Software patching is one of the primary security measures to prevent cyber-attacks. Many organizations realize the importance of patching, but the challenge starts when carrying-out patching as a routine activity. With multiple operating systems and software, ever-expanding networks, and an improper strategy, many organizations struggle to patch their software at the earliest and secure their endpoints. A reliable set of best practices for patch management with a patch management software ensures a better patching strategy and a lower attack surface.
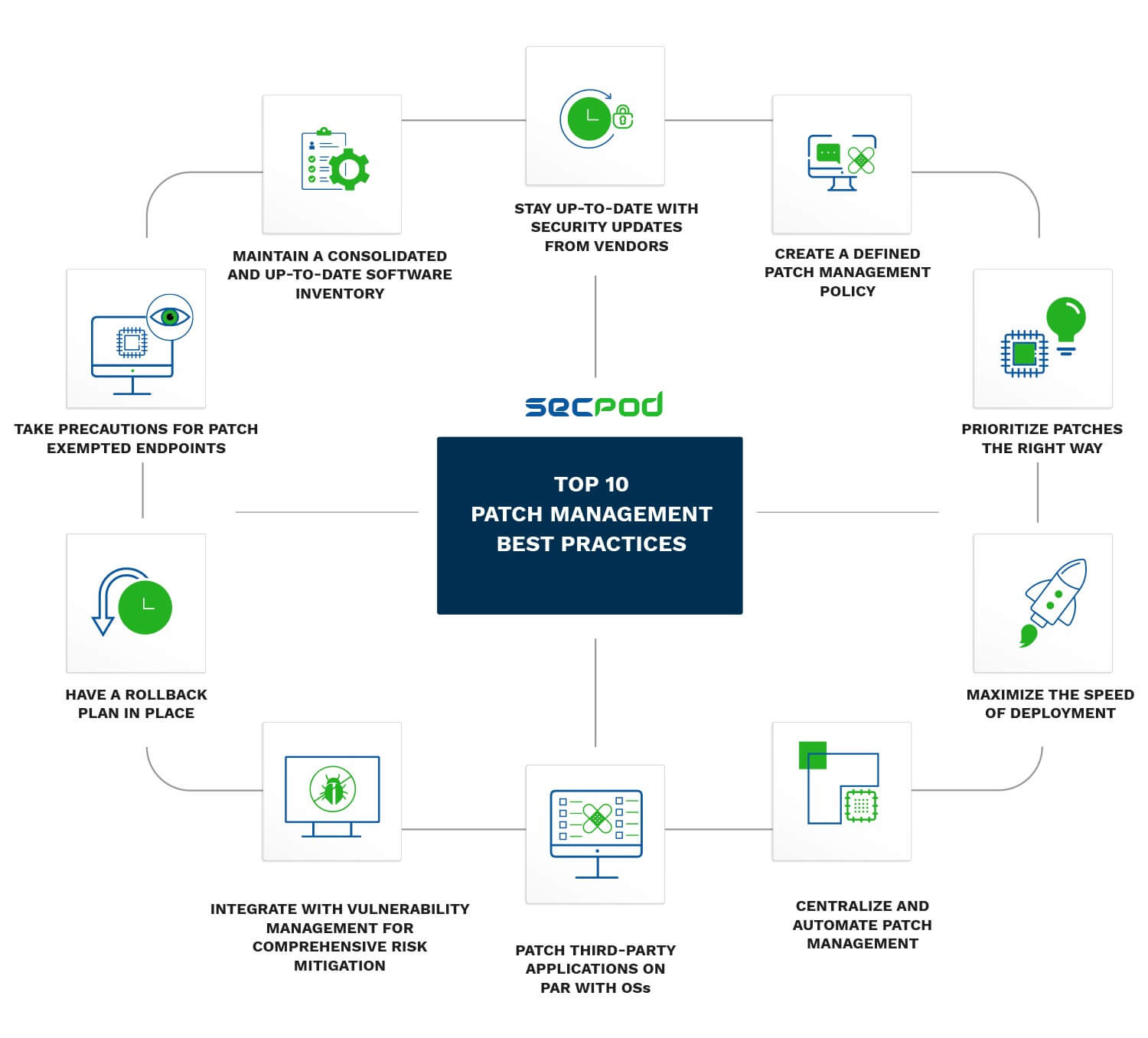
1. Maintain a Consolidated and Up-to-Date Software Inventory
Create a database of all IT assets in your inventory. Keep them organized according to device type, operating system, version of the operating system, third-party applications, and hardware. An up-to-date inventory is crucial to assess the true security posture of your organization. You cannot risk missing out on vulnerabilities because a device or software was not visible in your assets.
