Microsoft warned that two zero-day vulnerabilities ( CVE-2022-41040 and CVE-2022-41082 ) are being used against Exchange Server without a patch. CVE-2022-41040 is a Server-Side Request Forgery (SSRF) vulnerability, and CVE-2022-41082 allows remote code execution when PowerShell is accessible to the attacker, Microsoft explained. Moreover, Microsoft has not released the patch for these vulnerabilities yet. A good Vulnerability Management tool can prevent these attacks.
Microsoft is currently aware of targeted attacks utilizing these two flaws. Therefore, These attacks allow an authenticated attacker to trigger CVE-2022-41082, thanks to CVE-2022-41040 remotely. It should be highlighted that to exploit either vulnerability properly, authenticated access to the vulnerable Exchange Server is finally required. Vulnerability Management System can resolve these issues.
Researchers claim that CVE-2022-41082, CVE-2021-34473, and the 2021 Proxy Shell vulnerability are closely in connection. However, the new exploit’s request string was made public, and it is the same as the one from the previous year’s vulnerability, as is the Microsoft mitigation.
These vulnerabilities are reporting by the Vietnamese cybersecurity company GTSC as part of its response to a customer’s cybersecurity incident in August 2022; hence, it said the two zero-days used in attacks on their customers’ environments dating back to early August 2022.
A Chinese threat group is suspecting to be responsible for the ongoing attacks as the web shell codepage uses character encoding for simplified Chinese. Moreover, the attacks have also finally deployed the China Chopper web shell in attacks for persistent remote access, a backdoor commonly in use by China state-sponsored hacking groups.
At this time, GTSC has NOT released any technical details regarding this new zero-day vulnerability.
Mitigations
Exchange Online customers do not need to take any action.
The current Exchange Server mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> URL Rewrite -> Actions” to block the known attack patterns. Exchange Server customers should review and choose only one of the following mitigation options.
Option 1: For Microsoft Exchange users who have the Exchange Emergency Mitigation Service (EEMS) enable, Moreover, Microsoft releases the URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. The mitigation will finally enable automatically.
Option 2: Run the Exchange On-premises Mitigation Tool v2 (EOMTv2), available on Microsoft GitHub.
Option 3: Exchange users can follow the below instructions, which are currently in discussion publicly, and therefore successfully break current attack chains. 1. Open IIS Manager.
