Microsoft has released October 2022 Patch Tuesday security updates, addressing 84 vulnerabilities. Indeed 13 are classified as critical as they allow the most severe types of vulnerabilities like privilege elevation, spoofing, or remote code execution and 71 are classified as important. However, the products covered in the October security update include Active Directory Domain Services, Azure, Azure Arc, Client Server Run-time Subsystem (CSRSS), Microsoft Edge (Chromium-based), Microsoft Graphics Component, Microsoft Office, Microsoft Office SharePoint, Microsoft Office Word, etc.
Microsoft October Patch Tuesday 2022 fixes two zero-day vulnerabilities, with one known to be actively exploited* in attacks (CVE-2022-41033*, CVE-2022-41043). Fixing a vulnerability can be done by using a patch management software.
Zero-Days Vulnerabilities discovered in Microsoft October Patch Tuesday 2022
CVE-2022-41033 | Windows COM+ Event System Service Elevation of Privilege (EoP) Vulnerability
This vulnerability is classified as critical and has a CVSSv3.1 score of 7.8 out of 10. However, Microsoft has not revealed how the vulnerability is being exploited. Indeed, all they mention is how simple the attack is and how no user involvement is necessary for the attacker to get SYSTEM capabilities.
CVE-2022-41043 | Microsoft Office Information Disclosure Vulnerability
The vulnerability exists due to excessive data which is output by the application in Microsoft Office. Successful exploitation allows a local user to gain unauthorized access to sensitive information on the system. To illustrate, according to Microsoft, attackers could use this vulnerability to gain access to users’ authentication tokens. A vulnerability management software can prevent this from occurring.

Critical Vulnerabilities
CVE-2022-37968 | Azure Arc-enabled Kubernetes cluster Connect Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 10 out of 10. Moreover, this flaw affects the cluster connect feature in Azure Arc-enabled Kubernetes clusters and can be exploited by an unauthenticated user to gain admin-level control over the cluster.
CVE-2022-38048 | Microsoft Office Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 out of 10. The flaw exists due to insufficient validation of user-supplied input in Microsoft Office. Exploit works when a victim is persuaded to download and open a specially designed file from a website by the attacker via social engineering, which results in a local attack on their machine.
CVE-2022-41038 | Microsoft SharePoint Server Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8 out of 10. Moreover, this flaw allows a network-based authenticated attacker to execute arbitrary code on the server, provided the account has “Manage List” permissions.
CVE-2022-37979 | Windows Hyper-V Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8 out of 10. However, to exploit this vulnerability, attacker requires to win a race condition. In brief, successful exploitation could allow an attacker on a nested Hyper-V environment to gain Level 1 Hyper-V Windows Root OS privileges.
Some more critical vulnerabilities found in Microsoft October Patch Tuesday 2022:
CVE-2022-37976 | Active Directory Certificate Services Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8 out of 10. Moreover, to execute a cross-protocol attack, a malicious DCOM client might force a DCOM server to authenticate to it via the Active Directory Certificate Service (ADCS). Successful exploitation could allow an attacker to gain domain administrator privileges.
CVE-2022-34689 | Windows CryptoAPI Spoofing Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5 out of 10.However, an attacker might use active public x.509 certificates to impersonate the targeted certificate and perform actions like authentication or code signing.
CVE-2022-33634, CVE-2022-22035, CVE-2022-24504, CVE-2022-38047, CVE-2022-41081, CVE-2022-30198, CVE-2022-38000 | Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerability
These vulnerabilities by Microsoft October Patch Tuesday 2022 have a CVSSv3.1 score of 8.1 out of 10. However, for successful exploitation, an attacker would need to send a specially crafted malicious PPTP packet to a PPTP server which results in remote code execution on the server side.
