Ponemon Institute notes that around 60% of breaches could have been easily avoided if organizations had included a vulnerability management software to protect devices. Thousands of vulnerabilities in the cybersecurity space are discovered every year. Even a small failure to discover vulnerabilities in time and remediate them could lead to massive catastrophes and its critical to measure its success with some insightful vulnerability management program metrics is required to answer all this daunting chaos.
Implementing a vulnerability management tool is one step, but understanding the effectiveness of the program will make a huge difference.
How can you understand if your Vulnerability Management Process is working well?
Vulnerability Management, like any other process, should abide by certain parameters. The vulnerability management metrics play a crucial role in understanding the qualitative measurement for the security program.
Organizations need to learn about the top vulnerability management metrics or KPIs that are integral to vulnerability management. Also, in the long run, measuring the performance of your business in contrast with KPIs will give you an insight into accomplishing business goals. These metrics are the fundamental bricks and mortars of any vulnerability management program.
We’ve hand-picked the most important security metrics that vulnerability management should have to perform optimally. Any VM adhering to the following vulnerability management metrics might be a game-changer for your organization.
Important Vulnerability Management Program Metrics
1. Visibility over Network Assets
Visibility over network assets is the building block for any vulnerability management. IT teams need to ensure that all the devices and network ports spread across an organization are seamlessly scanned. This vulnerability management metric allows organizations to cover devices and look over them like clairvoyants. Having a transparent sight of network assets will help IT teams go beyond conventional methods of safeguarding them.
2. Scanning Time/Detection Time
Another crucial vulnerability management metric is the time taken to scan and detect vulnerabilities. The longer it takes to identify vulnerabilities in an organization, assessment and mitigation will be painful. Accordingly, you’ve to ensure that you opt for a vulnerability management program that scans for vulnerabilities at a faster rate.
3. Frequency of Scanning
When it comes to managing vulnerabilities, the frequency of scanning plays a vital role in detecting vulnerabilities. How frequently are the devices and networks scanned could change the dynamics of your organization’s cyber health! Periodic scanning isn’t the method to take on the ever-evolving vulnerabilities that are exploited regularly.
Failing to practice frequent scanning might lead vulnerabilities to spread to different devices over time. Ensure that you practice continuous vulnerability scanning and identify vulnerable loopholes regularly.
4. Accuracy of Scan
Accuracy plays a pivotal role in terms of vulnerability management. The most significant hazard that security teams face today is false positives. The occurrence takes place whenever a vulnerability scanner identifies an incorrect vulnerability.
False positives have become more common in the cybersecurity sphere. There are often instances where vulnerabilities are prevalent but have not been detected. The cause could be less information in the underlying data and inaccuracy in scanning. An accurate scanning makes it easier for security teams to discover and eliminate vulnerabilities.
5. Vulnerability Database Coverage
Vulnerability management relies on a database or a repository for security checks. The more security checks a repository has, the better the scanning, detection, and remediation becomes! Moreover, if you’re planning to make vulnerability management a breeze for your security teams, you should consider the VM tools relying on an extensive vulnerability database.
The more vulnerability checks a database has, the accuracy of detecting vulnerabilities becomes more robust.
6. Vulnerability Prioritization based on Risk Level
Gaining detailed insights into the detected vulnerabilities is a crucial part of a vulnerability management program. Vulnerability insights in real-time investigate to discover prevailing threats as per their CVS score or severity. Security teams foresee the scenario of threats and vulnerabilities that makes devices exploitable.
Understanding the type of impact these vulnerabilities could have on your IT infrastructure would make prioritization an inevitable practice. The insights will give a picture of the weaknesses in devices, affected devices, risk level, and operating system. Later, prioritizing the vulnerabilities as per their severity will lead to a seamless remediation process.
Vulnerability Management requires a robust and smartly curated plan to remediate vulnerabilities. Taking a random approach to remediate vulnerabilities will not suffice. After you understand the vulnerabilities impact level, assessing their prioritization level based on risk potential is essential. It would be best if you focused your efforts on remediating the most severe vulnerabilities first. This way, you will get rid of vulnerabilities with high-risk potential quickly.
7. Remediation Time
Vulnerability remediation time is one of the important vulnerability management metrics that determine the efficacy of a vulnerability management program. If remediation takes a long time, then the risk factors will intensify with every passing second. Further, this will also give an upper hand to the attackers to exploit more devices in your organization.
Opting for a fully-integrated vulnerability and patch management solution might reduce the time gap and fasten the remediation process.
8. Insightful Reports
Insightful reports bolster an organization’s take on addressing threats. Further, the process of auditing and reporting are KPIs that provide the necessary insights to keep the workforce safe and sound. Whenever security teams generate a report, they can run deep analysis to understand the flaws in the vulnerability management process. This aids them in taking the necessary steps in improving their vulnerability management processes.
