Business demands are driving a surge of enterprise endpoints. The average IT asset inventory is constantly growing with remote and heterogeneous devices used by multiple employees. While businesses take longer strides and step into bigger opportunities, it is essential to secure and enhance endpoint visibility and control of organizations to keep the business running by using a vulnerability management software.
According to a study, 30 percent of IT admins do not have a firm grasp of the number of endpoints in their companies, despite concerns about cyber threats to endpoints. Constantly changing IT environments and remote work norms complicate the task of discovering, securing, maintaining, and enhancing endpoint visibility and control. Failure to keep an eye on all devices in a network may turn into disastrous, unforeseen cyber-attacks. However, a patch management software can be of help.
Some basic measures are essential to ensure available endpoints in your network are discovered, continuously monitored, and secured from threats.
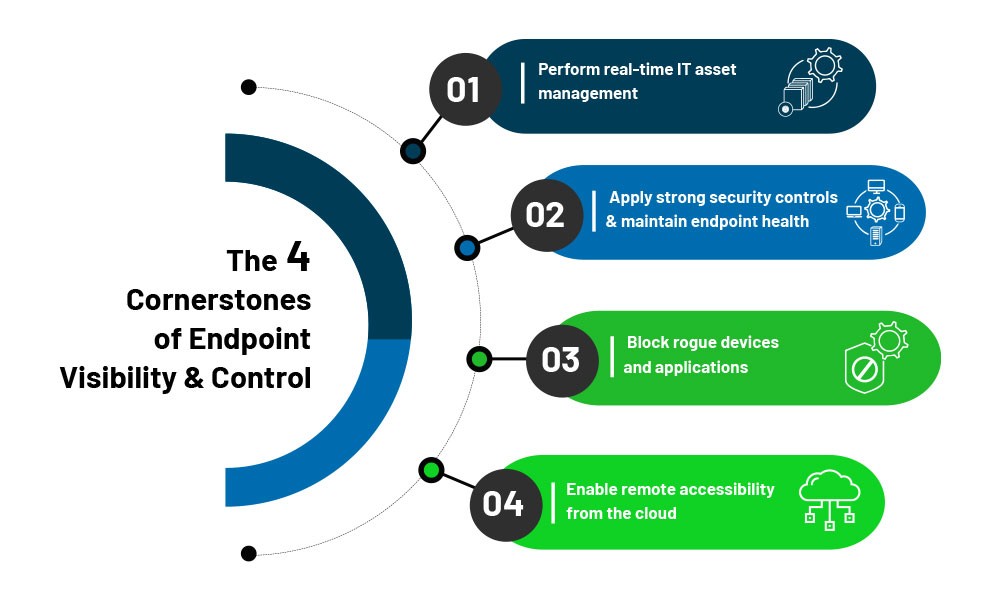
Here are the four cornerstones of endpoints to enhance endpoint visibility and control :
1. Perform real-time IT asset management
Gaining complete visibility over your IT asset inventory is crucial for security and monitoring productivity. It is equally important to run continuous scans on all your endpoints and detect all available software and hardware in your network. Monitor important metrics such as the number of hardware and software, devices installed, and outdated and rarely–used applications. Maintain a constantly updated and monitored IT asset inventory.
2. Apply strong security controls and maintain endpoint health
Numerous activities happen at an endpoint every day. Therefore, it is crucial to monitor all of it to detect suspicious activities. Continuously track and monitor all your endpoints with stringent and regular security checks. Check the health of endpoints regularly, enable stringent firewall policies, quarantine or isolate unnecessary devices, kill rogue processes and services, harden system configurations, and perform remote system tune-ups and disk clean-ups to safeguard your endpoints
3. Block rogue devices and applications
While Allowing usage of any random device or application in the network will gouge a hole in IT security and employee productivity. It is pivotal to disable or block rogue and unauthorized devices and applications entering your network. Implement a strong application and device control strategy to safeguard your network from malicious activities.
4. Enable remote accessibility from the cloud
When you want to actively monitor all endpoints, you need to execute security tasks remotely without relying on physical access to devices. Moving your visibility and control measures completely to the cloud has its benefits. You can execute control across your remote devices effectively, without worrying about connectivity and maintenance issues.
SanerNow Visibility and Control is a fully integrated cloud-based solution to establish comprehensive visibility and control over your heterogeneous enterprise endpoints and secure them from cyber threats.
Sign up for a free personalized demo. We’ll show you how SanerNow can help you secure your endpoints wherever they are.