2. Select Default Web Site.
3. In the Feature View, click URL Rewrite.
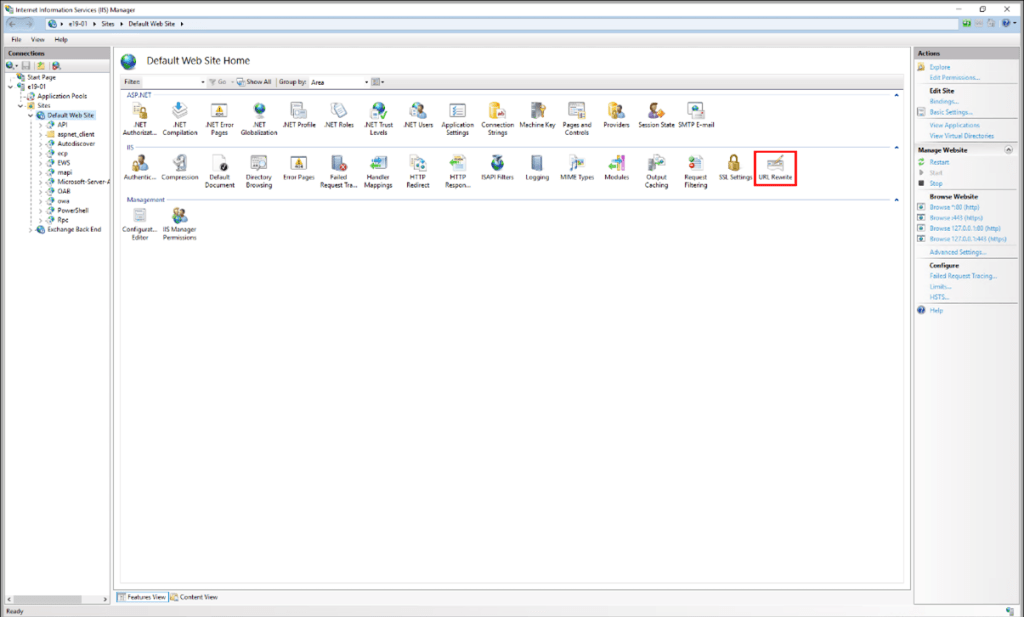
4. In the Actions pane right-hand side, click Add Rule(s)…
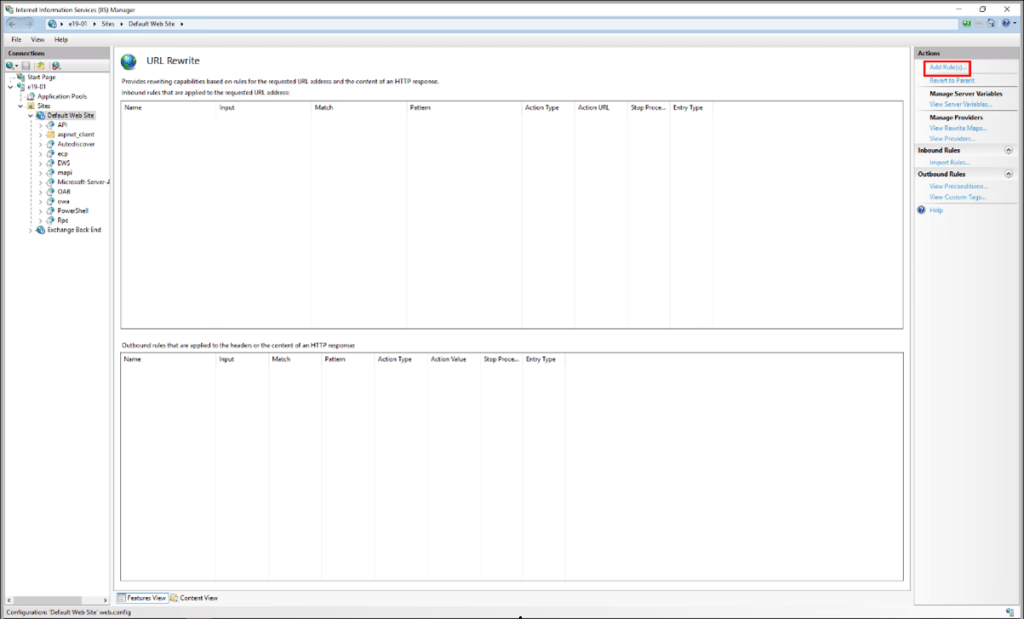
5. Select Request Blocking and click OK.
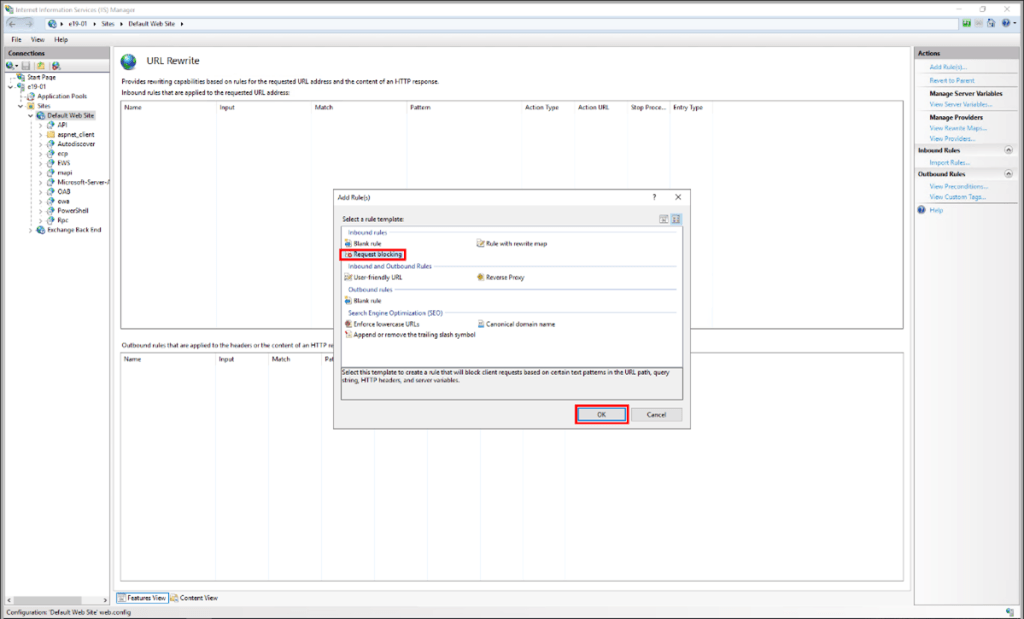
