Practicing Cyber Hygiene is worth it, making it much harder for hackers to succeed in infiltrating your system and reducing the damage they can cause to your personal as well as business information. Just as individuals take care of their health by following routine practices like handwashing to avoid infections, taking baths to stay clean, and maintaining Hygiene, organizations can safeguard their health by following certain cyber hygiene measures. A good vulnerability management tool helps you enforce security measures and elevate your Cyber Hygiene in various ways.
Our lives have been surrounded by technology for the past few decades, so ensuring proper cyber hygiene is a must. Cyber hygiene refers to the practices and precautions individuals and organizations take to safeguard their digital presence from cyber threats. From personal data protection to malicious attacks, adopting a proactive approach to cyber hygiene is essential. Timely patching of vulnerabilities using a patch management tool boosts your cyber hygiene score. Let’s review some cyber hygiene guidelines organizations can follow to improve their cyber hygiene score.
- Strong Passwords:
The foundation of good cyber hygiene is having strong, unique passwords for all your accounts. Utilize a mix of upper and lowercase letters, numbers, and special characters to create strong passwords. Avoid easily guessable passwords, such as names or birthdays. Using a password manager can be a game-changer, relieving you from the burden of remembering complex passwords while ensuring heightened security.
- Regular Software Updates:
Software updates often include patches for vulnerabilities. Neglecting them leaves your system exposed to potential threats. Set your devices and applications to update automatically or promptly install updates when notified. This simple step can make it difficult for cybercriminals looking to exploit outdated software.
- Multi-factor Authentication:
Adding an extra layer of protection, MFA requires users to verify their identity through multiple steps. This typically involves a combination of something you know (Password) and something you have (Smartphone for a verification code). Enabling MFA significantly reduces the risk of unauthorized access, even if your password is compromised.
- Continuously Manage Vulnerabilities:
We need to perform scans to identify vulnerabilities on a regular basis in the shortest time interval and consider having a vulnerability management tool that will manage these vulnerabilities. This process will minimize the surface exposure to services and applications as much as possible.
- Implement a strong automated backup system:
The first thing IT managers need to have cyber hygiene is to ensure that, even if something happens, the company will not lose work or important information for its operations. A well-planned approach, including secure backups and a website content migration plan, helps safeguard critical business data during transitions or system upgrades. With the increasing importance of IT, data risks, and market crashes, a manual backup routine is no longer enough for a secure business. Look for automated alternatives like good cloud services. This can light up your work and still free up time for the team.
- Regular Security Audits:
Conducting periodic security audits helps identify vulnerabilities in your digital ecosystem. Use top antivirus software to scan for malware and perform system checks. Additionally, stay informed about the latest cyber threats through threat intelligence sources, enabling your organization to adapt to emerging risks proactively.
- Employee Education and Awareness:
Educating employees about cyber vulnerabilities is necessary. Regular training sessions can empower your workforce to recognize and respond effectively to potential cyber threats. Cybersecurity awareness should be an ongoing initiative to ensure that your organization’s first line of defense, your employees, is well-equipped to handle evolving challenges.
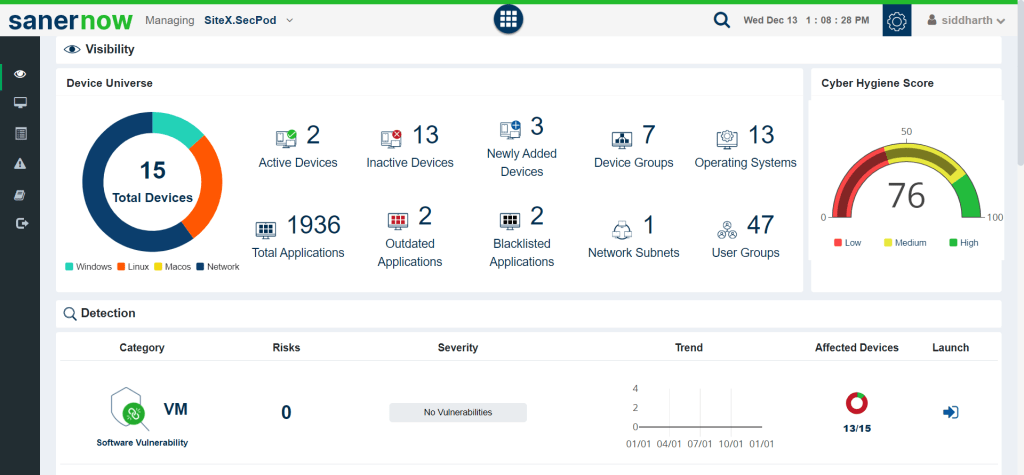
Conclusion:
In conclusion, improving the cyber hygiene score of your organization requires various approaches that involve both technological solutions and employee awareness. By prioritizing cybersecurity best practices, staying attentive against evolving threats, and maintaining a security culture, you can significantly enhance your organization’s resilience to cyber threats. Remember, cybersecurity is an ongoing effort that requires continuous adaptation to the ever-changing digital landscape.


