Are you willing to read reports which are 10,000 pages long? Not me, though. Vulnerability management reports are crucial while strategizing or auditing your organization’s security posture. An effective vulnerability management report should not be long and hard to read but contain all the necessary details of the vulnerability management process.
Vulnerability reports should easily summarize detected vulnerabilities and risks they possess and also provide the means of remediation through a patch management software.
This blog lets us quickly understand what we mean by vulnerability management reports. Why is it important? And the must-haves to make good vulnerability management reports.
What is a Vulnerability Management Report?
You need a vulnerability management tool to prevent cyber-attacks and secure your organization from attackers. Vulnerability management is a process of identifying vulnerabilities, assessing, prioritizing, and remediating them.
A vulnerability management report represents the outcome of the vulnerability management process. Using this report, you can better understand your organization’s risks and develop strategies for overcoming them.
Why is Vulnerability Management Report Important?
There are many scenarios where a vulnerability management report will be beneficial. For instance, your auditor would have raised reports to check if the organization meets all compliance standards, such as HIPAA, SOC, NIST, etc.
Having reports allows you to analyze potential threats and strategize the mitigation process. A detailed and precise report will help you ensure that your organization’s security is adequate.
Must Haves of a Good Vulnerability Management Report
1. Detailed Summary:
This should contain an overview of the vulnerability management process. It should give a high-level understanding to the users; it typically includes the number of vulnerabilities identified, the impact vulnerability can have on your organization, their CVSS score, and more.
2. Severity assessment:
After having the information about the detected vulnerabilities, make sure your reports also contain information about their severity levels. This would be vital information when you start remediating them.
3. Elaborate findings:
It is essential to elaborate on the detected vulnerabilities. For example, if you would have found a vulnerability, showcase it through their assigned CVE, their CVSS score, and the severity of that vulnerability so that you can get a precise idea about them in one place.
4. Use Charts and graphs:
Reports with graphs and charts are easily understandable, and at the same time, they give you accurate information and make your report attractive and easy to read.
5. Vulnerability statistics:
This represents detected vulnerabilities based on severity levels.
6. Vulnerability aging:
Time since vulnerabilities has been present in your operating system. This information helps you know if any vulnerabilities have not been remediated for a long time.
7. Impacted hosts:
Have a list containing the data about the number of vulnerable and non-vulnerable hosts.
8. Vulnerable hosts:
List of vulnerable hosts with their group ID, number of vulnerabilities present, and their severity details.
9. Patch statistics:
List of patches available and the number of vulnerable instances.
10. Automated reports:
Different tools in the market can provide you with canned reports that can be customized based on your requirements. Choosing them will reduce human error, and you will have a choice of representing the information you truly need.
SanerNow’s Vulnerability Management Reports
SanerNow vulnerability management provides canned and customizable insightful reports. Canned reports are the one that is already in-built based on your organization’s performance, and customizable reports are the one where you can drag and drop tables/ charts/graphs based on your requirements.
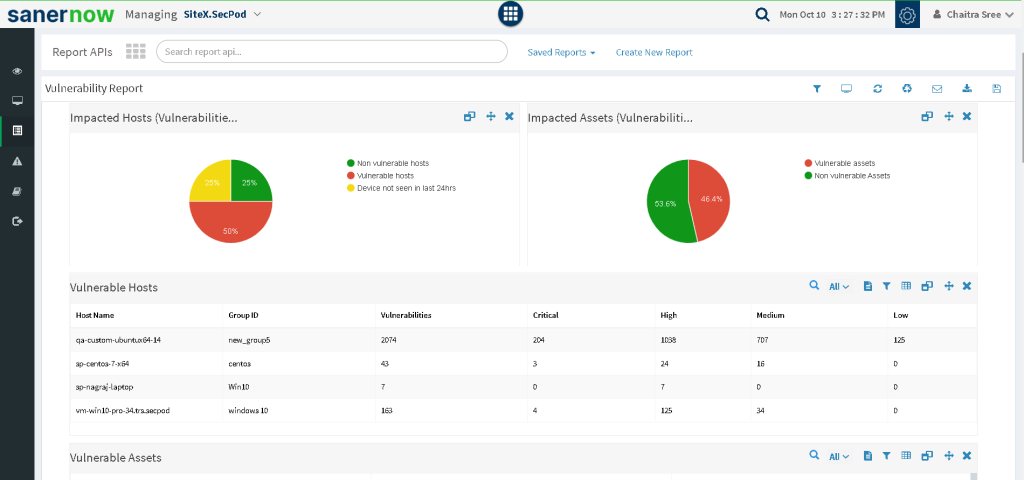
You can export reports in PDF format and also have a backup scheduled. Apart from these features, you can receive reports to your specific mail address. You can take a look at how SanerNow provides insights on vulnerability in our Sample Report.
SanerNow also provides a comprehensive Risk Assessment Report with detailed insights on the vulnerabilities and other security risk exposures in your network