In a world where cyberattacks are evolving faster than humans are able to detect and respond to threats, dealing with these attacks and finding effective tools to do so is crucial. Vulnerability management tools that help us safeguard our IT infrastructure are a necessity. Imagine you have hurt your hand badly, and you just let it be instead of treating it, thereby being vulnerable. The same goes for the digital realm. Once you are vulnerable, it’s just a matter of when the attack will happen. Vulnerability management and Exposure management are two very different approaches and concepts. In this blog, we will learn what exposure management is and, most importantly, the top exposure management solutions in the market!
What is Exposure in Cybersecurity?
Exposure in cybersecurity is the state of being vulnerable to cyberattacks due to vulnerabilities or weaknesses in an organization’s IT infrastructure. Once a vulnerability is exposed, the chances of getting attacked increase significantly. Essentially, exposure represents the risk posed by visible or accessible vulnerabilities, instantly increasing the likelihood of exploitation by cyber-attackers.
Vulnerability vs Exposure
Think of vulnerability as a weakness in a system’s defenses. It’s like having a hole in the wall of your house; if someone finds it, they can easily get in. In cybersecurity, vulnerabilities are software or hardware weaknesses that attackers could exploit to gain unauthorized access or cause damage.
Exposure is like leaving vulnerabilities in the open where malicious attackers can see them. In cybersecurity, exposure refers to the state of being susceptible to a potential threat due to a vulnerability. It’s when a vulnerability is visible or accessible to attackers, increasing the likelihood of it being exploited.
So, in simple terms, vulnerability is the weakness itself, like the hole in the wall, while exposure is the risk that comes from that weakness. It’s like when a thief walks past your house and sees a hole in your wall, he will steal something.
Top Exposure Management Solutions
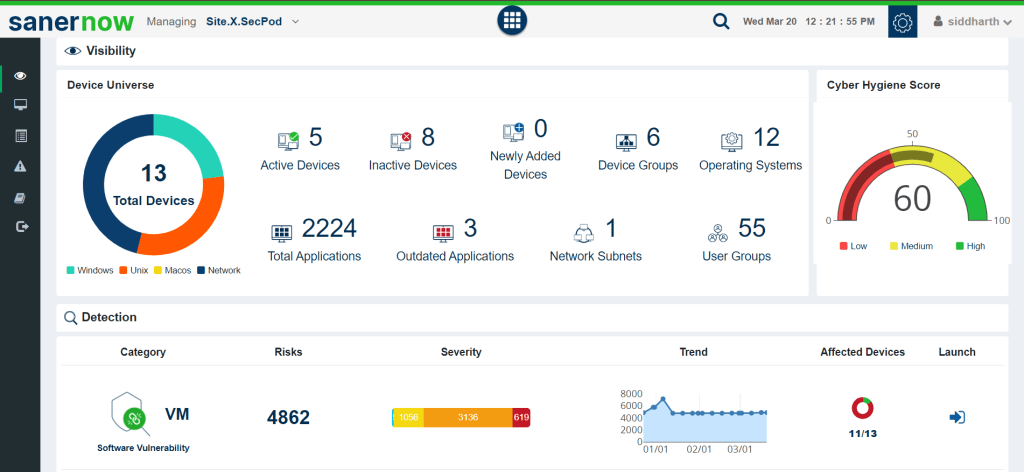
SanerNow Continuous Vulnerability and Exposure Management
- SanerNow CVEM stands for Continuous Vulnerability and Exposure Management.
- With CVEM, you can identify, detect, prioritize, and remediate IT asset exposures, vulnerabilities, missing patches, misconfigurations, deviations in security controls, and security posture anomalies and comply with regulatory compliance benchmarks, all with a single integrated unified platform.
- SanerNow has the world’s largest built-in vulnerability database, with 190,000+ software vulnerability checks. It also performs the industry’s fastest vulnerability scanning to detect vulnerabilities in less than 5 minutes.
- Moreover, SanerNow’s automated and integrated patch management supports all major operating systems like Windows, macOS, Linux, and 450+ third-party applications.
- It is also very user-friendly and easy to use.
- With its Unified dashboard, users can easily know what’s happening in their organization on one screen.
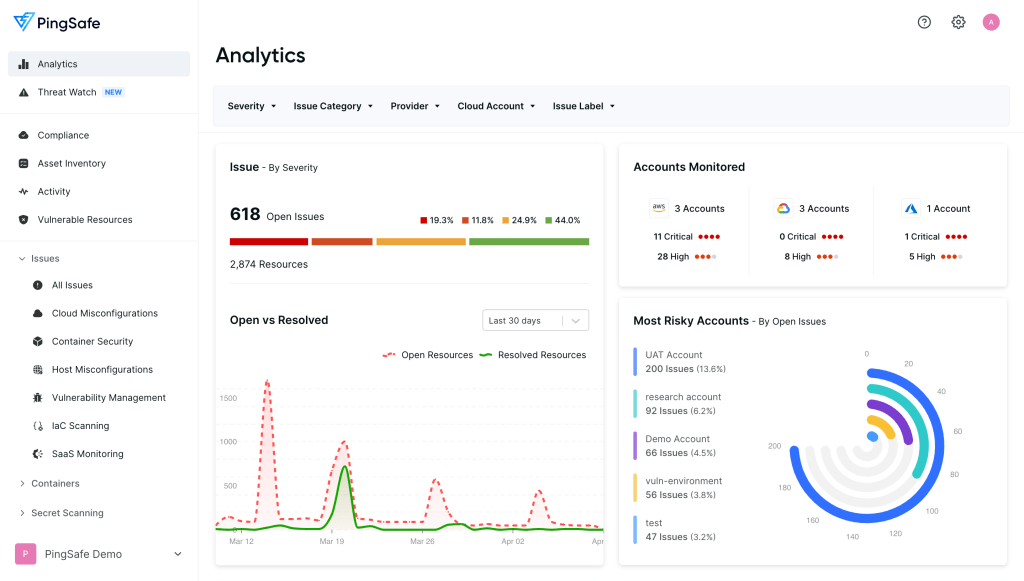
PingSafe
- PingSafe’s exposure management tool is a comprehensive platform that focuses on detecting publicly accessible assets, analyzing their relationships with other resources in the network, and identifying potential attack paths.
