Cerber is pernicious ransomware and one of the top 3 ransomware in the world. Cerber has been growing exponentially since early march of 2016. The notorious ransomware is now in its 5th version as the developers of the ransomware have been continuously improving their code to avoid endpoint security counter-measure.
So far we have seen five major versions of Cerber which include Cerber, Cerber2.0, Cerber3.0, Cerber4.0, and the latest Cerber5.0. Cerber 4.0 had many variants, some of the major ones include Cerber 4.1.0 – 4.1.6.
Here we will go through each Cerber version’s behavior.
Threat indicators – Indicator of Compromise:
Cerber1.0: The first version of Cerber once it’s executed on victim’s machine, uses very complicated encryption with RSA-2048 and AES-256 (Advanced Encryption Standard). Once it’s executed it first checks for the country where the victim machine is residing. If the country found to be, is one among from the below list then this version of the Cerber will not encrypt the files. It does no harm at all.
Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Russia, Turkmenistan, Tajikistan, Ukraine, Uzbekistan.
If the computer is not from the above list, Cerber will install itself into %AppData% folder with a random .exe file. Upon execution, Cerber will encrypt user files and documents with strong encryption algorithms which make them ‘unreadable’. After the encryption process finishes it attaches the .cerber extension to all the encrypted files.
By executing the below command, Cerber will cause loss of all the backup copy of local files.
C:\Windows\System32\wbem\WMIC.exe shadowcopy delete
Cerber’s Registry Entries:
Adds an entry of its extension – Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.cerber
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random.exe "%AppData%\{ransom}\[random].exe"
There are 3 files which contain information on how to decrypt the encrypted files. The ransom notes will be dropped in each folder where the encryption has taken place. These files are named as # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, # DECRYPT MY FILES #.vbs.
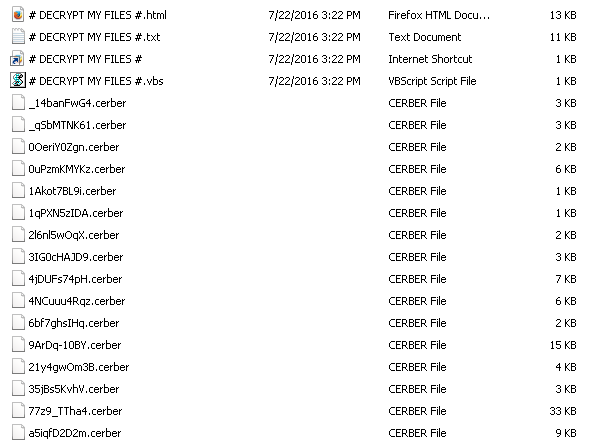
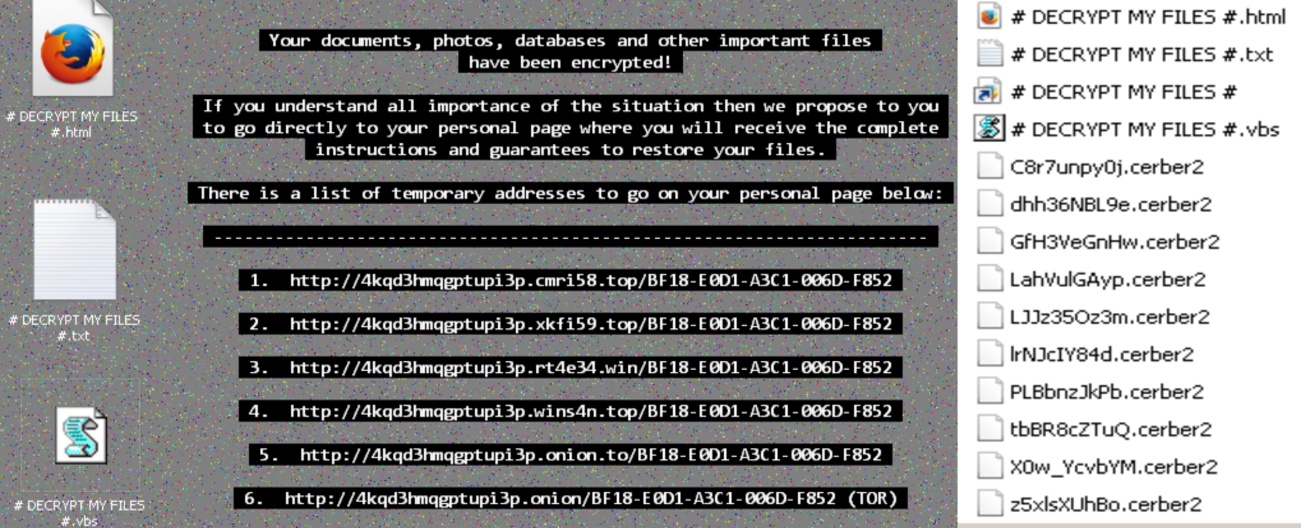
The # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt contains ransom notes on how to decrypt the encrypted files, and payment information, whereas # DECRYPT MY FILES #.vbs # file has a VBscript which will trigger an audio file speaking about ransom note. Here the attackers are asking ransom bitcoins which is approx 1.24 – 1.25. The victim has to pay ransom using TOR browser by visiting any one of the given 5 temporary addresses and follow the payment instructions. Don’t pay the ransom. Free decryptors are available for decryption.
