Digital transformation has pushed the boundaries of business operations. With expanding boundaries, there’s a drastic increase in the probability of cyberattacks. Organizations of all industries and sizes are at risk. Even though organizations pay attention to security on some level, they still experience attacks. Here we can use a vulnerability scanning tool to stay ahead of these attacks. Are they not paying enough attention? Is anything missing from their strategy? This is where cyber hygiene comes into the picture.
What is cyber hygiene?
IT assets now have more loopholes than ever which can be patched using a patch management tool. They are easy to exploit and can cause larger disruptions to the business. Unfortunately, such fragile environments exist in almost all organizations and cause a huge discomfort to IT security. Thus, a standardized security framework will ensure stronger, reliable, and scalable security measures, protecting the IT network from all potential risks.
Cyber hygiene is the process of following routine IT security and management measures. It keeps assets in their best health and helps operate with maximum security.
Benefits of cyberhygiene Framework
Adopting organizational cyber hygiene comes with a handful of benefits.
1. Stronger security posture
A cyber hygiene routine makes sure all security checks are done in time. As a result, the overall security posture improves and gets stronger.
2. Building repeatable processes for the security team
The best way to ensure consistency is to build a process. In other words, a routine with a defined workflow. When security teams repeat a process over and over again, they build a habit. Thus, defining a cyber hygiene routine ensures the security team meets the said security measures consistently and does not miss out on security checks.
3. Measurable KPIs for the board
The board or top management asks only one question. “How secure are we?”. Cyber hygiene is a great way to quantify security with KPIs and present it to the board. You can lead with the story of cyber hygiene and how it can prevent incidents before they occur. Then, you get to build and present a list of cyber hygiene measures for the board and show progress.
4. Ensuring business continuity
An important benefit of cyber hygiene is business continuity. Security issues are detected and fixed in advance. As a result, they do not escalate to a level beyond control and affect employee productivity to bring business to a grinding halt.
How does cyber hygiene influence security posture?
Instead of waiting for critical risks or threats to show up at the doorstep, cyber hygiene focuses on proactively seeking and mitigating risks.