- This tool provides insights into possible security breaches, enables proactive measures to prevent actual breaches, and offers evidence-based reports on potential issues for faster vulnerability identification and prioritization of security measures.
- However, the cost is high compared to other platforms in this segment.
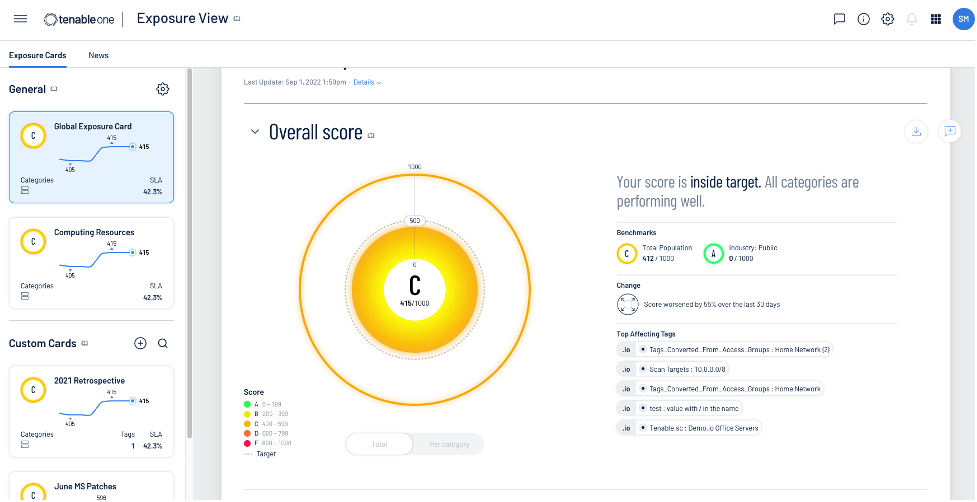
Tenable One Exposure Management Platform
- Tenable One Exposure Management Platform is designed to help organizations gain visibility across the modern attack surface, focus efforts to prevent likely attacks, and accurately communicate cyber risk to support optimal business performance.
- It combines risk-based vulnerability management, web application security, cloud security, and identity security to comprehensively view all assets and associated vulnerabilities, whether on-premises or in the cloud.
- However, some limitations in the dashboard features do not always convey the exact information or trend you want to know.
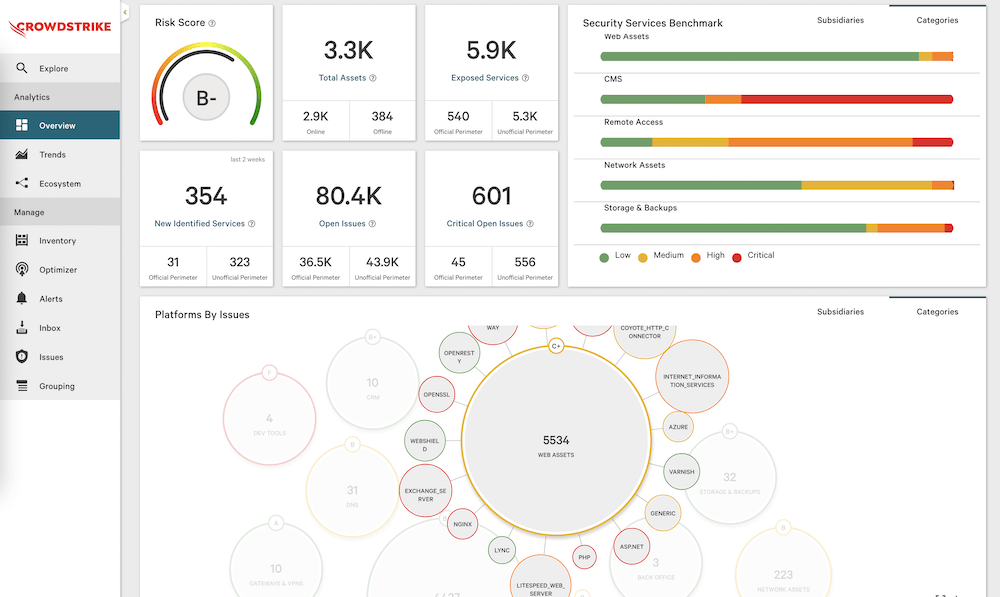
Crowd Strike Falcon Exposure Management
- CrowdStrike Falcon Exposure Management provides organizations with insights into potential security breaches, facilitating proactive measures to prevent actual breaches.
- It offers graph-based visualizations to help organizations understand potential attack paths within their infrastructure, enabling them to prioritize alerts based on business needs effectively.
- However, users must undergo extensive training on this platform to utilize and be thoroughly familiar with it.
Conclusion
Exposure management emerges as a crucial component in mitigating cyber risks. Organizations can enhance their security posture and safeguard against potential threats by understanding and addressing vulnerabilities while minimizing exposure. Leveraging advanced exposure management tools empowers organizations to act effectively, thereby fortifying their defenses against cyber threats.