PHP FPM (FastCGI Process Manager) is an advanced PHP FastCGI implementation with added features and is very useful for heavily loaded sites. A PHP FPM vulnerability, CVE-2019-11043, was discovered and exploited in the wild. A good Vulnerability Management tool is the solution to this problem.
NGINX servers with PHP-FPM are vulnerable. The vulnerability tracking is CVE-2019-11043 and is classified as buffer underflow (CWE-124). A buffer underflow vulnerability is where the pointer directs to a location before the referenced buffer. This can be of use to an attacker to leak sensitive information or execute arbitrary code. However, these vulnerabilities will be insignificant if you have a good vulnerability management software.
In this case, the flaw exists in env_path_info in file sapi/fpm/fpm/fpm_main.c, which contains certain pointer arithmetic that assumes it points correctly to the php_script. The absence of verification of a path or file’s existence leads to storing an incorrect pointer value in the ‘path_info‘ variable.
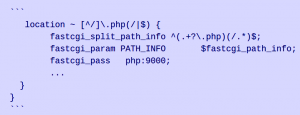 fig. Example of nginx configuration
fig. Example of nginx configuration
NGINX Configuration:
The advisory explains that if the nginx configuration looks as above, a crafted URL with a newline character can break the regex in the ‘fastcgi_split_path_info’ directive, leading to code execution. This type of configuration is not uncommon. The value of path_info[0] is set to zero going further in the code; FCGI_PUTENV is then called. However, an attacker can use a crafted URL with a carefully chosen length of the URL path and query string to modify path_info to point to the first byte of the _fcgi_data_seg structure. When zeros are present to this, the pointer char* pos moves backward, and FCGI_PUTENV overwrites some fast CGI variables and other data with the new script path. A set of config values with a fake PHP_VALUE fcgi variable can be of use for remote code execution.
Emil Lerner first reported the vulnerability to the vendor in September 2019. Omar Ganiev, a security researcher, tweeted about the vulnerability in PHP-FPM and also published a PoC.
 fig.PoC for Remote Code Execution
fig.PoC for Remote Code Execution
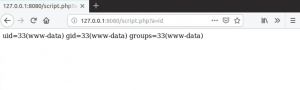 fig. exploitation of remote code execution
fig. exploitation of remote code execution
A certain set of pre-conditions are to be present for the server to be vulnerable by CVE-2019-11043:
- Location directive in nginx forwards requests to php-fpm
fastcgi_split_path_infomust be present and must contain a regex that starts with ‘^’ and ends with ‘$’.- fastcgi_param must have a value using the variable
PATH_INFO - file existence checks like
try_files $uri =404orif (-f $uri)must not be present.
Affected Products
PHP versions 7.1.x below 7.1.33, 7.2.x below 7.2.24, and 7.3.x below 7.3.11 are vulnerable.
Impact
An attacker can exploit the vulnerability to execute code remotely.
Solution
The vendor has fixed this vulnerability with the release of PHP 7.3.11 (current stable) and PHP 7.2.24 (old stable). Therefore, For those using Nginx with PHP-FPM, we urge users to update their machines with the installation of the latest patches.

