RYUK is a ransomware that was first spot in the year 2018 and distribute as a part of a targeted campaign. However, The attacks using this ransomware are with well-planning and highly targeted. This ransomware has encrypted a number of PCs, storage, and data centers in various organizations. Therefore, A Vulnerability Management Software can prevent these attacks.
The attackers behind this ransomware have carefully curated the ransomware to target highly sensitive data in large organizations to extort the highest ransom amount possible. Ryuk is considered a high-profile ransomware due to its wide impact on the networks it infects, high ransom demands, and reports of having earned close to 3.7 million dollars. Reports indicate that Ryuk was responsible for 23.9% of the ransomware attacks against enterprises. A good Vulnerability management tool can solve these issues.
Analysis
A careful analysis of the malware reveals the extensive research that the ransomware attackers perform. However, in mapping networks and collecting the credentials of their targets. However, Ryuk has meddled with the functioning of a number of organizations and has created huge losses for them. Ryuk encrypted files are identified by the.RYK extension and the RyukReadMe.html ransom note left behind on infected systems.
It has made close allies with other attackers to muscle in on large businesses. Check Point researchers found close connections of this ransomware with a North Korean group named Lazarus and code similarities with another ransomware called Hermes. Ryuk follows the same encryption procedure as that of Hermes. Ryuk is also known to have rented other malware as an Access-as-a-Service to gain entrance to a network. Ranss leveraged TrickBot and Emotet malware to infiltrate organizations. However, TrickBot and Emotet, which were distributed in large malspam campaigns, create a reverse shell back to the Ryuk attackers giving them remote access to the infected machines to install ransomware.
Ransomware Capabilities
- Deletes shadow volumes and backup files on infected machines.
- Distributes different versions of ransomware for 32 and 64-bit architectures.
- Kills processes and stops services by executing taskkill and net stop on a list of predefined services and process names mostly under the categories of antivirus, database, backup and document editing software.
- Ensures persistence on the target machine by writing itself to the Run registry key.
- Uses specific keywords to look for sensitive files.
- Uses the Wake-on-Lan feature to turn on powered-off devices on a compromised network.
- Blacklists Windows Subsystem for Linux
- Performs thorough network reconnaissance, collects admin passwords, takes over domain controllers, and utilizes post-exploitation toolkits such as PowerShell Empire to spread ransomware.
- Shuts down entire networks after the final infection.
- Steals confidential financial, military, and law enforcement files.
How can Ryuk infect your system?
- Spearphishing emails: Trickbot and Emotet malware are delivering to computers through spam mail, which returns a reverse shell to the Ryuk actors.
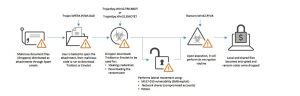 Fig1. Credits: https://success.trendmicro.com
Fig1. Credits: https://success.trendmicro.com
- Publicly accessible Remote Desktop Services on targets.
- Using the Wake-on-Lan feature for lateral movement in the compromised network.
Vulnerabilities Exploited
Ryuk ransomware has finally exploited the following vulnerabilities for infection:
- Network Weathermap HTML Injection Vulnerability (CVE-2013-2618 )
- Zyxel EMG2926 home router OS Command Injection Vulnerability (CVE-2017-6884)
- Internet Explorer Remote Code Execution Vulnerability (CVE-2018-8389)
Attackers can trick users into opening malicious links using vulnerable Internet Explorer to exploit the underlying vulnerability and deliver malware. - Adobe Acrobat and Reader Arbitrary Code Execution Vulnerability (CVE-2018-12808)
Malicious PDF files are transporting to target systems through spear phishing emails. These documents exploit the vulnerability in Adobe Acrobat and Reader to deliver malware.
SanerNow lists the potential targets for malware in an enterprise network(shown in the figures below).
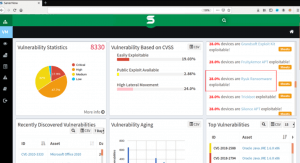
Fig2. SanerNow listing of potential targets in an organization for Ryuk Ransomware
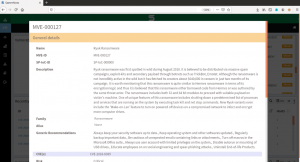
Fig3. Details about Ryuk Ransomware
SanerNow detects and mitigates the vulnerabilities which could be used as infection vectors for spreading Ryuk ransomware. Therefore, Download SanerNow and keep your systems updated and secure.
General recommendations to prevent ransomware infections
- Keep your systems up-to-date with the latest patches available from vendors.
- Maintain an active backup of the files on your machines.
- Refrain from opening any suspicious emails or links.
- Allow Remote Desktop connections through a Windows Firewall and finally make it only accessible through a VPN.

Pingback: 5 Critical Tips That Can Help You Prevent a Ransomware Infection | Cloudavize