Today, many enterprises need cybersecurity solutions to deal with the growing IT security threats. Cyberattacks like ransomware are escalating the importance of vulnerability assessment, prioritization, and instant remediation for small, medium, and large-sized enterprises. Cyberhygiene measures continue to be a foundational component of cybersecurity strategy. Therefore, enterprises need to go beyond their existing elementary vulnerability program and build robust and holistic vulnerability management solutions that protect their computing network.
Enterprises discover vulnerabilities that let attackers gain access to their computing network, giving birth to daunting IT security concerns. To handle such cybersecurity concerns, several enterprise vulnerability management tools can assist with identifying and remediating security weaknesses in the network. Organizations need such tools to secure mobile devices, personal devices, firewalls, operating systems, and applications running on IT assets from cyberattacks.
Securing Your Enterprise Network
Software vulnerabilities need your attention instantly. A proactive enterprise vulnerability program addresses numerous cybersecurity issues every day. It keeps the IT assets patched and updated.
Furthermore, vulnerabilities are not the only security concern when it comes to enterprise cybersecurity. Other issues such as poor change management practices, rogue servers, and blurred network boundaries also raise severe concerns while practicing actual vulnerability management.
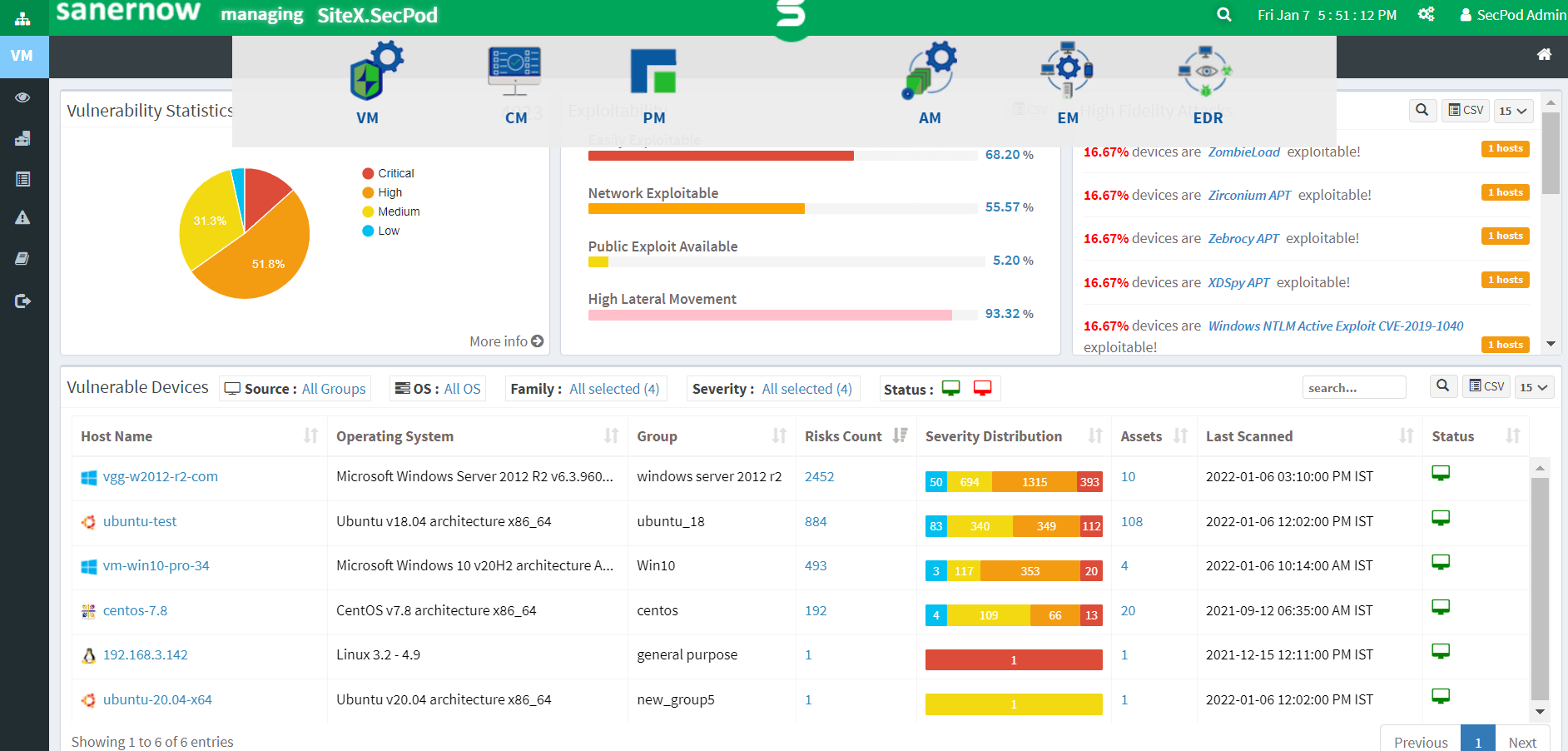
Vulnerability Identification
Scanning for vulnerabilities enables you to identify IT security weaknesses in your computing network and IT assets. It is the primary step toward building a successful enterprise vulnerability management program. If the vulnerabilities remain unidentified, cybercriminals can exploit them. They can also cause cyber threats like denial of service, damage to the whole data, etc. An effective enterprise vulnerability management helps you analyze, track and search for security flaws using tests audits from a single console.
Vulnerability Assessment
Every organization has a different approach and methodology to prioritizing vulnerabilities. However, several tools help run the assessment during less network usage to avoid network disruption. It helps discover the severity of vulnerabilities from the scanned data. The most critical security flaws indicate that the attacks are likely to happen, making an IT security team remediate/mitigate them instantly. Although such assessments can be time-consuming, they save enterprises from a significant security breaches. In general, the assessment and prioritization process help determine the critical risks involved in the network.