Many organizations end up using multiple versions of the same software. Multiple software versions complicate patching tasks and asset management. Consolidate software versions whenever possible. Keep one newest version of the software and discard the rest. This is easily automated with a patch management tool.
Monitor application usage across all endpoints. If an application is rarely used/not used, deprovision it to keep your application portfolio cost-efficient, lean, and up-to-date. A clean and accounted asset inventory makes patch discovery easier.
2. Stay Up-to-Date with Security Updates from Vendors
Security researchers in vendor companies regularly evaluate their software, discover vulnerabilities, and provide patch fixes to remediate the vulnerabilities. The availability of these patches is intimated to users in security update emails from the respective vendors. Subscribe to security emails from all known vendors in your application portfolio.
The widely known security update is Microsoft Patch Tuesday. It is a monthly routine where Microsoft releases patches for all Microsoft software products, including Windows and third-party apps. Make sure not to miss out on any security updates from your software vendors. Critical fixes might be made available to remediate an actively exploited vulnerability.
3. Create a Defined Patch Management Policy
Deploying all patches one-by-one in no specific order is not the smartest approach to go about. Create a patch policy that is specifically designed for your IT environment.
a) Define a scanning schedule
Scan all endpoints to discover missing patches in your software. You can schedule a weekly or monthly scan based on your requirements. The time for scanning might range from less than 5 minutes, up to several hours depending on your scanning tool.
The best scanning schedule, however, is continuous scanning offered by a few advanced patching tools. Agents installed in endpoints immediately discover a missing patch and notify you. A remediation plan can be swiftly rolled out if the patch is critical.
b) Categorize and segregate
Categorize the patches based on users/groups, devices, applications, and OS type. Once patches are categorized, planning the deployment job is easier. Patches can be tracked and verified without missing out on any devices. Identify and segregate security patches from non-security patches.
c) Prioritize and deploy
Prioritize critical security patches over non-security patches. Create a patch job containing the deployment time and reboot schedule. If required, assign technicians to specific jobs or groups of devices for faster deployment and increased efficiency.
4. Prioritize Patches the Right Way
Vulnerabilities in the same severity level do not necessarily pose the same level of risk. Severity ratings and CVSS (common vulnerability scoring system) scores give you a rough idea of the risk, but it’s not the whole picture.
Assessing the true risk of a vulnerability involves a lot of factors:
- Ease of exploiting the vulnerability (technical implications)
- Active exploitation of the vulnerability right now
- Number of days the vulnerability has remained unpatched (more days = higher risk)
- Number of devices reported with the vulnerability and the impact on business in case of a potential exploit
Publicly available information can only give you so much information. Manual risk assessment takes a lot of time and effort. The accuracy and smartness of your patching tool are crucial to finding the true risk to your organization’s attack surface fast enough.
5. Maximize the Speed of Deployment
According to a survey, there has been a 24% increase in annual spending on prevention, detection, and remediation in 2019 compared to 2018. Yet, the average time to deploy a critical patch remains at 12 days due to data silos and poor organizational coordination.
The speed of deployment is now more crucial than ever. According to the National Vulnerability Database (NVD) curated by NIST, a new record is set for the highest number of disclosed vulnerabilities each year. With the increasing rate of disclosed vulnerabilities, there are more doors open to threats each day. Remediating vulnerabilities fast is the best way to ensure that you stay on top of vulnerabilities and secure all possible gateways to your business.
A faster patch deployment can be achieved by improved skills, faster patch scanning and discovery, and automatic downloads and deployment. Faster deployment ensures there are fewer patches for you to assess and prioritize in each cycle. Your definition of ‘regular patching’ should keep climbing up the ladder of speed and accuracy.
