The cURL development team has recently disclosed a high-severity heap buffer overflow vulnerability (CVE-2023-38545), which poses a substantial risk of enabling remote code execution in applications utilizing the impacted iterations of the cURL library.
Note: cURL is a highly popular open-source utility for data transfer in standalone applications and scripts. It comes in various forms, including standalone executables and libraries (static or dynamic), and is often pre-installed on major operating systems, such as Microsoft Windows.
Vulnerability Details
This vulnerability leads to a heap buffer overflow within cURL during the SOCKS5 proxy handshake. When cURL transfers the hostname to the SOCKS5 proxy for address resolution, it enforces a 255-byte limit on the hostname length.Curl switches to local name resolution if the hostname exceeds this limit and transmits only the resolved address to the proxy. However, due to a bug, the local variable controlling the hostname resolution can be present incorrectly during a slow SOCKS5 handshake. Inadvertently the long hostname will copied to the target buffer, instead of just the resolved address due to CVE-2023-38545.
Technical Details
The target buffer is a heap-based download buffer within the libcurl library, employed for SOCKS negotiation before the data transfer commences. This buffer is 16 kilobytes by default, although applications can customize it to different sizes. The curl tool, for instance, defaults to a buffer size of 102,400 bytes but reduces it if the user sets a lower data transfer rate using the –limit-rate option.
libcurl provides the CURLOPT_BUFFERSIZE option, allowing adjustments to the download buffer’s size. It’s worth noting that libcurl accommodates hostnames in URLs up to 65,535 bytes.
When a hostname surpasses the capacity of the target buffer, a memcpy() operation occurs, overwriting the buffer in the heap. If included in the cURL build, the URL parser and potentially an Internationalized Domain Name (IDN) library must accept the hostname. This restriction limits the available byte sequences for copying.
For this overflow to transpire, it necessitates a SOCKS5 handshake to trigger the local variable bug, and the attacker must use a hostname longer than the download buffer. This scenario could arise with a malicious HTTPS server redirecting to a meticulously crafted URL as a result of CVE-2023-38545.
This vulnerability is only conceivable in applications that either do not specify CURLOPT_BUFFERSIZE or set it to a value less than 65,541. As the cURL tool defaults to a 100-kilobyte CURLOPT_BUFFERSIZE, it remains non vulnerable unless the user explicitly configures a lower data transfer rate of fewer than 65,541 bytes/second.
The circumstances that prompt the use of SOCKS5 with a remote hostname in libcurl include the following :
CURLOPT_PROXYTYPEset to typeCURLPROXY_SOCKS5_HOSTNAME, or:CURLOPT_PROXYorCURLOPT_PRE_PROXYset to use the schemesocks5h://- One of the proxy environment variables can be set to use the
socks5h://scheme. For examplehttp_proxy,HTTPS_PROXYorALL_PROXY.
In the case of the cURL tool, SOCKS5 with a remote hostname is invoked when employing the –socks5-hostname option or by setting either –proxy or –preproxy to use the “socks5h://” scheme. The same effect can be achieved by configuring relevant environment variables as described in the libcurl section.
Impact
Successful exploitation of this vulnerability by an unauthenticated user could lead to a complete compromise of the affected system.
Who is most affected by this flaw?
This high-severity issue can disrupt numerous software projects, applications, and platforms. This flaw needs your immediate attention if cURL is anywhere in your stack.
- REST API Clients: if your application makes HTTP/HTTPS requests via cURL, it might compromise the data sent or received, posing a significant risk.
- Package Managers: Package managers employ cURL for remote package retrieval, and an exploit could manipulate these downloads, potentially resulting in various detrimental consequences, such as data exposure and remote code execution
- Web Scraping Tools: Many tools and libraries use cURL to retrieve web pages. This vulnerability could lead to exposure of sensitive information or RCE.
- Data Transfer in Microservices: if services communicate over HTTP/HTTPS, the flaw could be a critical weak link.
- IoT Devices: They often use cURL to interact with the web and the vulnerability can be used to compromise the devices
- Deployment Scripts: DevOps commonly employs automated deployment scripts using cURL to fetch software, configurations, and interact with internal REST APIs. Exploiting this flaw may jeopardize these processes.
- CI/CD Pipelines: CI/CD pipelines commonly rely on cURL commands for web interactions, and a successfully exploited vulnerability could disrupt the entire process.
- Cloud Services Interactions: If you employ cURL within a script to communicate with AWS S3, Google Cloud Storage, or other cloud service APIs, this vulnerability may lead to the exposure of sensitive data or access credentials.
- VPN Software: Certain VPN services employ libcurl for specific operations, and any exploitation could result in a breach of privacy or more severe consequences.
AFFECTED VERSIONS
Solution
CVE-2023-38545 vulnerability is patched in the cURL version 8.4.0. Updating to the latest version will mitigate the flaw. Following are the other things that can be proccesable:
- Do not use
CURLPROXY_SOCKS5_HOSTNAMEproxies with cURL - Do not set a proxy environment variable to socks5h://
How SanerNow detects and remediates this issue?