Cerber2.0: Cerber2.0 is the updated version of Cerber1.0 ransomware. Though the behavior of this ransomware is quite similar to the previous one, it differs in the indicators it leaves behind and some notifiable behavior in its execution. The encryption process is similar to Cerber1.0, but here the attackers have replaced the file extension with .cerber2 for the encrypted files. The newer version presents itself as the wallpaper of the desktop which contains ransom note. Apart from these changes, it remains same as it will drop # DECRYPT MY FILES #.html, # DECRYPT MY FILES #.txt, and # DECRYPT MY FILES #.vbs files.
Like Cerber1.0, this version also executes the below command. It causes the loss of all the backup copy of local files.
C:\Windows\System32\wbem\WMIC.exe shadowcopy delete
Registry Entries:
Adds an entry of its extension -Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts.cerber2
HKCU\Software\Microsoft\Windows\CurrentVersion\Run[random.exe "%AppData%{ransom}[random].exe"
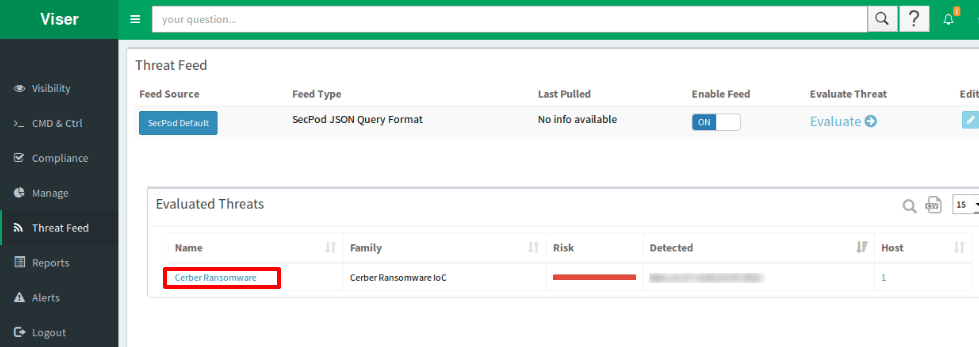
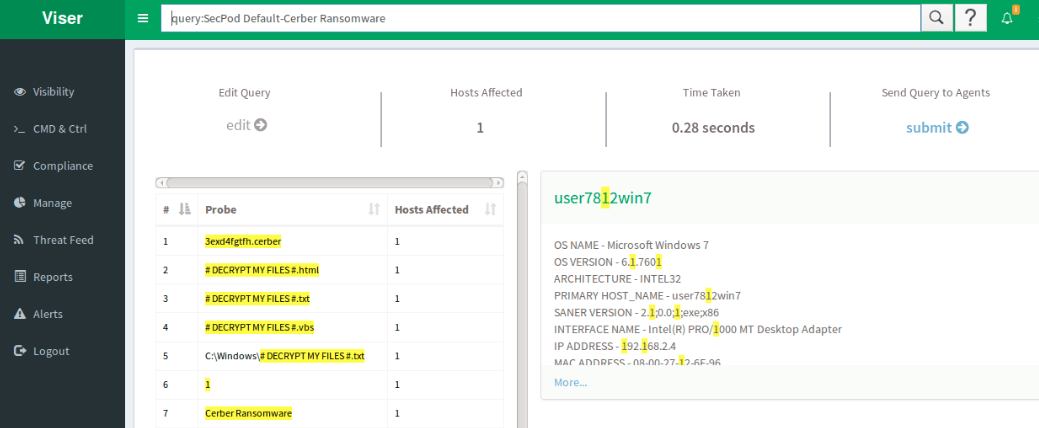
Saner in Action:
The snapshots below shows how Saner detects Cerber ransomware in real-time.
Cerber indicators can be seen in the screenshot below.
Saner catches Cerber encryption in real-time. We’re always on the hunt for new threats. Be careful about opening skeptical items on the internet as much as possible. Do not open suspicious spam emails which includes attachments. Avoid running into such malicious software in the future. Recognize Cerber malware alerts and trust Saner updates.
Click here for more technical info on further versions of Cerber Ransomware.
– Kashinath T (Security Research Engineer)