6. Centralize and Automate Patch Management
In a survey of IT professionals, 88 percent of respondents say their team is not fully responsible for patching vulnerabilities and they have to coordinate with other teams. Multiple patching tools create data silos and lead to poor coordination and disintegrated efforts.
A smart decision is to centralize patch management with a comprehensive patching tool that supports all operating systems and third-party apps. This way, data silos are avoided, and all risk assessment and patching tasks are performed using one tool.
In the same survey, most respondents voted automation as the best step to improve their organization’s patch management. With increasing challenges such as inadequate staffing and skills, longer deployment cycles, manual risk assessment, and continuously expanding networks, automation might be the next logical step for your patching strategy. Automation allows you to document, execute, and analyze patching as an established process in your organization.
7. Patch Third-party Applications on Par with OSs
In 2019, browsers were the most actively exploited applications, with six publicly disclosed zero-days. Flash players and document readers are also very commonly exploited applications. In fact, Adobe released patches for more than 400 CVEs (common vulnerabilities and exposures) in 2019. That is half the amount of patches released for Microsoft products over the entire year.
Add third-party patching to your Patch Tuesday routine and perform truly complete risk mitigation. If you can, include firmware updates to your patching routine and complete the entire circle of your patch management program.
8. Integrate with Vulnerability Management for Comprehensive Risk mitigation
The primary need for software patching is remediating vulnerabilities. So it’s acceptable to say that patch management belongs in the subset of vulnerability management. Vulnerability management is more than just patching. It involves a comprehensive and continuous risk assessment program that detects vulnerabilities in the form of open ports, faulty system configurations, registry settings, and more.
A vulnerability database such as the SCAP feed contains thousands of publicly disclosed vulnerabilities. A vulnerability scanner detects all types of vulnerabilities in endpoints. By patching or remotely changing system settings, the vulnerabilities are mitigated.
An integrated vulnerability and patch management tool gives you a standardized risk mitigation process that scales along with your growing enterprise endpoints. However, IT teams can easily adopt a single tool to carry out vulnerability management and patching hand-in-hand.
9. Have a Rollback Plan in Place
Sometimes, a patch even though tested and verified, may prove incompatible on some devices resulting in downtime. To avoid downtime caused by incompatible patches, a rollback plan is necessary to remove the patch and restore the software to the previous stable version. You can also develop a plan to run and execute commands to roll back the patches from endpoints.
Some patching tools have a rollback feature built into them. Admins can simply roll back the patch remotely with a single click and then restore the functionality of the device or application.
10. Take Precautions for Patch Exempted Endpoints
Sometimes, patches may fail to deploy due to many reasons like the unavailability of vendor servers or misconfigurations in endpoints. Troubleshoot failed patches, try to figure out the root cause, and deploy the patch.
If the patch is still not deployed, you have to take other measures to ensure a potential threat actor doesn’t discover and exploit the vulnerability. Truncate the app from the network and make sure it’s not open to exploits. You can:
- Whitelist the app and run only allowed executable files
- Restrict user/group permissions to the app
- Cut off internet access to the application
The importance of patching enterprise software is rising exponentially. More vulnerabilities and patches are revealed every year, further complicating patch management for IT admins. Follow these best practices to have a smooth patch management process and minimize your organization’s risk exposure.
SanerNow Patch Management is a cloud-based, fully-automated patching tool that supports all operating systems (Windows, Mac, Linux), a wide range of third-party apps, and firmware. You can see these best practices in action and implement them right away in your security stack.
Register for a free demo, and we’ll show you how you can take patch management to the next level.


One of the most important things to keep in mind is patch management should not just be performed when you remember, or when you hear a critical security issue has come up.
That’s right, Sam. Patching is a basic IT security process commonly overlooked by organizations.
If you move workloads to cloud you’ll have less to patch. At the same cloud is more expensive usually
Absolutely true Alex! However, cloud doesn’t always have to be expensive. Check out SanerNow Patch Management if you haven’t yet. You’re in for a surprise.