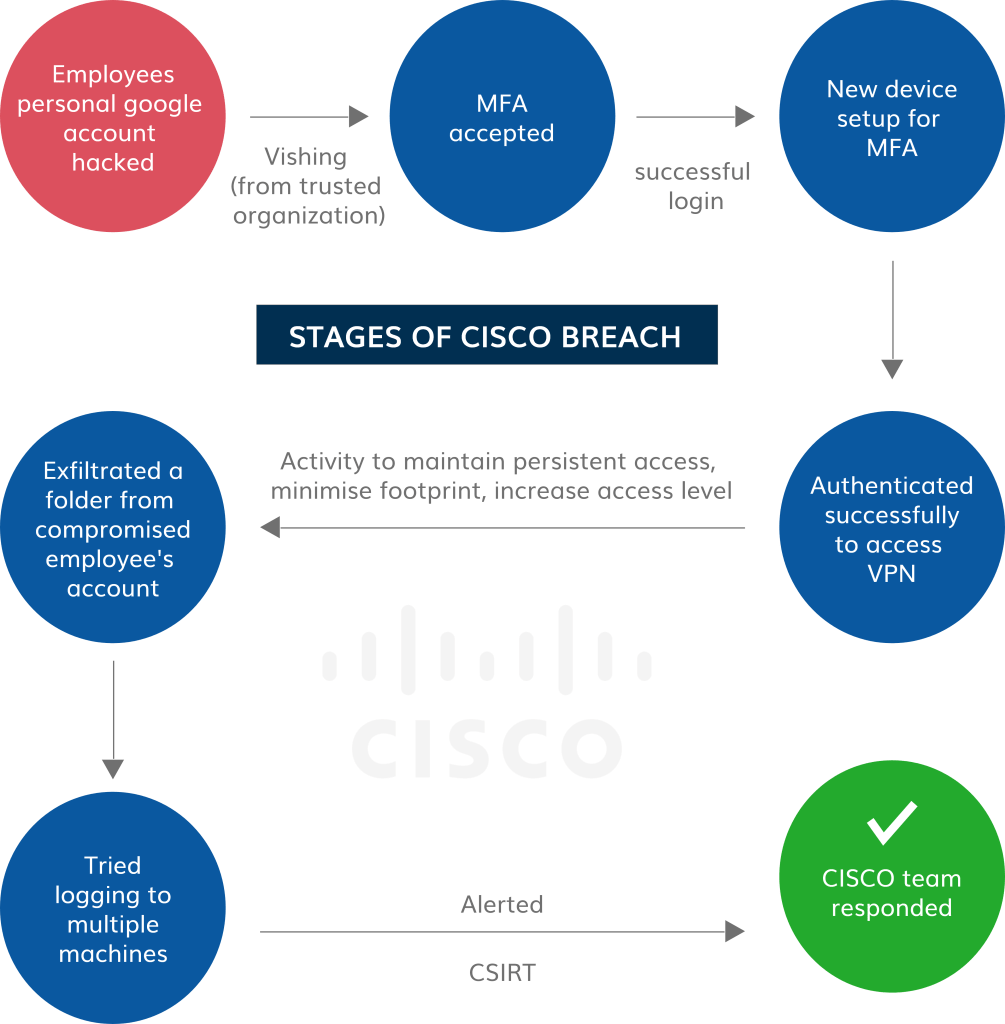
Attackers have gained access to a Cisco employee’s personal google account, where the company’s VPN credentials were stored. After syncing the information from the google account, attackers implemented numerous techniques to break the Multi-factor Authentication enabled in VPN. Through Vishing (voice phishing), a popular social engineering attack technique, attackers bypassed the MFA. They also started registering new devices for MFA to maintain persistent access and successfully authenticated to Cisco’s VPN. Therefore, to prevent such attacks, a continuous vulnerability management software is essential.
Followed by the MFA spoofing, attackers gained access to administrative privileges and logged in to multiple systems, which alerted the CISCO’s incident response team.
Subsequently, Cisco Security Incident Response Team responded to the incident. Cisco found no evidence of ransomware during the attack. However, the attacker group has stolen 2.8GB of data.
Although Cisco is a leading security organization with strong security controls in place, attackers invaded its network like child’s play. So, Organizations must stay even more vigilant now and implement robust precautionary and practice automated patching with a patch management tool and measures to stay ahead of such attacks.
Top Security Recommendations to Prevent Similar Attacks:
After analyzing the Cisco breach thoroughly, we have put together the key learnings and crucial security recommendations that you can implement in your network to prevent similar attacks:
Rigorously Patch Vulnerabilities in the Network:
During the Cisco breach, attackers could get their final leg in the network by gaining access to the administrative privileges. This security loophole is primarily due to unpatched vulnerability prevailing in the IT infrastructure. It is strongly recommended that IT security teams continuously run vulnerability scans and remediate the detected vulnerabilities with relevant patches on time.
Security Awareness Training for Employees:
Cisco attack proved that humans are the weakest link to initiate cyber attacks. Organization employees must undergo continuous cyber awareness training. They should be taught about the potential attacks, including social engineering attacks they can be exposed to. Employees must be aware of the organization’s security policy, and in case of any suspicious activity, they should report to the concerned security team immediately.
Enforce Password Vault in the Organization:
The primary reason behind the Cisco attack is the company credentials being stored in the employee’s personal account. Organizations should implement a secured password vault for employees to store their credentials. Employees should also be guided to refrain from storing company credentials in their personal accounts.
Continuously Monitor New MFA Registrations:
Enabling MFA is a crucial security practice organizations must implement in their network. Yet, it doesn’t stop with that. In Cisco’s case, attackers bypassed MFA and registered multiple devices in the account. Hence, IT security teams must continuously monitor the registered MFA accounts to identify if any intruder has entered the network.
Implement Application Control, Blacklist & Whitelist Applications:
After gaining access to the Cisco network, attackers have installed various tools in their network, including remote access tools like LogMeIn and TeamViewer, and threatening security tools like Cobalt Strike, PowerSpoilt, Mimikatz, and Impacket. Organizations must implement strong application controls and blacklist offensive security and remote access tools. They should also whitelist the necessary applications which can run in their network. IT security teams must continuously monitor the network for unauthorized applications to discover shadow IT.
Rethink Your Attack Surface with CyberPrevention in Mind
The Cisco breach left us with an unforgettable security lesson. Attack surfaces are massive, and attackers will not leave out even the tiniest security loophole in the network. IT security teams should start rethinking attack surfaces and manage numerous security risks in the network to deal with complex cyberattacks like these. To tighten the security posture, all security risks, such as software vulnerabilities, poorly configured settings, deviations from security controls, missing patches, and IT asset exposures, should be continuously detected and remediated.
Organizations need a robust CyberPrevention program to address vulnerabilities and security risks on time before they become a threatening attack. Moreover, the cost of implementing an advanced prevention program will be much lower than resolving incidents after they occur. And it will save organizations from becoming victims of malicious attacks.