The below graphs are hypothetical re-creations of a real-world IT environment. They are represented for a period of 6 weeks. We have taken the scenarios of two different companies to explain better. Firstly, Company A follows a standard routine through a cyber hygiene framework. It performs risk scanning, assessment, and remediation every week. In contrast, Company B has no routine. IT doesn’t follow a cyber hygiene framework. Security measures are done less frequently at the end of a month (week 4).
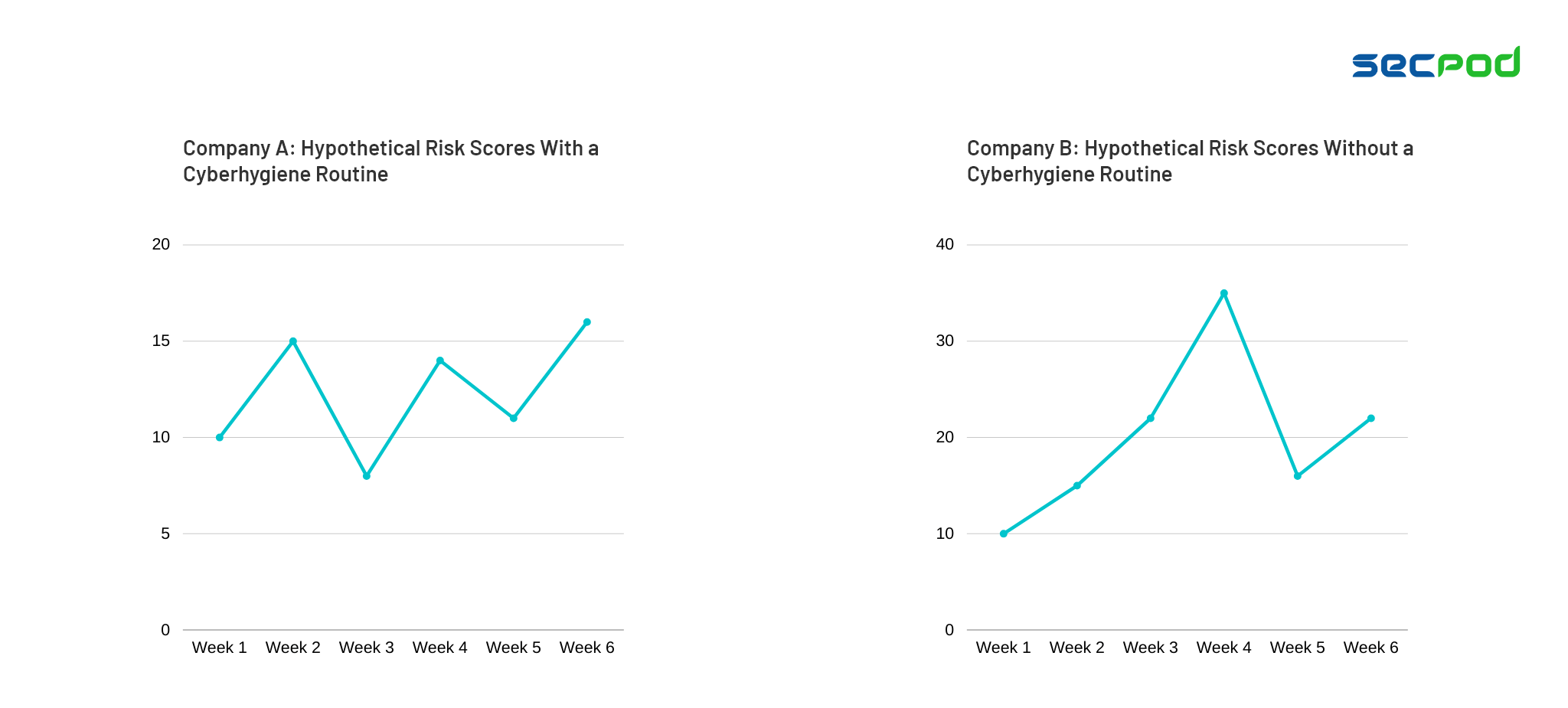
As you see in the two graphs, Company B is exposed to high risk for a period of 2 weeks. They do not stick to a consistent and frequent routine. In contrast, company A has a standardized playbook (cyber hygiene framework) to follow. The result? Lower and consistent risk scores guaranteeing a stronger security posture.
What is a cyber hygiene framework?
A cyber hygiene framework is a checklist to ensure you keep an eye on all important security measures. An established cyberhygiene checklist ensures you keep an eye on all important security controls and don’t miss out on any. In addition, you need a set of parameters to analyze during every routine to assess your security posture.
Components of a cyberhygiene framework
The following core security measures serve as a checklist for the overall cyberhygiene framework.
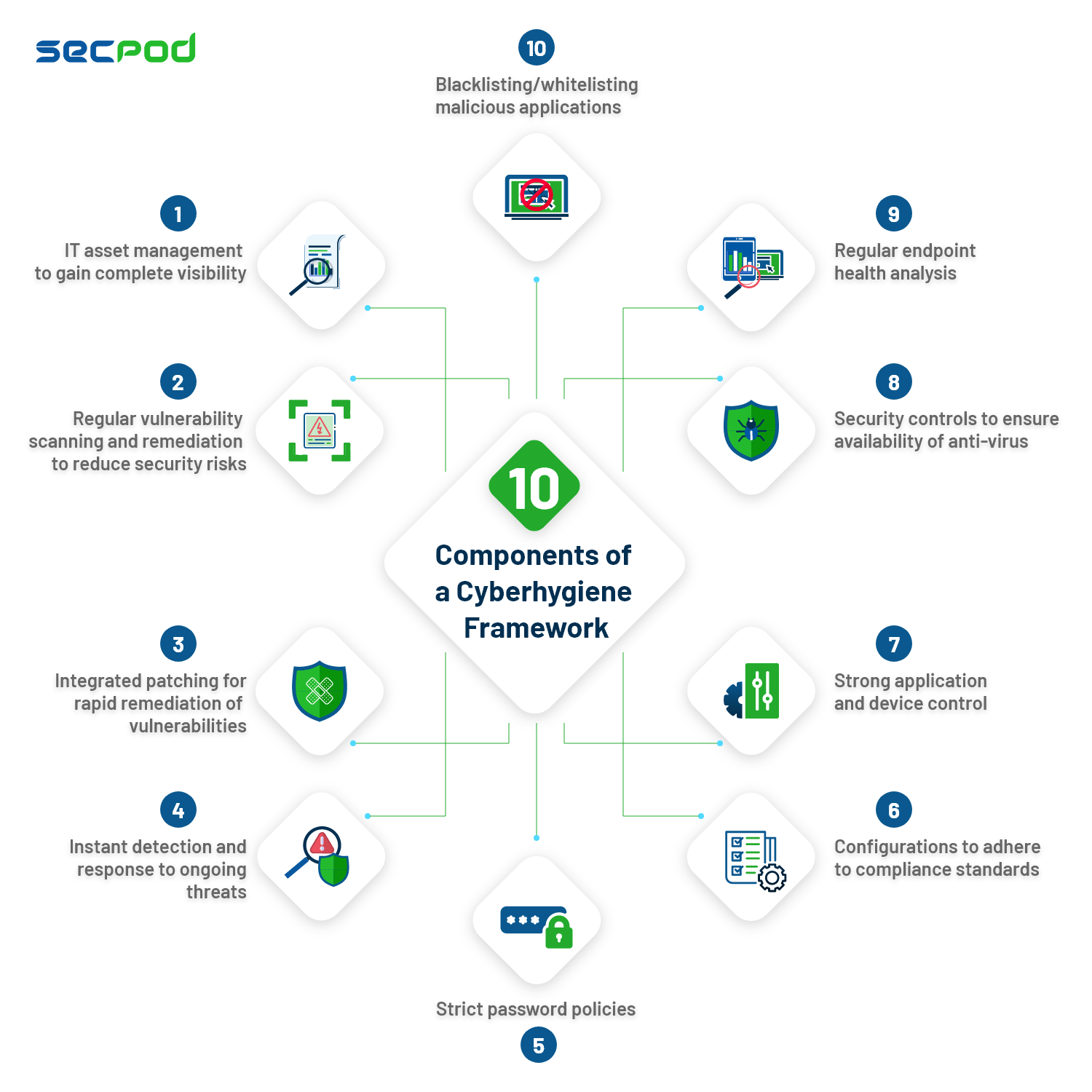
1. IT asset management to gain complete visibility
Getting complete visibility over the hardware and software inventory is the first step of cyber hygiene. You cannot protect what you cannot see. Your routine should include continuous asset scans. They help attain complete visibility of all the hardware and software used in your organization.
2. Blacklisting/whitelisting malicious applications
After accounting for all the applications present in your networks, evaluate their usage/requirement. Users might knowingly or unknowingly install malicious applications. These may pose serious risks to the entire environment. Hence, you need to blacklist or whitelist them accordingly. Your cyber hygiene framework should focus on filtering out malicious software and allow only essential software to operate in the network.
3. Regular endpoint health analysis
Endpoints are vital IT assets to guarantee uninterrupted business operations. Health and everyday endpoint management should happen seamlessly as part of the cyber hygiene routine. Hence, you need to regularly monitor endpoint health metrics, system performance, processes, and services. All these guarantee smooth business operations.
4. Security controls to ensure availability of anti-virus
Anti-virus constantly monitors and warns you about ongoing threats like malware and data corruption. It detects threats in your devices based on historic malware signatures. Install anti-virus software in all endpoints and make sure it is up-to-date.
5. Regular vulnerability scanning and remediation
