Cisco has released a Security Advisory for the actively exploited worldwide CVE-2020-3452. Cisco Read-Only Path Traversal Vulnerability in the web services interface of Adaptive Security Appliance (ASA) Software and Firepower Threat Defense (FTD) Software could allow an unauthenticated, remote attacker to perform directory traversal attacks & read sensitive files on the system. Moreover, With the correct vulnerability management tool, you can easily detect and remediate this instantly.
Rapid 7 Researchers found over 85,000 ASA/FTD internet-accessible devices which are a huge threat and should be looked at with concern, based on the “uptime” technique. In this technique, hping is used to determine device uptime from timestamps and to detect devices that reboot for patch since the exploit release. Systems with an up-time higher than the release time of the patch are technically vulnerable. Researchers also added that only about 10% of the ASA/FTD devices rebooted (patched) since the release of the updates ASAP. If the devices are unable to update ASAP, the exploitation of a large number of devices can occur in the near future. To prevent this exploitation, a good vulnerability management software will be helpful.
Vulnerability Details:
The path traversal vulnerability CVE-2020-3452 exists in affected devices due to a lack of proper input validation in HTTP requests in the web services interface of ASA/FTD. Moreover, an attacker can exploit this vulnerability by sending a crafted HTTP request containing directory traversal character sequences to an affected device. On Successful exploitation of the vulnerability, an attacker is limited to reading arbitrary files only within the web services file system, which may also contain information such as WebVPN configuration, bookmarks, web cookies, partial web content, and HTTP URLs. Cisco claims that this vulnerability is useless to access web services ( ASA or FTD) system files or the underlying operating systems (OS) files. On affected devices, the web services file system is enabled when it is configured with either WebVPN or AnyConnect features.

The devices listed below are vulnerable to a typical crafted HTTP request that takes use of this path traversal vulnerability flaw to access the contents of the file “portal_inc.lua” in Cisco ASA and Cisco Firepower:
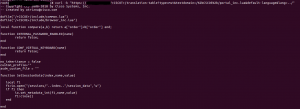 Command used:
Command used:
curl -k “https://<domain>/+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../”
Publicly available PoC:
The proof-of-concept codes are publicly available for the vulnerability.
- Exploit Payloads on Twitter.
Impact:
This path traversal vulnerability allows an unauthenticated, remote attacker to perform directory traversal attacks and hence read sensitive files on a targeted system.
Affected Versions:
The path traversal vulnerability affects Cisco devices running a vulnerable release of Cisco ASA/FTD software with a vulnerable configuration of AnyConnect or WebVPN.
Vulnerable ASA Software Features:
- AnyConnect IKEv2 Remote Access (with client services)
Vulnerable Configuration: crypto ikev2 enable <interface_name> client-services port <port #> - AnyConnect SSL VPN
Vulnerable Configuration: webvpn
enable <interface_name> - Clientless SSL VPN
Vulnerable Configuration: webvpn
enable <interface_name>
Vulnerable FTD Software Features:
- AnyConnect IKEv2 Remote Access (with client services)
Vulnerable Configuration:
crypto ikev2 enable <interface_name> client-services port <port #> - AnyConnect SSL VPN
Vulnerable Configuration: webvpn
enable <interface_name>.
This path traversal vulnerability affects only the products with the listing of the Vulnerable Products section of the advisory. Additionally, Cisco also confirmed that this vulnerability does not affect Cisco Firepower Management Center (FMC) Software.
Solution:
Cisco has published a security advisory addressing path traversal vulnerability CVE-2020-3452.
Therefore, We strongly recommend installing security updates without any delay.

Do we have any IOCs for this vulnerability? If it is being exploited, where is the evidence? There is no information online as to what to look out for? What type of threat actor is actively using this?
Cisco has confirmed that this vulnerability is being actively exploited in the advisory. In this article, we have included technical details about this vulnerability.