Automated Remediation and Reporting
In a large enterprise, the IT security team always looks for ways to fix vulnerabilities faster with fewer resources. It can be achieved using automation techniques, which help you create trigger alters, create tickets, prepare reports and more.
In addition to identifying, assessing, and prioritizing vulnerabilities, the remediation and reporting process helps ensure that all security flaws and necessary remediation steps are executed. If the IT security team decides that remediation is not needed for a particular vulnerability, keeping that data for future reference is essential.
Vulnerability Management for Mobility
Modern enterprises rely on mobile devices to meet their various business objectives in today’s hybrid working culture. In addition, permitting employees’ personal devices, which often connect and disconnect from the corporate network, might pose key security challenges. Most importantly, business organizations have various ways of managing their mobile devices, which are delicate to security software installed.
With Bring Your Own Device (BYOD) deployments, enterprises should include mobile device assessment as part of their vulnerability management program. It should also work in-sync with the existing cybersecurity investments. The main objective is to prevent unauthorized devices from gaining access to the computing network.
Security Intelligence
One of the primary components of enterprise vulnerability management is security intelligence. Gathering data about numerous vulnerabilities that impacted other businesses is a part of a successful vulnerability management strategy. The database of extensive security checks will help enterprises stay ahead of attackers and secure their IT network. The data-driven approach helps reduce the impact or mitigate the risks associated with vulnerabilities. The tools can help you identify assets with the most critical vulnerabilities that need to be patched immediately.
Enable A Resilient and Reliable Vulnerability Management Program for Your Enterprise
Gain control of your computing environment and secure your business assets using an enterprise vulnerability management program. SanerNow, a CyberHygiene platform, can help you achieve that effortlessly.
If your organization is transiting between work from office and hybrid working models, then a successful vulnerability management program is a must. Try your hands on SanerNow’s vulnerability management module. It works well in both cloud and on-premises environments.
Schedule a demo here and learn the best way of managing vulnerabilities.