Detection – Identify the vulnerable packages in your Infrastructure by using the Vulnerability Management module of SanerNow.
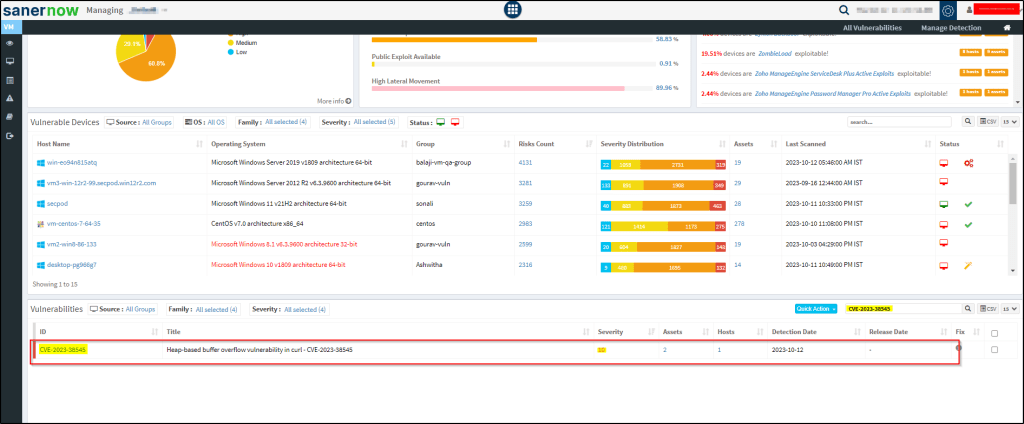
Mitigation
SanerNow is the best tool to remediate this vulnerability. Further, follow the below steps to mitigate it.
- Login to SanerNow platform
- Scan all your devices in your infrastructure
- Select the Vulnerability Management module and scroll down to the vulnerabilites category and search for CVE-2023-38545 in the search bar.
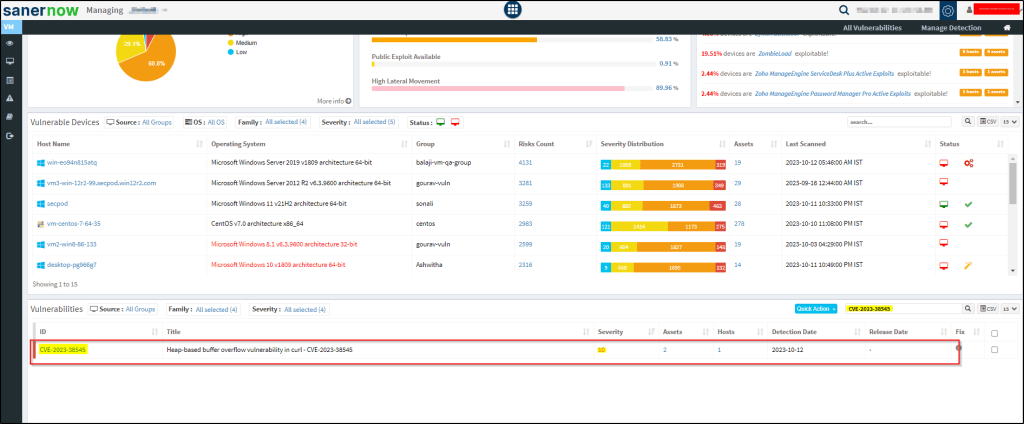
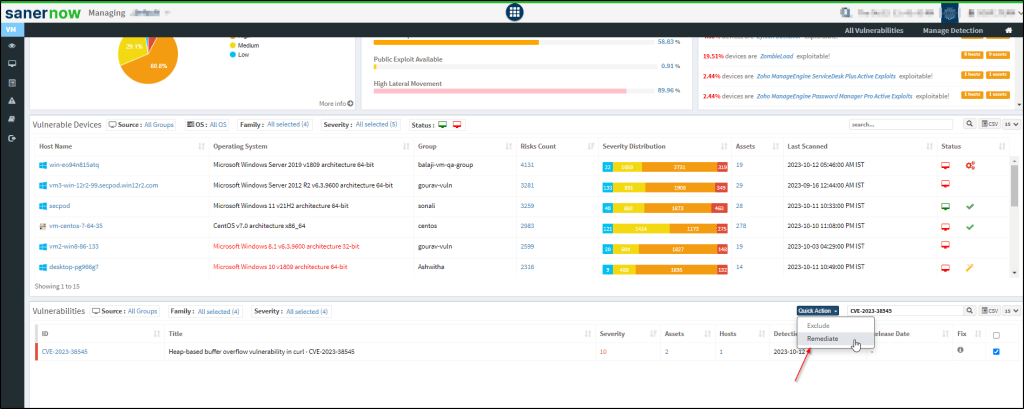
- Now, select the checkbox and click on quick actions, then remediate.
Have any questions on how to fix CVE-2023-38545 specific to your IT? Let’s discuss.