Microsoft Security Bulletin Summary for October 2022
- Active Directory Domain Services
- Azure
- Azure Arc
- Client Server Run-time Subsystem (CSRSS)
- Microsoft Edge (Chromium-based)
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft WDAC OLE DB provider for SQL
- NuGet Client
- Remote Access Service Point-to-Point Tunneling Protocol
- Role: Windows Hyper-V
- Service Fabric
- Visual Studio Code
- Windows Active Directory Certificate Services
- Windows Defender
- Windows DHCP Client
- Windows Group Policy
- Windows Group Policy Preference Client
- Windows Internet Key Exchange (IKE) Protocol
- Windows Kernel
- Windows NTFS
- Windows NTLM
- Windows Security Support Provider Interface
- Windows Server Remotely Accessible Registry Keys
- Windows Server Service
- Windows Storage
- Windows TCP/IP
Products affected by Microsoft October Patch Tuesday 2022 vulnerabilities:
Product: Microsoft Windows
CVEs/Advisory: CVE-2022-22035, CVE-2022-24504, CVE-2022-30198, CVE-2022-33634, CVE-2022-33635, CVE-2022-33645, CVE-2022-34689, CVE-2022-35770, CVE-2022-37965, CVE-2022-37970, CVE-2022-37973, CVE-2022-37974, CVE-2022-37975, CVE-2022-37976, CVE-2022-37977, CVE-2022-37978, CVE-2022-37979, CVE-2022-37980, CVE-2022-37981, CVE-2022-37982, CVE-2022-37983, CVE-2022-37984, CVE-2022-37985, CVE-2022-37986, CVE-2022-37987, CVE-2022-37988, CVE-2022-37989, CVE-2022-37990, CVE-2022-37991, CVE-2022-37993, CVE-2022-37994, CVE-2022-37995, CVE-2022-37996, CVE-2022-37997, CVE-2022-37998, CVE-2022-37999, CVE-2022-38000, CVE-2022-38003, CVE-2022-38016, CVE-2022-38021, CVE-2022-38022, CVE-2022-38025, CVE-2022-38026, CVE-2022-38027, CVE-2022-38028, CVE-2022-38029, CVE-2022-38030, CVE-2022-38031, CVE-2022-38032, CVE-2022-38033, CVE-2022-38034, CVE-2022-38036, CVE-2022-38037, CVE-2022-38038, CVE-2022-38039, CVE-2022-38040, CVE-2022-38041, CVE-2022-38042, CVE-2022-38043, CVE-2022-38044, CVE-2022-38045, CVE-2022-38046, CVE-2022-38047, CVE-2022-38050, CVE-2022-38051, CVE-2022-41033
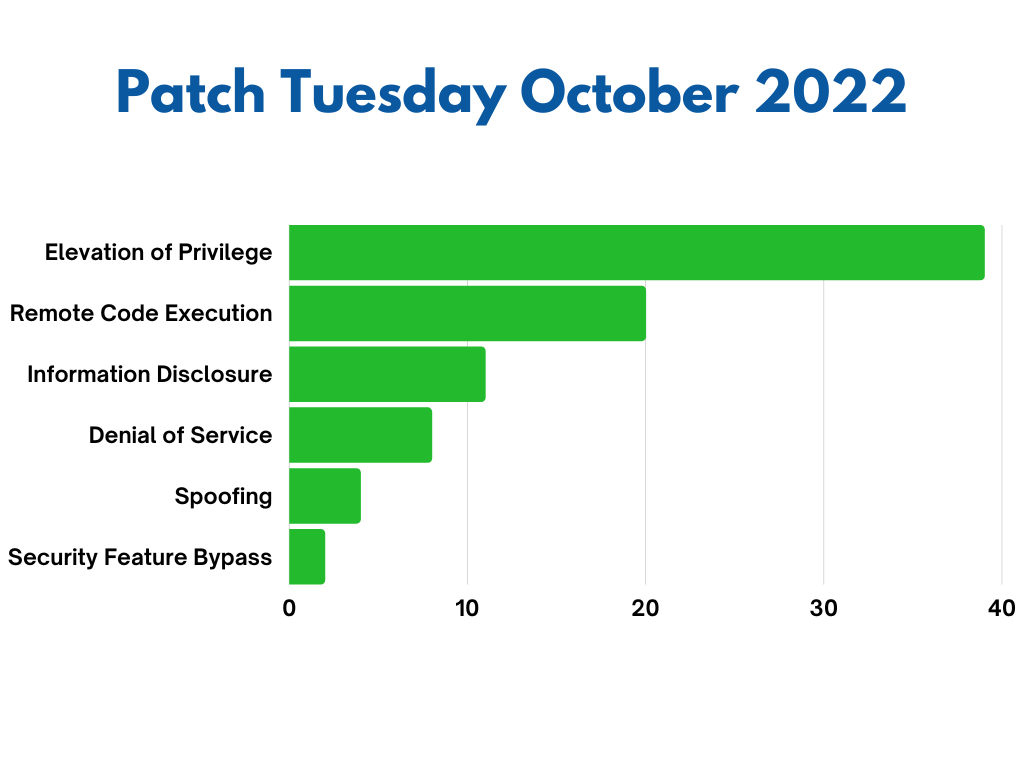
Impact: Denial of Service, Elevation of Privilege, Information Disclosure, Remote Code Execution, Security Feature Bypass, Spoofing
KB’s: 5016616, 5016622, 5016623, 5016627, 5016629, 5016639, 5016672, 5016681, 5016683, 5016684, 5018410, 5018411, 5018418, 5018419, 5018421, 5018425, 5018427, 5018457, 5018474, 5018476, 5018478
Product: Microsoft Office
CVEs/Advisory: CVE-2022-38001, CVE-2022-38048, CVE-2022-38049, CVE-2022-38053, CVE-2022-41031, CVE-2022-41036, CVE-2022-41037, CVE-2022-41038, CVE-2022-41043
Impact: Remote Code Execution, Information Disclosure, Spoofing
KB’s: 5002026, 5002278, 5002279, 5002283, 5002284, 5002287, 5002288, 5002290
Product: Azure
CVEs/Advisory: CVE-2022-37968, CVE-2022-35829, CVE-2022-38017
Impact: Elevation of Privilege, Spoofing
However, SanerNow VM and SanerNow PM detect and automatically fix these vulnerabilities by applying security updates. Therefore, use SanerNow and keep your systems updated and secure.

