Given the constant evolution and increasing sophistication of cyber-attacks, it is essential to have a strong patch management lifecycle and patch management software to ensure the security of computer systems. Software vulnerabilities, misconfigurations, and other issues can leave your organization’s systems and sensitive data exposed to potential threats.
To minimize these threats, organizations need to implement a well-organized patch management process that includes identifying, downloading, testing, and deploying software patches or updates in a timely and efficient manner.
Read more: https://www.secpod.com/blog/sanernow-automated-patch-management-process-speed-up-patching-cycle/
In this article, we will discuss a detailed overview of the patch management lifecycle that can help safeguard an organization’s IT infrastructure and also know the obstacles faced by patch management tool.
Understanding the Patch Management Lifecycle
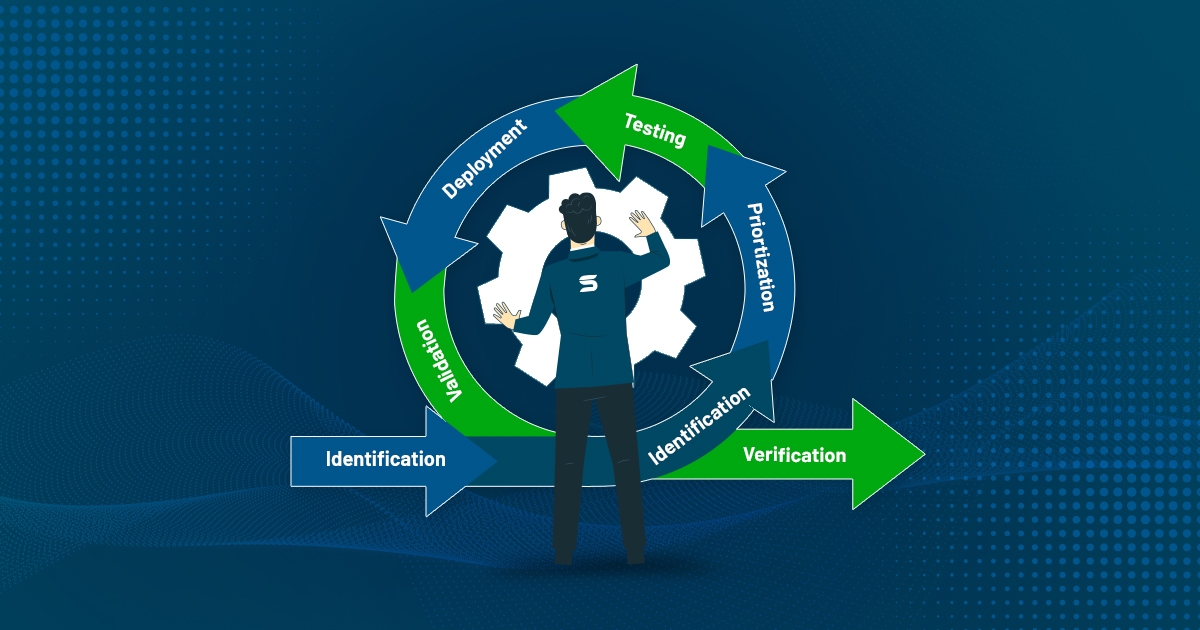
A reliable patch management software should be able to perform multiple crucial tasks actively, such as identifying patches, prioritizing the ones that need to be applied first, testing the patches, deploying them, and finally, verifying that they have been successfully implemented.
Identification:
The first step in the patch management lifecycle is to identify the patches or updates that need to be applied. This involves monitoring vendor sites for known vulnerabilities and updates.
This can also involve the use of automated tools to scan organizational assets for missing patches. The primary goal of this step is to identify and collect information about patches that are necessary to remediate potential cyberattacks.
Prioritization:
The second step is the prioritization of patches based on the severity of the vulnerability, CVSS scores, the potential impact of an attack, the criticality of the affected system, high-fidelity attacks, and more.
You can categorize patches according to their severity, such as critical, high, medium, or low. Assigning top priority and initial deployment should be given to the patches with high severity , such as critical ones. It would help to minimize the attacks associated with vulnerabilities by applying patches based on their severity level.
Read More: https://www.secpod.com/blog/why-is-it-important-to-prioritize-vulnerabilities-beyond-cvss/
Testing:
Before deploying patches, it is essential to test them in a non-production environment to ensure they do not cause any conflicts in the organizational IT environment.
You can accomplish this by creating a test environment that replicates the production environment. This step will assist in detecting any potential issues with the patches before deploying them to the production environment.
Deployment:
After testing, the patches can be deployed to IT assets either manually or through the use of automated patch management software. Automated deployment tools can help streamline the process and reduce the risk of human error. or any other malfunctions.
Validation (or) Verification:
Verifying the effectiveness of the patches after deployment is crucial. This ensures that we can address the vulnerabilities and secure the IT network of the organization.
Obstacles of Patch Management Lifecycle
Complexity:
Manually managing patches for a large number of systems can be challenging, particularly when dealing with different operating systems and software applications.
Time-consuming:
Testing patches can be time-consuming when done manually.
Manual deployment:
It needs human intervention at every step of the deployment process. Deploying patches manually might lead to errors and is challenging, particularly when dealing with remote and legacy devices.
Also read: https://www.secpod.com/blog/overcoming-the-challenges-of-vulnerability-management/
To overcome these challenges, organizations can implement various strategies, such as using automated patch management tools, continuous patch management software, leveraging cloud-based patch management solutions, and developing a patch management policy that outlines the whole patch management lifecycle.
Conclusion
Effective patch management software is critical for maintaining the security and stability of IT infrastructure. Organizations that implement a robust patch management process can reduce the risk of cyber-attacks, data breaches, and system failures.
To streamline the patch management process, choose automated third-party tools that support all the needs of third-party applications and operate continuously.