Exim is the most used MX server with more than 57% of installations on mail servers reachable on the Internet. Exim has released an urgent security update today. The vendor had released an early security warning to install the updates immediately after release. The vulnerability is tracked as CVE-2019-16928 and classified as heap-based buffer overflow (CWE-122) using a vulnerability scanning tool.
The flaw exists in ‘string_vformat’ in file string.c‘. Heap based buffer overflow allows attackers to potentially execute arbitrary code or crash the application. The bug is essentially a simple coding error where the length of the EHLO string taken into consideration and corrected with a one line fix handling the length of string sent to the buffer. A patch management tool can patch this bug.
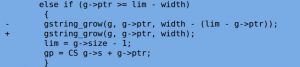
fig. fixed patch for vulnerability
Proof of Concept
A Proof of Concept published by Jeremy Harris of Exim Development Team. While this exploit uses a specially crafted EHLO string to only crash the Exim process, there could be other commands to execute arbitrary code. However, an unauthenticated remote attacker can cause denial of service by sending an extended EHLO string with large amounts of data.
A month ago, Exim mail server patched for a critical remote code execution vulnerability (CVE-2019-15846) which allowed a remote unauthenticated attacker to execute programs with root privileges. In July, Exim patched for another critical remote command execution vulnerability (CVE-2019-10149) which actively exploited in the wild. Get detailed information about these vulnerabilities in our blogs on CVE-2019-15846 and CVE-2019-10149. We request system administrators to install the latest updates for Exim Mail Server as soon as possible.
Affected Products by heap based buffer overflow:
Exim Mail Server versions 4.92 through 4.92.2.
Impact:
An attacker can execute arbitrary code or cause a denial of service.
Solution to heap based buffer overflow:
Also, please refer to this KB Article, which now replaced by KB Article, to apply the patches using SanerNow.