Software vulnerabilities in endpoints are one of the primary areas of IT risk management. Your cyber hygiene framework should be capable of running continuous real-time scans to detect, assess, and prioritize vulnerabilities based on their severity level. The process should make further remediation easy to execute.
6. Integrated patching for rapid remediation of vulnerabilities
Patching helps organizations run the latest version of the software. Beyond staying updated, it also remediates vulnerabilities in software. A few organizations pay importance to vulnerability assessment. However, they see patching as a separate step for another time. Integrated patch management controls can correlate vulnerabilities with the respective patches. They go a long way in bringing down security risks without manual work and delays.
7. Strong application and device control
Careless use of malicious applications, USB devices, and other peripheral devices can invite security breaches. Implement strong application and device control on your endpoints. It blocks any malicious devices or applications immediately. Keep a constant watch on your device and application portfolio to detect new changes immediately.
8. Configurations to adhere to compliance standards
Compliance with security standards is a business requirement for many organizations. Many organizations also implement customized policies in their environment. The cyber hygiene framework should also accommodate regular checks to identify non-compliant endpoints. Harden the non-compliant endpoints hand-in-hand during each routine.
9. Strict password policies
Setting up a complex and unique password for all the devices prevents both insider and outsider threats. Enforce strict password policies to secure enterprise endpoints. A well-built cyber hygiene framework with strong password policies serves as a protective moat for the business.
10. Instant detection and response to ongoing threats
Identifying and responding to indicators of attack and compromise (IOA and IOC) across your endpoints is crucial to protect your network from ongoing threats. This is not necessarily a routine. However, it’s an always-on, reactive security measure that can sound off alarms when there’s something fishy.
Implement an all-round cyber hygiene framework with SanerNow
SanerNow CyberHygiene Platform is the first in the market to have a full-fledged cyber hygiene tool stack. It has all 6 major applications required to build a strong and scalable cyberhygiene framework. They are Vulnerability Management, Patch Management, Asset Management, Endpoint Management, Compliance Management, and Endpoint Threat Detection and Response. They are the key applications of SanerNow, which form the framework.
Levering the world’s largest vulnerability intelligence database, cloud–based console, a single multifunctional agent with one server, and intelligent capabilities, SanerNow swiftly orchestrates and automates cyber hygiene among endpoints, assuring a strong security posture.