6. Add the string “.*autodiscover\.json.*\@.*Powershell.*” (excluding quotes).
7. Select Regular Expression under Using.
8. Select Abort Request under How to block and then click OK.
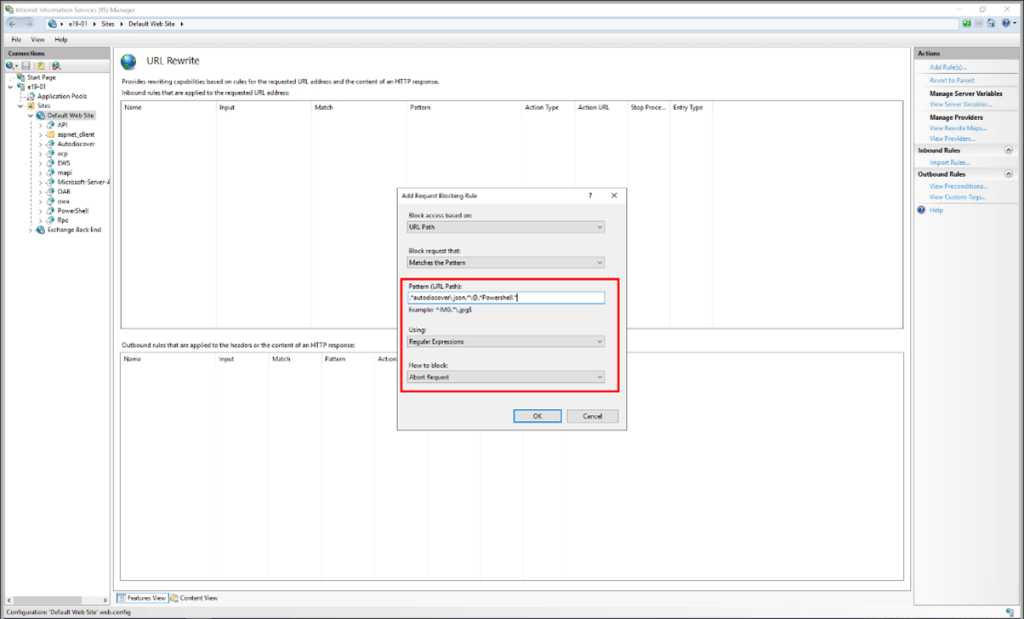
9. Expand the rule and select the rule with the pattern .*autodiscover\.json.*\@.*Powershell.* and click Edit under Conditions.
