Highly evasive hackers breached Orion IT monitoring and management software of SolarWinds and deployed malware updates to it. It is known as solarwinds sunburst. As a result, attackers have gained access to government, consulting, technology, telecom, and extractive entities in North America, Europe, Asia, and the Middle East. A reliable vulnerability management solution can stop these attacks.
The supply chain attack (a cyberattack that attempts to inflict damage to a company by exploiting vulnerabilities in its supply network) is how the attacker gained access to FireEye’s network, which the company disclosed recently. FireEye termed the malware as SUNBURST, distributed via SolarWinds Orion business software update. FireEye has discovered this global intrusion campaign and tracking attackers behind it as UNC2452. This campaign had started as early as Spring 2020 and is currently ongoing. Although FireEye named this malware SUNBURST, Microsoft has named it as Solorigate and updated Defender antivirus with new detection rules. Auto patching can be used to mitigate vulnerabilities.
SUNBURST Backdoor
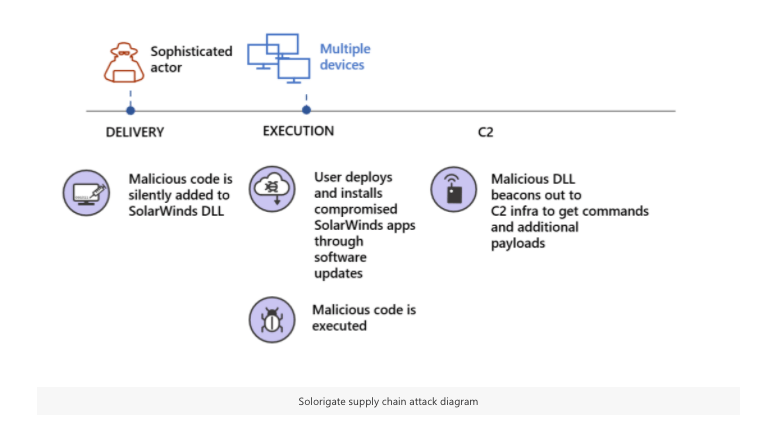
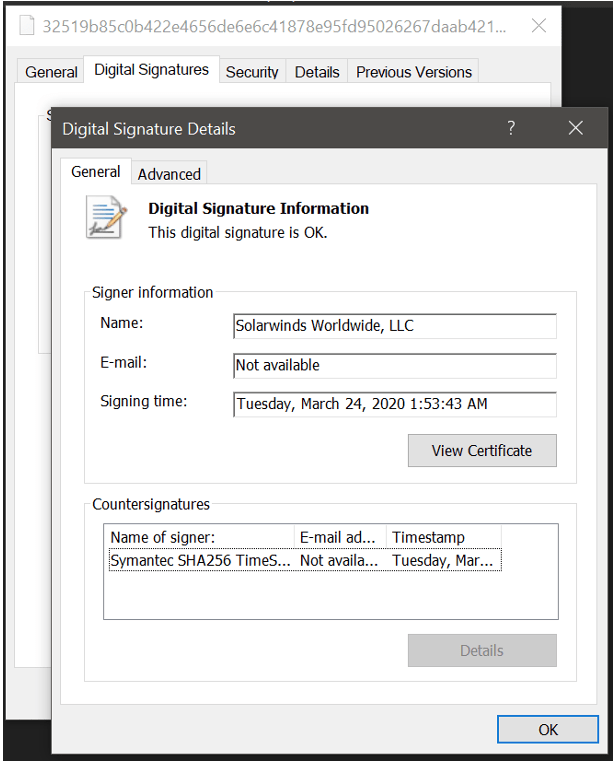
SolarWinds.Orion.Core.BusinessLayer.dll is a SolarWinds digitally-signed library file of the Orion platform known, and it contains the backdoor that communicates to third party servers via HTTP.
Once SUNBURST malware is on victim’s machines, after the inactive period of up to two weeks, it retrieves commands called “Jobs”, which can transfer files, execute files, profile the system, reboot the machine, and disable system services.
The malware is deceptively smart enough to make its network traffic look like the Orion Improvement Program (OIP) protocol and stores initially examined results within trusted plugin configuration files allowing it to blend in with legitimate SolarWinds activity. Moreover, the malware identifies forensic and anti-virus tools running as processes, services, and drivers using multiple obfuscated blocklists.
Image: SolarWinds digital signature on software with a backdoor
Multiple digitally-signed updates infected with the malware were posted on the SolarWinds update website since March-2020. The update file is a standard Windows Installer Patch file that includes the affected SolarWinds.Orion.Core.BusinessLayer.dll component. After the update, SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe loads the malicious DLL.
In solarwinds sunburst, after two weeks, the malware attempts to resolve a subdomain of avsvmcloud[.]com, and the DNS response returns a CNAME record that points to a Command and Control (C2) domain. However, the C2 traffic to the malicious domains is deceptive enough to look like communications between SolarWinds APIs. Finally, the list of known malicious infrastructure is available on FireEye’s GitHub page.
Affected Products by solarwinds sunburst
Orion Platform versions 2019.4 HF 5 and then 2020.2 with no hotfix or with 2020.2 HF 1, including:
Application Centric Monitor (ACM)
Database Performance Analyzer Integration Module (DPAIM)
Enterprise Operations Console (EOC)
High Availability (HA)
IP Address Manager (IPAM)
Log Analyzer (LA)
Network Automation Manager (NAM)
Network Configuration Manager (NCM)
Network Operations Manager (NOM)
Network Performance Monitor (NPM)
NetFlow Traffic Analyzer (NTA)
Server & Application Monitor (SAM)
Server Configuration Monitor (SCM)
Storage Resource Monitor (SCM)
User Device Tracker (UDT)
Virtualization Manager (VMAN)
VoIP & Network Quality Manager (VNQM)
Web Performance Monitor (WPM)
Solution
However, SolarWinds stated that it is going to release a new update (2020.2.1 HF 2) on December 15 that “replaces the compromised component and provides several additional security enhancements.”


