As the global pandemic, COVID-19 is hitting the world hard, organizations’ workforces are now working from home. No company can easily work without regular meetings, team communications, partner and client calls, webinars, online training, video-conferences etc. Not just corporate organizations, even the educational institutions are dependent on these remote meeting software to continue their regular classes. Since everything is remote nowadays, cyber attacks can be easily done. A vulnerability management solution can stop these attacks.
Is your remote meeting software secure?
To be more precise, right now everyone in the world requires a platform which will help them connect with their friends, colleagues, and customers. This need has thus led to a huge surge in the download of remote meeting software across the globe. Overnight Zoom reported an increase in daily online meetings by over 20 times. Zoom CEO Eric S Yuan claims in his note to his application’s users that almost 200 million people are meeting on Zoom daily. That’s more than half of the US population.
There is no doubt these remote meeting software are helping businesses function smoothly, but are we looking at the security aspects of such software? The security aspects can be maintained using a patch management solution.
Remote meeting software, the new eye candy for cyber attackers:
It is evident that the world is running on these remote meeting software. This has eventually gained more attention from cyber attackers worldwide. Billions of user data are now available in these software and are serving as new eye candy for cyber attackers. One of the most trending software which connects audiences across the globe today is Zoom. Off late, the media is flooded with news on how Zoom is being played around by attackers. One of the biggest security issue Zoom is facing right now is “Zoom bombing”, where an uninvited user breaks into and disrupts the meeting. This Zoom bombing has also led to severe security outbreaks like stealing user accounts and user sensitive information.
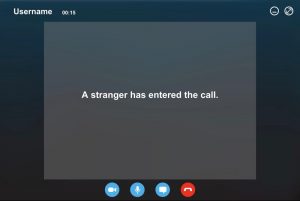
An article claims that millions of user accounts and their credential details are now available for free on hacker forums. This is a serious security threat which puts organizations IT security at doubt. CERT-In, the national agency to combat cyber-attacks and guarding the cyberspace, has announced that the unguarded usage of Zoom can be vulnerable to cyber-attacks, which might lead to leakage of sensitive information to cybercriminals.
Few recommendations to prevent hackers from being unwanted guests in your online meetings:
Here are a few recommendations users can follow to prevent scenarios like Zoom bombing,
- Set a complex unguessable password for all scheduled meetings and webinars. This will prevent hackers from guessing passwords and stealing sensitive information.
- Enable ”waiting room” feature so that the owner of the call will have better control over the participants. On doing this, the participants will be allowed to join a virtual ”waiting room”, but the call owner will have the control to approve them. This restricts unwanted entrants from business calls.
- Disable ”join before host” feature as it lets other participants to continue the meeting in the absence of an actual call owner or the host. This will prevent other participants from hosting the meeting after the call owner leaves. If needed, you can allow trusted participants to host meetings using “schedule privilege” option.
- Restrict or disable file transfer during the meetings. This is to protect the sensitive organization’s data.
- Limit screen sharing to the call owner or host only. This ensures that others don’t get to view the screens unnecessarily.
- Ensure that the removed participants are not able to re-join the call. This prevents unwelcomed users from attending the call.
- Lock the meetings, webinars or sessions once everyone joins and allow only the trusted participants to record the session. This will again save critical calls from the entry of unwanted users and saves sensitive business information.
Patching, the most important recommendation to secure Remote Meeting Software like Zoom:
In the previous section, we saw a few recommendations which users can follow while using remote meeting applications. But the foremost recommendation or a security measure suggested to safeguard these remote meeting software is to perform patching on time. As these software are prone to various vulnerable loopholes, patches are still available to fix them. IT teams are recommended to continuously patch these applications to secure their IT network from potential cyber breaches.
SecPod SanerNow, the solution which automates patching and secures your remote meeting software:
If you are wondering about how you can simplify and automate patching of these remote meeting software, SecPod SanerNow is the solution you should opt for. SecPod SanerNow automates end to end tasks of patch management right from scanning the missing patches, downloading them from the vendor sites to deploying them on target computers. All you have to do is install Saner Agents on the enterprise endpoints and create automated patch deployment tasks to roll out the missing patches. This is how you can easily patch Zoom or any remote meeting software.
Along with this, SanerNow assists you to take security steps beyond patching by letting you perform various other endpoint security and management actions like vulnerability management, compliance management, endpoint management, software deployment, application and device control, threat detection and response etc., from a centralized SanerNow console.
It is always better to stay proactive than to be a victim of these security breaches. Without any delay, Download SecPod SanerNow and secure your IT network now.
Written by,
Dixitha.S
Product Marketing Lead