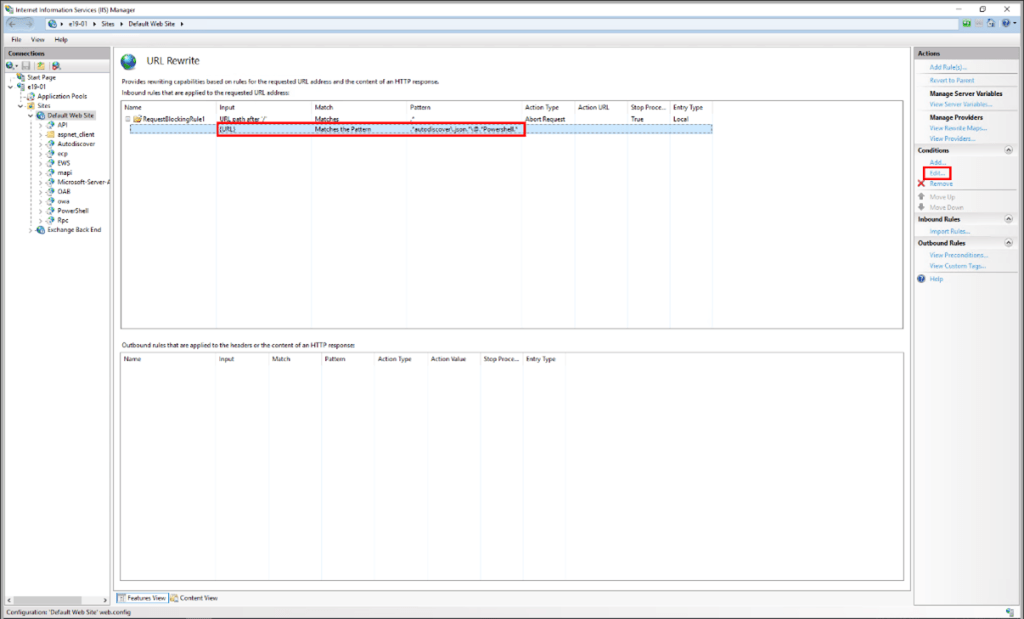
10. Change the Condition input from {URL} to {REQUEST_URI}
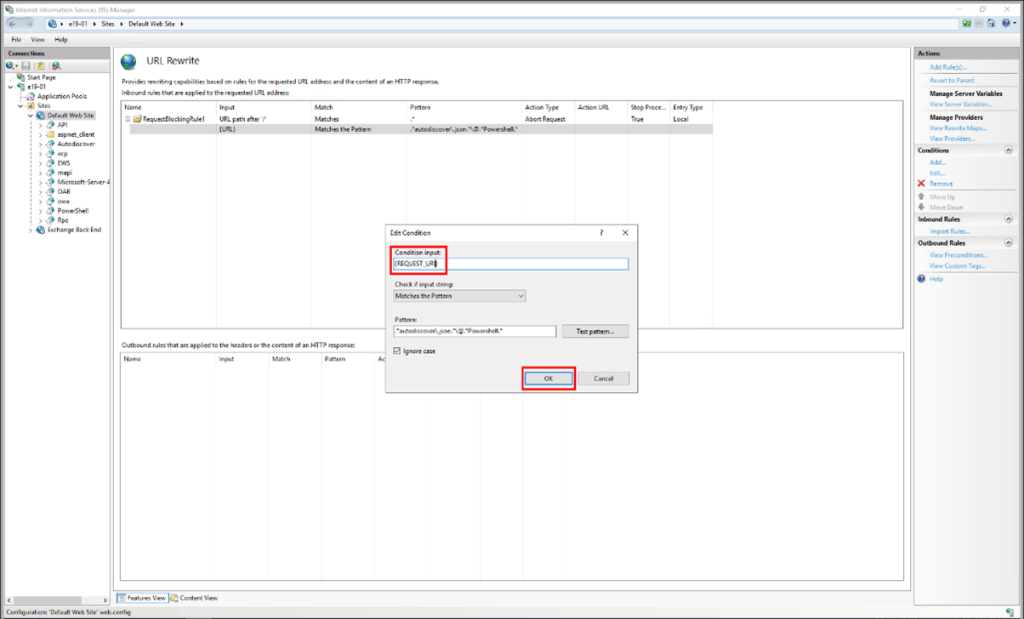
NOTE: If it is needed to change any rule, it is best to delete and recreate it.
Impact: There is no known effect on Exchange functionality if URL Rewrite is installed as recommended.
Microsoft strongly recommends Exchange Server users disable remote PowerShell access for non-admin users in their organization.
SanerNow VM detects these vulnerabilities. Use SanerNow and keep your systems updated and secure.

