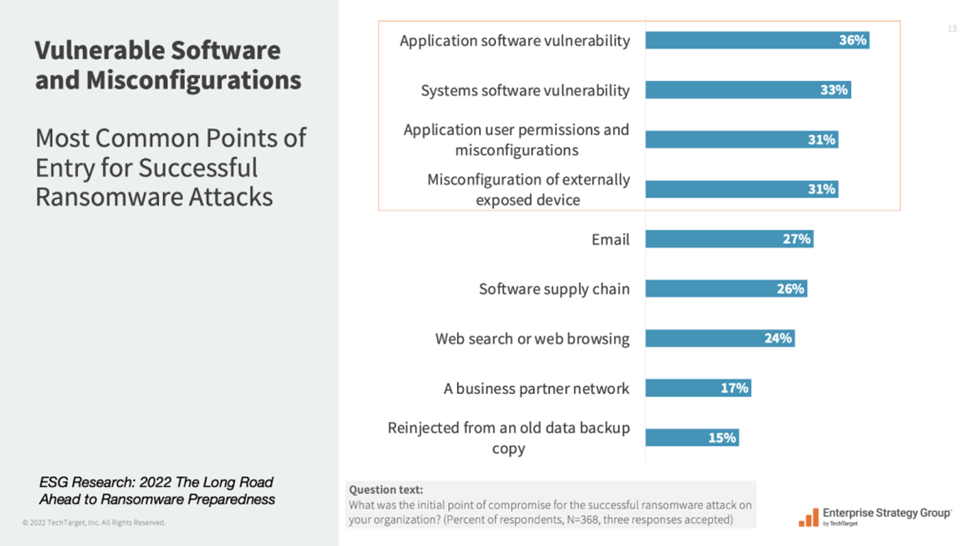
The biggest reason for cyberattacks has been vulnerabilities. However, the trend has slowly changed, with threat actors using different methods and security risks to enter your network. Research suggests that 31% of cyberattacks were due to security risks such as misconfigurations, posture anomalies, and asset exposures being exploited, and alarm bells are ringing everywhere on how to mitigate these risks. Traditional vulnerability management tools were struggling to keep up.
So, are patches alone enough to mitigate these risks? Let’s find out!
Patching vs. Mitigation: The Difference
Simply put, patching is the process of application of a patch. It can either be to fix a risk or as a feature update. Patches are typically vendor-developed, which means they eventually become outdated.
Mitigation, on the other hand, is the process of eradicating risk. It includes patching and other means of risk remediation. Examples could be workarounds, security controls, isolation, or even physical replacement of assets.
So, have you been patching or mitigating?
Why is Patching Not Enough?
Patching takes up a significant chunk of the mitigation process but not all of it. While patching has significant advantages, there are still some major limitations to it. Let’s take a look at them.
- Vulnerability without a patch:
Often, new software is developed and released, but vulnerabilities are detected in them. Sometimes, the detected vulnerability is not critical enough to raise alarms for an immediate patch. As patches take time to develop, sometimes they are put on hold, leading to an open loophole in your systems that a threat actor can exploit. And all you can do is wait for the developers to patch. - End-of-life software risks:
Outdated or end-of-life software is another main reason why patching is not enough to mitigate security risks. A significant portion of endpoint devices in a network can have outdated software with dangerous critical vulnerabilities that will never get a patch. Since waiting for patches is futile, the risks can go unchecked without other mitigation methods. - Zero-day Vulnerabilities:
The software applications can have undiscovered vulnerabilities that don’t have a patch that hackers can take advantage of. Additionally, most Software apps usually get patches, but sometimes fixing something can break something else! New patches can bring in undiscovered vulnerabilities without any fixes. These Zero-day vulnerabilities can be devastating if other mitigation methods instead of patches are not used to mitigate them.
What is the Solution? Remediation beyond Patching
We know that patching is not enough. So, how do we mitigate risks effectively? As previously mentioned, workarounds, security controls, and isolation are some methods of mitigating risks when patching doesn’t work. Among them, security controls are the most critical method of mitigation beyond patching. Let’s understand how it helps mitigate risks that don’t have a patch.
Cloud Email Security:
Another important mitigation solution involves incorporating cloud email security into your environment. This method ensures the protection of an organization’s email ecosystem against advanced threats and targeted attacks that patches might not address immediately or effectively. These solutions leverage multiple layers of protection, including threat intelligence, advanced filtering, and encryption, to secure email communication.
By implementing such cloud-based security measures, businesses can enhance their overall security posture, reducing the vulnerability to exploits and attacks that prey on unpatched systems or those that cannot be patched promptly. This approach aligns with the mitigation strategies beyond patching, focusing on proactive and comprehensive security controls to protect against a vast array of digital threats. To take your email security one step further, make sure to check DKIM and SPF which authenticates the sender’s identity and message integrity providing an additional layer of protection.
Security Controls:
Arguably, the most important mitigation solution, security controls, are settings and configurations used to protect an organization’s endpoint devices and the data stored as well. These security controls can help you perform a wide variety of functions that include blocking malicious applications, enabling firewall policies, disabling rogue devices or software, etc.
For example, when a particular software has a critical vulnerability without a patch, security controls like blocking malicious applications can instantly negate the potential effects of the security risk and help you isolate the issue.
These security controls, when properly configured, can have a significant impact on your organization’s security posture and help you reduce attack surface and achieve compliance as well.
A critical advantage of proper implementation is that most compliance regulations incorporate it in their regulatory controls.
Read more about Vulnerability Management Controls
Simplified Vulnerability Mitigation with SanerNow
With multiple OSs in a network and 100+ security controls in each of the devices, manual implementation of security controls is a herculean task. Enter SanerNow to your rescue. SanerNow is an advanced vulnerability and exposure management solution that will reduce your attack surface and help prevent cyberattacks.
From patching to mitigation beyond patching, SanerNow can help you achieve and implement effective security controls to rapidly and efficiently reduce the attack surface and mitigate the potential risk originating from security risks without patches.
Learn more about how SanerNow can help you mitigate risks beyond patching
Conclusion
Patching is a critical component of IT security, but the hard truth is that it’s not enough. A significant number of security risks don’t have a patch but still pose a threat to your IT infrastructure.
Security controls beyond patching are the answer to this problem, and proper implementation can be a complete game changer in improving your cybersecurity posture and achieving security compliance for your organization.