Stay on top of your Vulnerability Management game with SanerNow
With SanerNow, you can meet all the requirements of a robust Vulnerability Management solution and ensure that the key parameters are met.
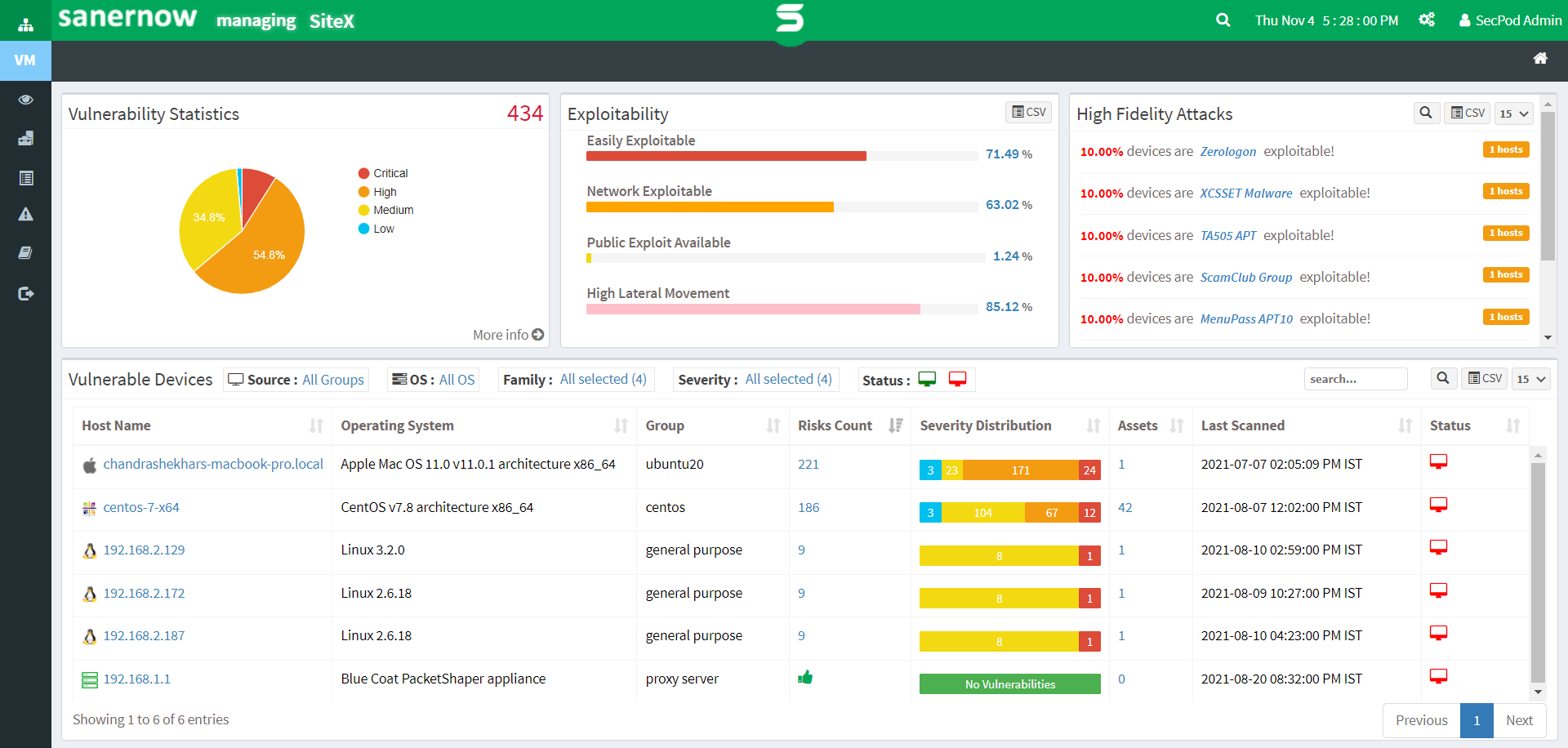
SanerNow allows you to:
- Monitor vulnerabilities across all your network devices
- Run the fastest VM scan in less than 5 mins
- Perform continuous scans with scheduled automation
- Detect vulnerabilities with precise accuracy
- Leverage the world’s largest vulnerability database with 160,000+ security checks.
- Gain detailed vulnerability insights and prioritize them based on their severity level
- Remediate vulnerabilities on time with integrated patch management
- Assess your vulnerability management process with insightful and customizable reports.
To experience the next level in vulnerability management, schedule a demo with SanerNow Today!