image credit: blogs.oracle.com
Oracle has released an out-of-band security update to address a critical oracle weblogic server deserialization RCE. A deserialization flaw allows remote code execution and tracked with CVE-2019-2729. Using a vulnerability scanning tool. Also, This vulnerability is rated critical and is found to be exploited in-the-wild.
The vulnerability exists due to a deserialization flaw in XMLDecoder in oracle weblogic server deserialization rce Web Services and is triggered by wls9_async and wls-wsat components in Oracle WebLogic allowing unauthenticated remote code execution. A patch management solution is critical to remediate these vulnerabilities. Also, This vulnerability published by researchers from the KnownSec 404 Team claiming that they were able to bypass the patch that issued in April (CVE-2019-2725). As per the researchers,
"a new Oracle WebLogic deserialization RCE 0day vulnerability was found and is being actively used in the wild. We analyzed and reproduced the 0day vulnerability, which is based on and bypasses the patch for CVE-2019–2725"
But, Oracle has clarified that although both CVE-2019-2725 and CVE-2019-2729 are deserialization issues, CVE-2019-2729 is a distinct vulnerability from CVE-2019-2725.
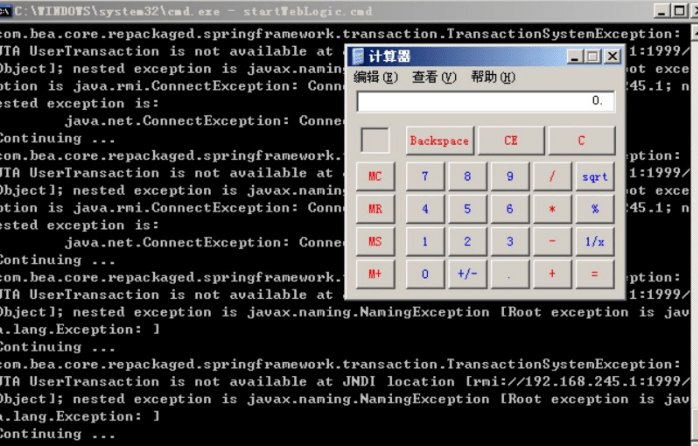
At the time of publishing this blog, no known PoC code was available for CVE-2019-2729. However, the KnownSec 404 Team reports seeing the exploitation of this vulnerability in the wild. They also posted an image of successful RCE exploitation achieved by exploiting this vulnerability.
image credit: medium.com
Affected Products:
The vulnerability affects these versions of the application:
- Oracle WebLogic Server 10.3.6.0.0
- Oracle WebLogic Server 12.1.3.0.0
- Oracle WebLogic Server 12.2.1.3.0
Impact:
An attacker can run arbitrary code in the context of the affected application.
Solution:
The Oracle WebLogic patches are available only for customers. However, Please advised to download the patch from Oracle portal and install. SanerNow’s software deployment capability used to install executable/scripts.
Oracle strongly recommends that customers apply the updates provided by this Security Alert as soon as possible
Mitigation:
Two mitigations are available:
- If components wls9_async_response and wls-wsat not applied in the WLS cluster, find and delete wls9_async_response.war, wls-wsat.war and restart the WebLogic service.
- Control URL access for the /_async/* and /wls-wsat/* paths by access policy control.